FakeRean
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 18,004 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 9,842 |
| First Seen: | November 30, 2010 |
| Last Seen: | January 29, 2026 |
| OS(es) Affected: | Windows |
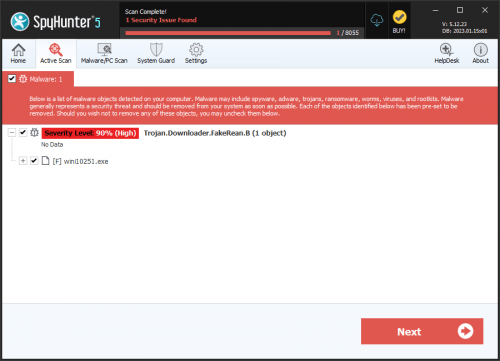
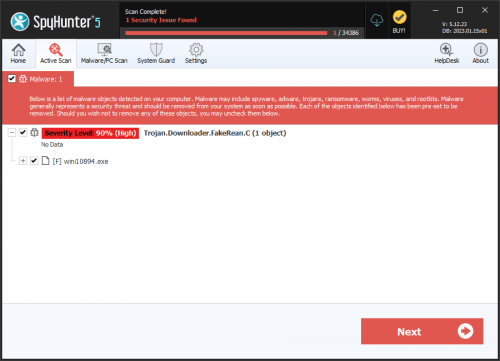
FakeRean is a Trojan that is usually included and spread as an email attachment similar to ZBot. Spam messages are successful with spreading FakeRean by including an executable called "install.exe" within a zip archive. If a computer user downloads the ZIP file and runs the "install.exe" file, then they their system will be infected with the FakeRean Trojan horse. FakeRean can cause damage to a computer’s system files and prove difficult to manually detect and remove in some cases. FakeRean is also known as W32/FakeAV.AE!genr, W32/FakeRean.A.gen!Eldorado or TrojanDownloader:Win32/FakeRean.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Cryptic.EOS |
| Fortinet | W32/Jorik_Fraud.SRX!tr |
| Ikarus | Trojan.Win32.Loktrom |
| AntiVir | TR/Symmi.176421 |
| Kaspersky | Trojan.Win32.Jorik.Fraud.srx |
| AVG | Crypt.BXIV |
| Fortinet | W32/Generic!tr |
| McAfee | Fake-Rena-FMB!D3516C44B50F |
| AVG | Generic30.BBID |
| Kaspersky | Trojan-FakeAV.Win32.CProtection.aih |
| Symantec | Trojan.Winlock!gen1 |
| Fortinet | W32/Generic.GPL!tr |
| AntiVir | TR/Fake.Rean.776 |
| Sophos | Troj/FakeAV-GOU |
| McAfee | Fake-SecTool-FLM!B7B9041FC273 |
SpyHunter Detects & Remove FakeRean
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | msecurity.exe | d35d56ba42a7b32196ff263fb79e3cad | 5 |
| 2. | security_cleaner.exe | 635515dd37ff62f238920eacaf91e233 | 4 |
| 3. | pnj.exe | ae7d35206e33efa128fed3ab03f25cd9 | 3 |
| 4. | nek.exe | 632d67b553428b93204f7457472f3972 | 3 |
| 5. | ndr.exe | c4f2c5841f26525a899a53b0c12d7bb3 | 2 |
| 6. | fmb.exe | 3c29d43a0f4f4803fd1fb1866bf46cbd | 2 |
| 7. | exr.exe | 70d574b7f24bd23467d2188377025039 | 2 |
| 8. | fap.exe | 20167cba152bdc52965a84b488d05627 | 2 |
| 9. | erv.exe | f61e2a0ad9d5e04ab1baca8399ecfd18 | 2 |
| 10. | pdh.exe | 82be0d41ee155bfcf919f8a5ded9c6d4 | 2 |
| 11. | wwe.exe | 7df15ed96ced549d4ddd5a388b8505e0 | 2 |
| 12. | av.exe | 0bc5e06b4fe42bbdde18b534ec8feb91 | 2 |
| 13. | tlf.exe | fd965a0be37382bc83ebfcb8a7ba3e52 | 2 |
| 14. | dow.exe | 9bd2bc135683525822d1c251d4959847 | 2 |
| 15. | drw.exe | 529b489bb3eb8232f87318b8bb3e3ba3 | 2 |
| 16. | bcq.exe | 8b8585f8d64dd6383dcf8dbbf49621be | 1 |
| 17. | qwu.exe | f0e50738e85f8db4787130b4823e1906 | 1 |
| 18. | aak.exe | 4da1e82ba52f7050757fa2104b14c87e | 1 |
| 19. | sve.exe | 61e91f6e0cd4b05e2701fdd4c048bd47 | 1 |
| 20. | jqq.exe | 8657d274e17a0936704365288e8d04f8 | 1 |
| 21. | qnb.exe | 802c064f0ba701e499dd0605e218a5e4 | 1 |
| 22. | bll.exe | f8b7849c7ac2b3c850332b78b2f0189f | 1 |
| 23. | ljo.exe | 4c33f7dfd6dc5f684e60f9e019e7c180 | 1 |
| 24. | snf.exe | 99569cebc1f721ff66217699808230bc | 1 |
| 25. | bvk.exe | 3958bb38562dee3cc0ae35d4220aa627 | 1 |
| 26. | yna.exe | 3f9ef3cef499dd435d7b86d74ea838bb | 1 |
| 27. | kfk.exe | 433f01b5642c37016588f11ee5485519 | 1 |
| 28. | 8814206.exe | 86562961e94a757cb37576d2a955c06b | 1 |
| 29. | amsecure.exe | d3516c44b50fabd3ba2636e54ff172d1 | 1 |
Analysis Report
General information
| Family Name: | Rogue.FakeRean |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
0604af7c52911b648819277aa11e2872
SHA1:
38b24c6e11a0e5a8d9dc7ef4dead9399d96543e7
SHA256:
B599512AF4A79C574D397B1F3AD319B5912FD86C00F3C57A2224EA6D540FD11F
File Size:
393.22 KB, 393216 bytes
|
|
MD5:
e3cb47ea02d2ff4cec014a3e4be1004e
SHA1:
f240b4ed11c4a0e44876ce1185ddfebf7e5df0f2
SHA256:
A41A998C482BA943BDCBE019AD9115C0D4BBA64D25CEF19B5377F99A437C2072
File Size:
2.79 MB, 2786304 bytes
|
|
MD5:
7684c3746b315e2ba8768771f8c88a0d
SHA1:
b558fd80a32aef34ad0d1f408bf9afca62016651
SHA256:
12A24B74AF1C7C3F73382B10EC08C1FB10A4ABFF049E9DB425EDFE47A295FB15
File Size:
1.82 MB, 1818624 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has TLS information
- File is .NET application
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version | 1.0.0.0 |
| Comments | MBM Converter |
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright | Copyright © Luxtron 2010 |
| Legal Trademarks | Cequenze Technoloy Inc. |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- .NET
- vb6
- x86
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\windows\appcompat\programs\amcache.hve | Read Data,Read Control,Write Data |
| c:\windows\appcompat\programs\amcache.hve | Write Attributes |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| User Data Access |
|
| Anti Debug |
|
| Process Shell Execute |
|
| Encryption Used |
|
| Process Manipulation Evasion |
|
| Other Suspicious |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\Windows\Microsoft.NET\Framework64\v2.0.50727\\dw20.exe dw20.exe -x -s 824
|