Enjey Crypter Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | March 8, 2017 |
| Last Seen: | June 5, 2018 |
| OS(es) Affected: | Windows |
The Enjey Crypter Ransomware is a ransomware Trojan. The Enjey Crypter Ransomware carries out a typical ransomware attack, which involves encrypting the victims' files and then demanding the payment of a large ransom in exchange for the decryption key. These attacks have become quite common in the last few years because of their irreversible nature; once the victim's files have been infected, even if the Enjey Crypter Ransomware infection itself is removed, the files will remain compromised. The files encrypted during the Enjey Crypter Ransomware attack are simple to identify because the Enjey Crypter Ransomware will add the extension '.enjey' to the files' names.
Table of Contents
The Infection Method Used by the Enjey Crypter Ransomware
There are numerous ways in which the Enjey Crypter Ransomware could spread. However, the most common is the use of corrupted email attachments contained in spam email messages. The Enjey Crypter Ransomware can be spread using social media websites or file sharing networks. It is important to treat all content downloaded from the Web with caution and be especially cautious when it comes to unsolicited email messages. A reliable security application that is fully up-to-date also can help computer users ensure that the Enjey Crypter Ransomware is not installed on a computer.
Once the Enjey Crypter Ransomware enters the victim's computer, it makes changes to the Windows Registry that allows it to maintain persistent, running automatically when Windows starts up. The Enjey Crypter Ransomware will then scan the victim's drives in search for files to encrypt in its attack. The Enjey Crypter Ransomware will use a strong encryption method to make the victim's files inaccessible completely. The Enjey Crypter Ransomware will then drop a ransom note in the form of a text note named 'README_DECRYPT.txt,' which includes the following text:
'//============================================= [ ENJEY CRYPTER ] =============================================\
Hello, your personal identity:
All of your documents, photos, databases and other important data has been encrypted.
To get a decoder, please contact me by e-mail: contact_here_me@india.com
In the message write the following: ‘ ‘ Hey, I need a decoder + your personal identifier ‘ ‘
You will receive Bitcoin wallet, which will need to pay.
If you have no Bitcoin wallet
– Create a Bitcoin wallet https://blockchain.info/wallet/#/signup~~dobj
– Buy cryptocurrency.
– Https://en.bitcoin.it/wiki/Help:FAQ (for beginners),
Attention!
– Do not try to do something on their own, you can lose all your data!
– Do not rename all files are encrypted!
\>//============================================= [ ENJEY CRYPTER ] =============================================//'
PC security researchers strongly advise computer users against paying the ransom amount or following the instructions contained in this ransom note. In its attack, the Enjey Crypter Ransomware will encrypt a wide variety of file types, including the following:
.7z, .bmp, .doc, .docm, .docx, .html, .jpeg, .jpg, .mp3, .mp4, .pdf, .php, .ppt, .pptx, .rar, .rtf, .sql, .tiff, .txt, .xls, .xlsx, .zip.
Dealing with the Enjey Crypter Ransomware Infection
Paying the ransom demanded by the people responsible for the Enjey Crypter Ransomware is not recommended because it allows these con artists to continue creating ransomware threats and affecting other computer users. Apart from this, there is no guarantee that these con artists will follow through and provide the decryption key after the ransom is paid. In many cases, the con artists will ignore the payment or ask for more money from the victim.
The Enjey Crypter Ransomware can be removed with the help of a reliable security program that is fully up-to-date easily. However, even if the Enjey Crypter Ransomware is removed, the victim's files will remain encrypted. Because of this, the best protection against ransomware threats like the Enjey Crypter Ransomware is to have backup copies of all files. System administrators, who may encounter these threats regularly, should have backup images of their files, as well as cloud storage. Computer users also should ensure that they have backup copies of their files on an external memory device or the cloud.
SpyHunter Detects & Remove Enjey Crypter Ransomware
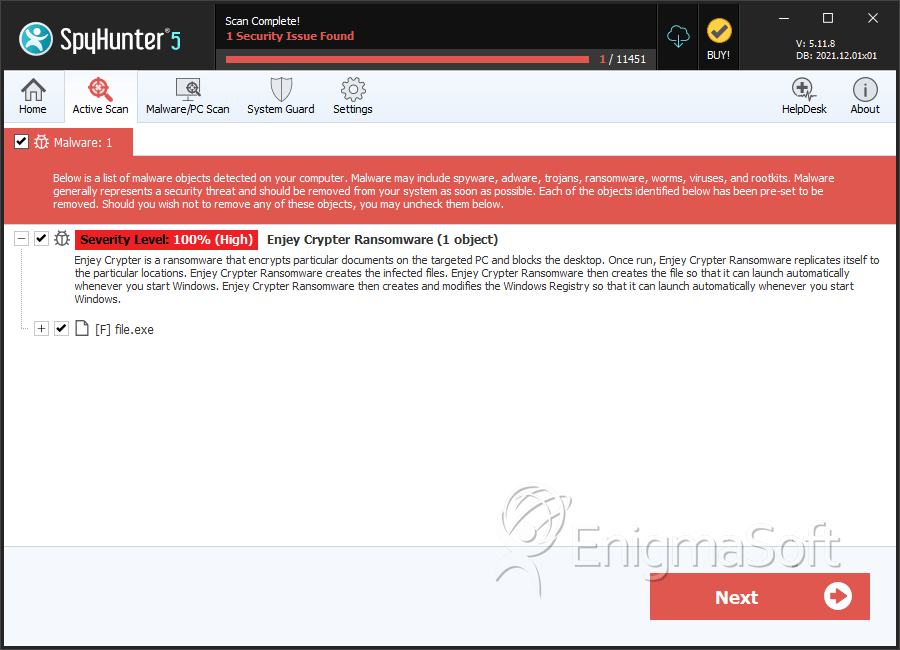
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | c92b209d85d866b40365ca5723e079ee | 2 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.