FakeSysDef
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 71 |
| First Seen: | March 18, 2011 |
| OS(es) Affected: | Windows |
The FakeSysDef family of rogue defragmenter programs is a dangerous group of fake security applications that forms part of a well-known online scam. What makes the FakeSysDef family of rogue defragmenter programs particularly dangerous is that they will usually be associated with a Master Boot Record (MBR) rootkit, such as TDL4 that can be quite difficult to remove. Malware analysts have been keeping track of malware in the FakeSysDef family of rogue defragmentersecurity programs since 2010. Some examples of the dozens of clones of FakeSysDef rogue security programs include System Recovery, WinHDD, Windows Fix Disk, Windows 7 Recovery, Windows Diagnostic, Windows Disk, Windows Repair, Windows Recovery, Windows Safe Mode, and System Repair. Despite their names, make no mistake about it, rogue security programs from the FakeSysDef family are not connected in any way with Microsoft or with any kind of legitimate security application. These fake security programs are designed to take over your computer system until they managed to scam you and take your money. Rogue defragmenter programs fromthe FakeSysDef family will often continue to profit from the infected computer by using the included Master Boot Record rootkit.
Table of Contents
How the FakeSysDef Scam Works
Most of the rogue defragmenter programs in the FakeSysDef family follow the same basic premise in order to scam their victims. Programs in the FakeSysDef family pretend to be legitimate defragmenters or system optimization utilities. After invading the victim's computer system with the aid of a dropper Trojan and common Trojan delivery methods, rogue defragmenter programs from the FakeSysDef family will pester the victim with a constant stream of error messages, fake system alerts and pop-up notifications. Rogue defragmenter programs from the FakeSysDef family pretend to run a system scan (which is nothing more than an animation) and then display a list of alarming problems on the infected computer. Many of these problems, such as failure to detect a hard drive or extreme CPU overheating are impractical and even laughable in most cases. However, the technical language in the alerts may be enough to alarm inexperienced or gullible computer users. The next step in the FakeSysDef scam involves convincing the computer user that a "full version" of the rogue security program in question is needed. The victim is taken to a website where he/she will then enter his/her credit card information. ESG security researchers strongly recommend against paying for any of the rogue defragmenter programs. This family of fake security programs has absolutely no way of fixing a hard drive, optimizing your system or removing malware. Once a "full version" of this dangerous malware is purchased, all the victim will receive in exchange will be a rootkit infection and the chance of identity theft or credit card fraud.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AntiVir | SPR/Tool.573440.11 |
| BitDefender | Application.Generic.351675 |
| AVG | Generic4.BASC |
| Ikarus | Gen.Variant.Tdss |
| McAfee-GW-Edition | Heuristic.BehavesLike.Win32.Packed.D |
| AntiVir | ADSPY/AdSpy.Gen2 |
| DrWeb | Trojan.Searcher.225 |
| F-Prot | W32/Zwangi.C.gen!Eldorado |
| K7AntiVirus | Adware |
| Panda | Trj/CI.A |
| BitDefender | Trojan.Generic.KDV.164004 |
| Avast | Win32:FakeSysdef-EB |
| NOD32 | a variant of Win32/Kryptik.LVS |
| AhnLab-V3 | Trojan/Win32.Hiloti |
| Comodo | MalCrypt.Indus! |
SpyHunter Detects & Remove FakeSysDef
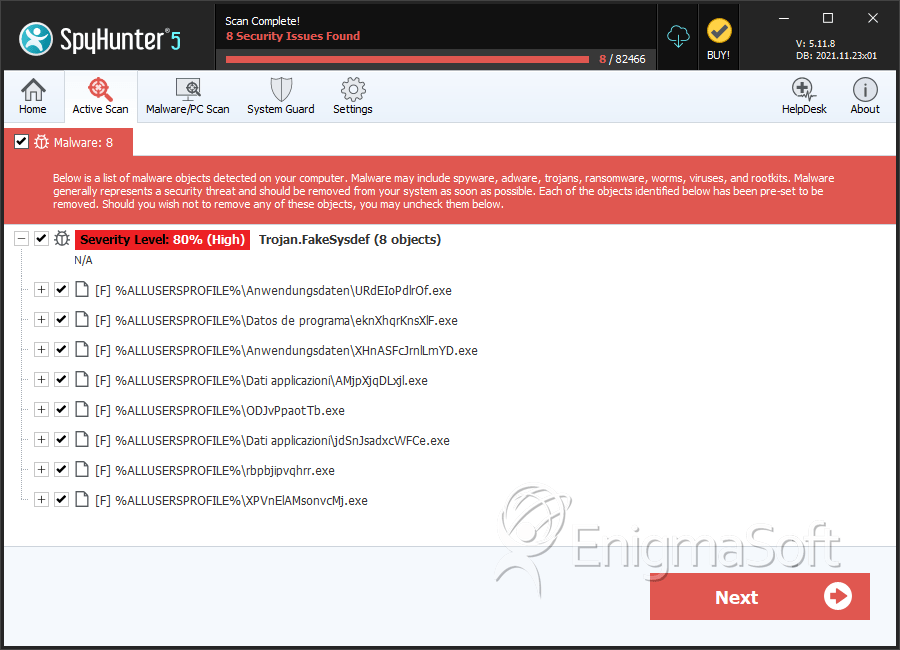
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | SSFdrVXAOXpQ.exe | 4a342010e7135680d5af24955d907c38 | 31 |
| 2. | questbrwsearch.dll | 80c2efe7728d7778e8eb1d71edc021b2 | 9 |
| 3. | msn.exe | 30a50d02b42698f9526eef00fc49f09e | 7 |
| 4. | EAGueaRwrDlOoPP.exe | 7bf705d074223fdcd2ac7d64903c3149 | 6 |
| 5. | gTqujgchSFYWU.exe | f8998757f8138bd3d9283948545b2647 | 5 |
| 6. | arking.exe | fa5347dc734dac4e3cadb455442289c5 | 4 |
| 7. | EAGueaRwrDlOoPP.exe | 11f07625d1fccff9e64905f4a6bbeba0 | 2 |
| 8. | gGloYwWdPuRr.exe | 2c6a70f5886124a22c0970db141e6969 | 2 |
| 9. | resultbar.dll | 231a8fa441de76f622580f17cb907fbe | 1 |
| 10. | mapionir.dll | 17bfc74909aea4e45b752b16e31aabac | 1 |
| 11. | s0WPDCe.dll | 5f4978a6764b73e25447272dae73853e | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.