Executioner Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 21 |
| First Seen: | June 7, 2017 |
| Last Seen: | March 23, 2023 |
| OS(es) Affected: | Windows |
The Executioner Ransomware is a ransomware Trojan that was first observed on June 6, 2017. The Executioner Ransomware delivers its ransom note and attack in English and seems to be delivered to victims through corrupted email attachments sent in spam email messages. Most of the Executioner Ransomware attacks and their associated spam email campaign are targeting computer users in Western Europe and North America. There is little to differentiate the Executioner Ransomware from most encryption ransomware Trojans that are active currently. As with most ransomware Trojans, the goal of the Executioner Ransomware attack is to encrypt the victims' files and then demand the payment of a large ransom in exchange for the decryption key or software necessary to recover the affected files. In essence, the Executioner Ransomware takes the victim's files hostage and then demands the payment of a ransom.
Table of Contents
The Executioner Ransomware and Other Encryption Ransomware Trojans
New versions of ransomware Trojans like the Executioner Ransomware are released every day. The Executioner Ransomware represents a threat to computer users and their data. Because of the high number of ransomware Trojans being distributed currently, it is more needed than ever that computer users protect their data with the help of a reliable, fully updated anti-malware application. Since the Executioner Ransomware and other ransomware Trojans may be delivered through the use of corrupted spam email attachments, take steps to ensure that this content does not reach your computer and learn to handle these messages if they happen to make it past your anti-spam filter.
How the Executioner Ransomware Executes Its Attack
The Executioner Ransomware is very similar to other ransomware Trojans targeting computer users in Turkey released recently. The Executioner Ransomware will search for the user-generated files such as those created with software such as Windows Photo, Microsoft Office, Adobe Acrobat, etc., as well as media files, which may include video, audio, images and various others. The Executioner Ransomware will use a strong encryption algorithm to make its victim's files unreadable. The Executioner Ransomware will deliver a ransom note once the victim's files have been compromised. The Executioner Ransomware delivers its ransom note in the form of an HTML file named 'Sifre_Cos_Talimat.html' written in Turkish. Below is a translation into English of the Executioner Ransomware's ransom note text:
'READ THIS!
YOUR FILES HAVE BEEN ENCRYPTED BY the Executioner Ransomware !!!
TEXT, PHOTOGRAPHS, AUDIO IN YOUR COMPUTER AND OTHER IMPORTANT FILES !!
YOU NEED DECRYPTION SOFTWARE TO RECOVER THE FILES
NOTE: DO NOT CLOSE THE WINDOW
OR YOU WILL NOT RECOVER YOUR FILES!
BUY SOFTWARE?
THE PRICE IS $ 150 BITCOIN
ID NUMBER: [RANDOM CHARACTERS]
THEN YOU WRRITE AN EMAIL INCLUDING YOUR ID
DO NOT RENAMED FILES AND CHANGE THEIR SIZE
GOOD LUCK!
Mail:executioner.ransom@protonmail.com
EXECUTIONER'
Protecting Your Data from the Executioner Ransomware and Similar Ransomware Trojan
The files encrypted in the Executioner Ransomware attack will have random extensions and text strings added to their names frequently. Computer users should refrain from contacting the people responsible for the Executioner Ransomware attack or paying the ransom amount. Instead of doing this, take steps to protect your data from this and other attacks. The most effective way of ensuring that your data is safe from the Executioner Ransomware and other encryption ransomware Trojans is to have a reliable backup system. If you can recover your files by copying over from a backup copy in the cloud or a mobile memory device, then the people responsible for the Executioner Ransomware attack lose any power that allows them to demand a ransom payment from you. In fact, once enough computer users have backup copies of their data, then attacks like the Executioner Ransomware will become obsolete and will die off. Apart from file backups, you should have a reliable security program that you can trust.
SpyHunter Detects & Remove Executioner Ransomware
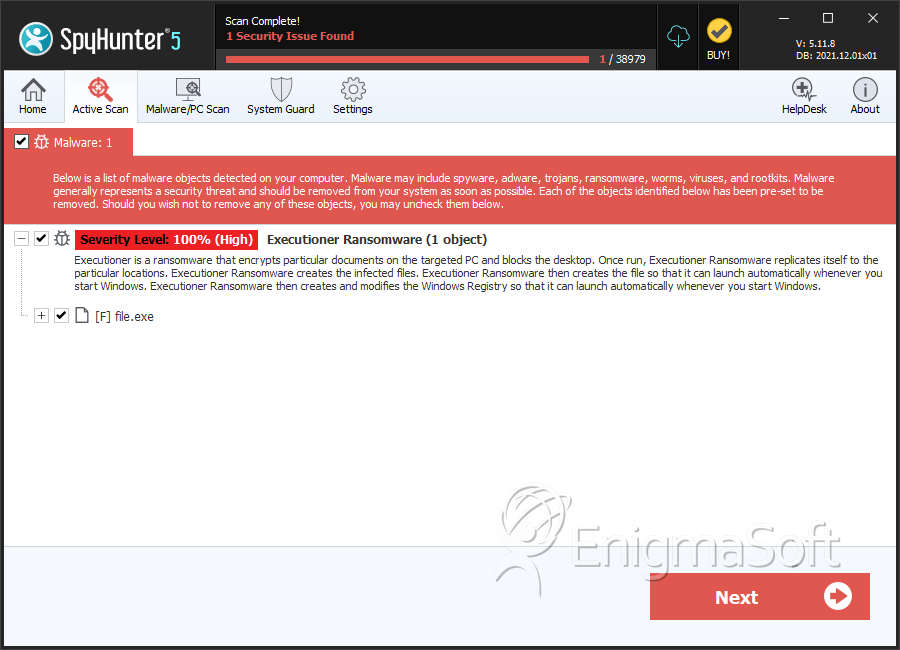
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | eec4f84d12139add6d6ebf3b8c72fff7 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.