DCRTR Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 9 |
| First Seen: | February 15, 2018 |
| Last Seen: | September 17, 2019 |
| OS(es) Affected: | Windows |
The DCRTR Ransomware is an encryption ransomware Trojan that was first observed in early February 2018. The DCRTR Ransomware is mainly being delivered to victims through the use of corrupted email attachments. Affected computer users will receive a spam email message, which uses phishing tactics and social engineering to trick the victim. The email attachment will often include damaged macro scripts that download and install the DCRTR Ransomware onto the victim's computer.
Table of Contents
How the DCRTR Ransomware Attacks Your Machine
Once the DCRTR Ransomware has been installed, it will begin encrypting the user-generated files. The DCRTR Ransomware will search for certain file types, using a strong encryption algorithm to make all files with a targeted file extension that are smaller than 100 MB unusable. The DCRTR Ransomware will avoid the Windows system files and applications (since it requires the victim to be able to use the infected computer to carry out a ransom payment). The following are some of the file types that are typically targeted in these attacks.
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The DCRTR Ransomware will rename the files encrypted by the attack by adding the string '{LAMA}' to the files' names and the '.dcrtr' extension to the end of each file's names. The DCRTR Ransomware will often include the contact email used by these people to the file extension appended to each file's name.
The DCRTR Ransomware’s Ransom Note
The DCRTR Ransomware delivers its ransom note in a text file named 'ReadMe_Decryptor.txt.' This note is dropped onto the victim's computer's desktop. The following is the text of the DCRTR Ransomware's ransom note:
'All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail decryptor@cock.li
In case of no answer in 24 hours write us to theese e-mails: masterdecrypt@openmailbox.org
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
h[tt]ps://localbitcoins[.]com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
h[tt]ps://www.coindesk[.]com/information/how-can-i-buy-bitcoins'
PC security researchers strongly advise computer users to refrain from following the instructions in the DCRTR Ransomware's ransom note. Rather than following these instructions, PC security researchers advise computer users to use a reliable security program that is fully up-to-date to remove the DCRTR Ransomware infection completely. Once the DCRTR Ransomware infection has been removed, PC security researchers advise computer users to restore the compromised files by replacing them with backup copies. Having file backups stored on the cloud or an external memory device is the best protection against ransomware threats like the DCRTR Ransomware and the countless other ransomware variants that are being used to attack computer users currently.
SpyHunter Detects & Remove DCRTR Ransomware
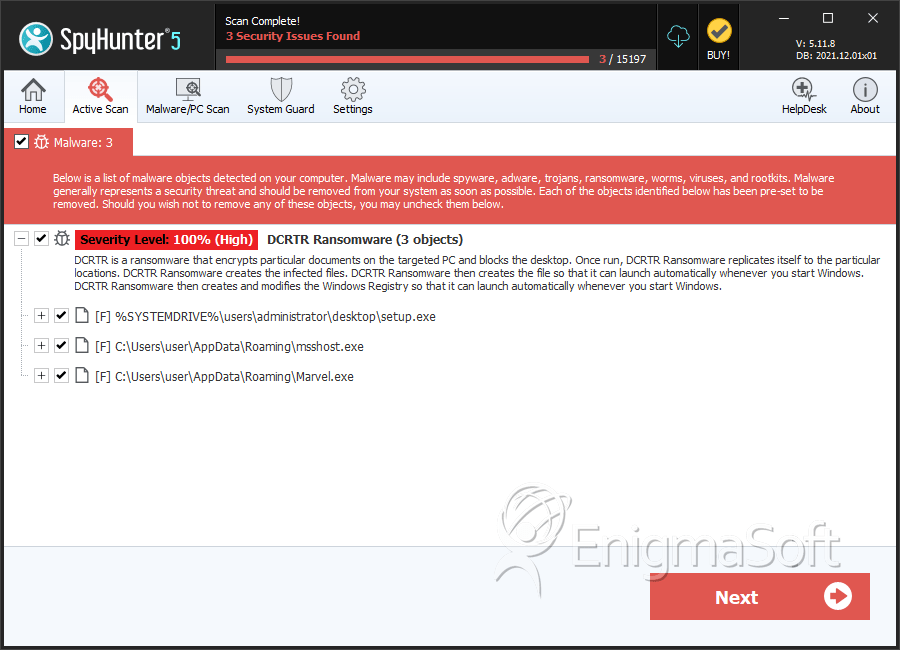
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | setup.exe | 3e2f03caf12e820104a816bc347ffcc8 | 4 |
| 2. | msshost.exe | 08945d816ef948fa28ecbf0791ccb061 | 1 |
| 3. | Marvel.exe | 96c3139f571a36a1e8968208d40a4fc1 | 1 |

