DoubleGuns Botnet
The DoubleGuns Botnet is an operation that appears to be exclusively targeting Chinese users. Around the peak of the activity of the DoubleGuns Botnet, there were 100,000 infected systems approximately. Over time the DoubleGuns Botnet has been used to deliver different payloads, which led malware analysts to suspect that the creators of this project may be offering the services of the botnet to cybercriminals who are willing to pay them.
It would appear that the DoubleGuns Trojan is distributed via a fake copy of a pirated game. The game in question was promoted on different Chinese social media platforms and forums. The number one goal of the DoubleGuns Botnet is to collect sensitive login credentials from victims. To do this, it would plant different malware types that would run as a corrupted driver or a rootkit, allowing them to be silent and persistent. Although attackers could get their hands on any login data, they appear to prioritize credentials for gaming platforms like Battle.NET, Steam, and others. This botnet also can be utilized for click-fraud. The DoubleGuns Botnet can plant advertisements in the users' Web browser and trick them into engaging with the ads. It also can take over the users' QQ account and send spam messages to everyone on their contacts list. The DoubleGuns Botnet also can redirect its victims whenever they try to open certain online stores.
Chinese malware experts have been able to determine the technique used in the communication between the botnet and the operators, which allowed them to disrupt the DoubleGuns operation. The attackers were using a specific image hosted on a service called Teiba – all the compromised devices would download the image in question. This image contained the instructions set up by the attackers. Even though the images linked to the DoubleGuns Botnet activity have been taken down, the operators of this project are not likely to give up on this operation, and we may see a come back in the near future.
What is DoubleGuns?
DoubleGuns has been active since July 2017, when Qihoo researchers found the first samples in the wild. Within three years, DoubleGuns changed little but grew in the scale of infections. The malware is still spread through malware-laced apps shared on Chinese websites. Most of those include pirated games on Chinese social networks and gaming forums. The primary purpose of the malware was to infect users with MBR and VBR bootkits, malicious drivers and to steal credentials from local apps, including Steam accounts. DoubleGuns may also act as adware and a spam module. It inserts ads on devices and hijacks QQ accounts, spreading ads to the victim's friend list through private messages.
Older versions of DoubleGuns were also seen hijacking traffic from e-commerce portals and redirecting users to fake websites, but that capability was dropped in later versions. The botnet is targeting Chinese users since the functions behind it are aimed at disabling most Chinese antivirus products.
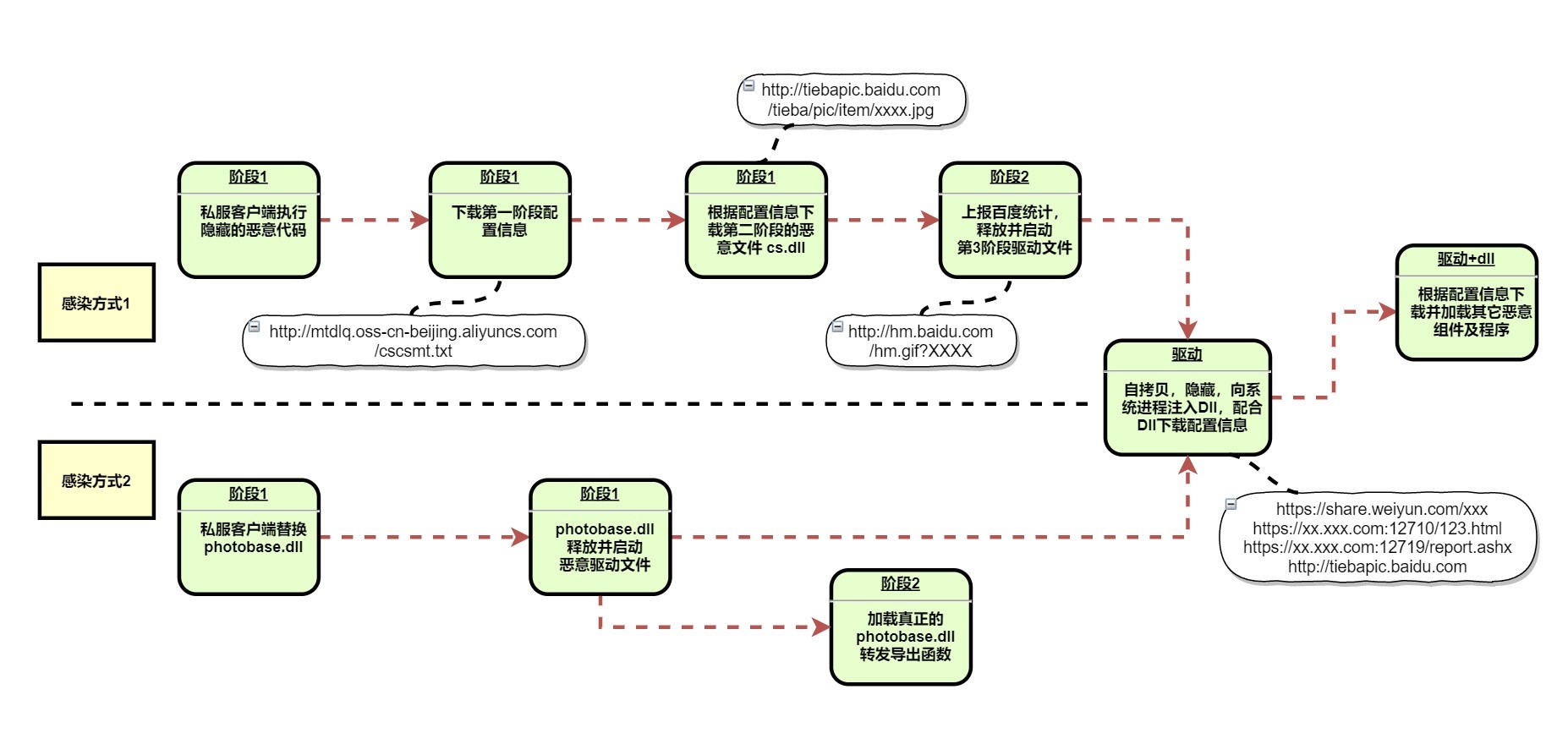
The DoubleGuns infection flow. Source: Netlab 360
How DoubleGuns Works
The file cs.dll is hidden in files hosted on Baidu Teiba. The images contain separate malicious code data and image data, with the key string in the file also using a customized DES encryption. That is similar to other DoubleGun samples the researchers found before.
Cs.dll performs countermeasures for virtual machines and anti-software, using the Baidu statistics service to report bot information to its C2 server, according to researchers. It uses the system API to create a bot ID on the host and writing it in the registry as 'SOFTWARE\PCID.'
Once the Bot ID is established, the botnet operators used fields within the Baidu statistics interface to keep track of the host's data. Many websites use the Baidu statistical service, so it is difficult to distinguish it, making it harder for security vendors to see and take action, according to local researchers. The interface allows the botnet operators to upload statistics scripts, Bot ID, user cookies, and other information so they can assess and manage the infected machines.
A third stage driver is also deployed, one that fetches configuration information, obfuscating itself with a DES encryption. Once the decryption is complete, the configuration information was noticed to use a custom format. All configuration information returned by the driver samples contained a Tencent Weiyun address. The researchers believe that is a strategy that dynamically generates configuration file server addresses, possibly still in a development stage.
Once the malware is installed, the operators hijack system processes and download more malicious programs. The DLL obtains the configuration server information by calling the driver. The downloaded configuration files showed that it goes to Baidu Tieba to download more malicious code and to carry out the next step of its malicious activities.

