CryptoViki Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | May 16, 2017 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
The CryptoViki Ransomware is part of a large family of ransomware that is growing rapidly. Like many other ransomware Trojans, the CryptoViki Ransomware may be delivered to its victims through the use of spam email attachments. Once the CryptoViki Ransomware enters a computer, it will encrypt the victim's data systematically. The CryptoViki Ransomware does this to demand a ransom payment from the victim in exchange for the decryption key that is needed to recover the affected files. Effectively, ransomware Trojans like the CryptoViki Ransomware take the victims' files hostage and then extort the victims, demanding a large ransom. Although it is still not clear who is responsible for the CryptoViki Ransomware attack, there are clear relationships between the CryptoViki Ransomware and other recently released ransomware Trojans.
Table of Contents
How the CryptoViki Ransomware Attacks a Computer
Victims of the CryptoViki Ransomware infection may first receive an email message with an attachment or embedded link, often using some social engineering tactic to trick the victim into opening the attached content. When the victim does this, the macros in the attachment will download and install the CryptoViki Ransomware on the victim's computer. To begin its attack, the CryptoViki Ransomware will make an index of all files on the victim's computer that are eligible for its encryption attack. The CryptoViki Ransomware targets user generated files and looks for image, media, text, database files, as well as many other types of content. Using a fusion of the RSA and AES encryptions, the CryptoViki Ransomware will make the victim's files completely inaccessible, encrypting them and storing the encryption key (which is itself encrypted with a different encryption algorithm) to its Command and Control server and away from the victim's reach. This is an encryption technique that is typical of most ransomware Trojans active today. The files encrypted by the CryptoViki Ransomware will have the file extension '.viki' added to the end of their file names, making it simple to identify a CryptoViki Ransomware infection and to know which files have been encrypted in the attack.
How Con Artists may Profit from a CryptoViki Ransomware Infection
After encrypting its victims' files, the CryptoViki Ransomware will demand payment of a ransom. To do this, the CryptoViki Ransomware drops a text file named 'readme.txt' on the infected computer's desktop. This file contains the following text:
'Your files have been encrypted.
To decrypt them, You need to write a letter
to the email address cryptoviki@gmail.com .
Next, you will receive all necessary instructions.
Attempts to decipher alone will not lead to anything other than irretrievable loss of information.
If you still want to try, make a backup of the files, or in the case they change the decryption will be impossible under any circumstances.
It is important to refrain from following the instructions in the CryptoViki Ransomware file. Paying these ransoms allows the extortionists to continue creating threats like the CryptoViki Ransomware. Furthermore, there is no guarantee that these people will restore the affected data after the ransom is paid. They are just as likely to ask for more money, ignore the victim, or reinfect the victim's computer.
Dealing with a CryptoViki Ransomware Infection
If the CryptoViki Ransomware has been installed on your computer, PC security analysts strongly advise removing it with a security product that is fully up-to-date. After the CryptoViki Ransomware has been removed, the affected files should be replaced with backup copies. Backup copies of all files are the single best protection against threats like the CryptoViki Ransomware since it removes any power the con artists have over the victim completely. If computer users can restore their files from a backup, then the extortionists have no leverage over the victim. In fact, once file backups become used by all computer users commonly, ransomware attacks like the CryptoViki Ransomware will become ineffective, and the con artists will have to find a different way of extorting computer users.
SpyHunter Detects & Remove CryptoViki Ransomware
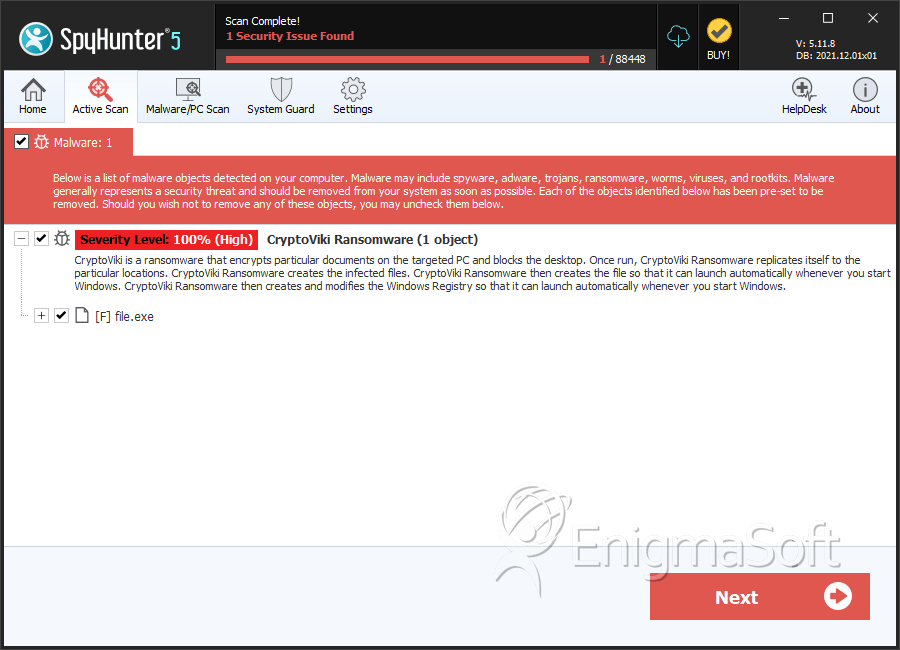
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 696452bdc9b90e64b76b69ef02ad5afb | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.