FileFrozr Ransomware
The FileFrozthe R Ransomware is a ransomware Trojan written using C#. The FileFrozthe R Ransomware seems to be part of a RaaS (Ransomware as a Service) scheme that is located on the TOR network onion site frozrlockqqxz7a2.onion. The FileFrozthe R Ransomware is being promoted on various underground forums. Con artists use threats like the FileFrozthe R Ransomware to lock the victims' data and offer their help at a lower price than many other Trojans available. Con artists can build their own customized version of the FileFrozthe R Ransomware for $100 USD, or 0.09 BitCoin at the current exchange rate.
Table of Contents
How the FileFrozthe R Ransomware may be Delivered
Con artists wanting to purchase the services of the FileFrozthe R Ransomware builder would connect to this TOR website and pay a fee to gain access to the ransomware Trojan. Once they do this, they can customize the FileFrozthe R Ransomware to release and distribute it using their own methods. According to the creators of the FileFrozthe R Ransomware, this ransomware Trojan does not use an open source code, unlike many ransomware Trojans available currently, and the Trojan itself is self-sufficient. Con artists receive the FileFrozthe R Ransomware payload in the form of an obfuscated package, which prevents distributors or researchers to decode the FileFrozthe R Ransomware's code to prevent attacks or reverse engineer the code to create their own versions of the FileFrozthe R Ransomware. There are many ways in which threats like the FileFrozthe R Ransomware can be distributed, including corrupted email attachments or hacking into computers and networks through poorly protected RDP (Remote Desktop Protocol) accounts or other access points directly. Once the files have been encrypted in the FileFrozthe R Ransomware attack, they become inaccessible without the decryption key, which the FileFrozthe R Ransomware's creators hold in their possession.
How the FileFrozthe R Ransomware Attack Works
The FileFrozthe R Ransomware RaaS provides con artists with a customized version of the FileFrozthe R Ransomware. Con artists can then use whatever distribution method they prefer to deliver the FileFrozthe R Ransomware to their victims. The FileFrozthe R Ransomware threat itself is designed to encrypt more than 250 different file types. Once the FileFrozthe R Ransomware enters a computer, it uses a strong encryption algorithm to make the files inaccessible completely. The FileFrozthe R Ransomware will target commonly used file types associated with media and documents, as well as specific file types created by software such as Photoshop or AutoCAD. The people responsible for the FileFrozthe R Ransomware also can customize it to rename the encrypted files, marking them with a specific file extension to identify them during the attack. After the FileFrozthe R Ransomware attack has encrypted the victims' files, the FileFrozthe R Ransomware will deliver a ransom note, which the RaaS also allows the cyber crooks to customize. These ransom notes will demand payment of a ransom, between 0.2 and 5 BitCoins, depending on the extent of the attack. The people responsible for the FileFrozthe R Ransomware RaaS handle all payment processing and updating the FileFrozthe R Ransomware Trojan itself, keeping a percentage of the ransom profits as payment. It is likely that the controllers of the FileFrozthe R Ransomware RaaS keep a large percentage of the attack profits. In some cases, the percentage kept by these people could be as high as 60%, but it may average between 30% and 40% of the profits.
Protecting Your Computer from the FileFrozthe R Ransomware Attacks
The FileFrozthe R Ransomware attacks are not very different from many other Trojans. The files encrypted by the FileFrozthe R Ransomware cannot be recovered without the decryption key. Because of this, computer users will need to restore the affected files from a backup copy. In fact, this is the best protection against threats like the FileFrozthe R Ransomware. PC security researchers advise computer users to have backup copies of their files to protect themselves from the FileFrozthe R Ransomware attacks. This is the best type of protection against encryption ransomware since the extortionists lose their edge if the victims can simply restore the affected files from a backup copy.
SpyHunter Detects & Remove FileFrozr Ransomware
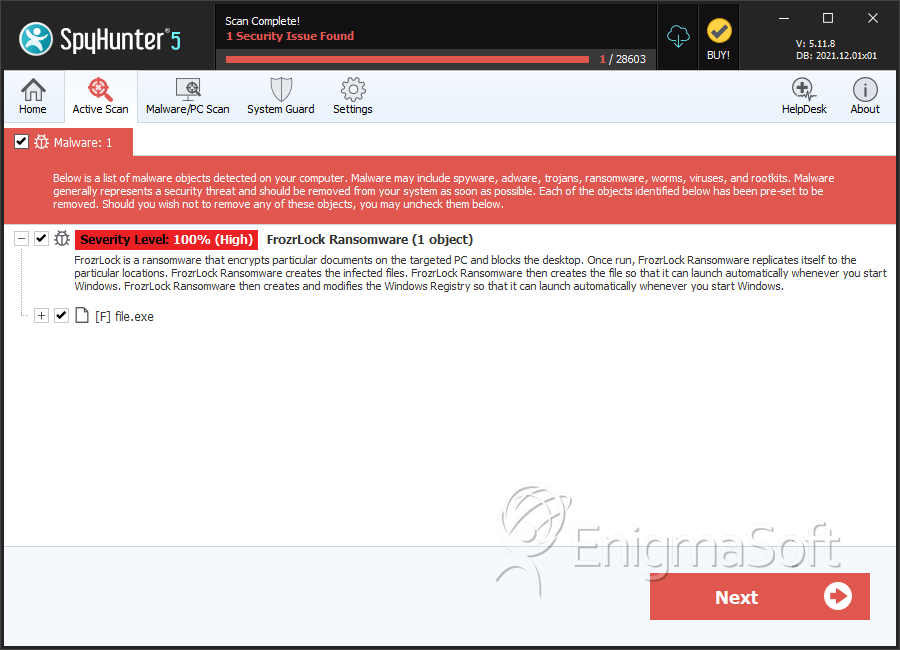
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 25abae5e16daf9795952e0195f7c7f7b | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.