CryptoJoker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 6 |
| First Seen: | January 4, 2016 |
| Last Seen: | May 30, 2023 |
| OS(es) Affected: | Windows |
The CryptoJoker Ransomware is a ransomware infection. Ransomware threats like the CryptoJoker Ransomware may be transmitted using corrupted email attachments. The CryptoJoker Ransomware represents a real threat to your data and computer. Computer users should protect their machines from threats like the CryptoJoker Ransomware by following safe online browsing habits and always using a reliable security program that is fully up -to-date to protect your computer.
Table of Contents
The CryptoJoker Ransomware – An Unacceptable Joke
The CryptoJoker Ransomware infection is relatively simple: the CryptoJoker Ransomware takes over a computer and attempts to encrypt the victim's files. The CryptoJoker Ransomware targets specific file extensions, including the following: .txt, , .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd, .java, .jpeg, .pptm, .pptx, .xlsb, .xlsm, .db, .docm, .sql, and .pdf. The CryptoJoker Ransomware will change the files' extensions after encrypting them, adding the extension .crjoker to the file name. Once encrypted by the CryptoJoker Ransomware, the files become impossible to access or decrypt without the decryption key. Essentially, the CryptoJoker Ransomware takes the victim's files hostage, demanding payment of a ransom from the victim.
How the CryptoJoker Ransomware Extracts a Ransom from Its Victims
Once the CryptoJoker Ransomware has encrypted a file, it is impossible to access it normally. As part of its infection process, the CryptoJoker Ransomware drops text and HTML files in the folders holding infected files. These files contain instructions about payment of the CryptoJoker Ransomware's ransom. One variant of the CryptoJoker Ransomware contains the following message in these files (it is implied that third parties responsible for these attacks will change their email addresses regularly):
Write to us at mail: file987@sigaint.org
Spare mails: file9876@openmail.cc or file987@tutanota.com.
Instructions for payment will be sent in the opposite letter.
One surprising aspect of the CryptoJoker Ransomware attack is that it does not demand a specific amount. This means that it is likely that the people responsible for the CryptoJoker Ransomware may adjust their ransom depending on the victim and the importance of the encrypted files. PC security researchers strongly advise against paying the CryptoJoker Ransomware ransom. Computer users simply have no guarantee that the people responsible for this attack will honor their part of the agreement and deliver the decryption key after receiving the ransom payment. Avoid supporting these kinds of activities, allowing third parties to finance further attacks. In fact, if all computer users agreed not to pay these types of ransoms, the attacks would no longer be viable.
Additional Information Regarding the CryptoJoker Ransomware
The CryptoJoker Ransomware uses AES-256 encryption to take the victim's files hostage. This results in an encryption that cannot be broken using brute force methods. The tCryptoJoker Ransomware installer may be concealed in the form of a PDF file distributed as an email attachment. The CryptoJoker Ransomware may be distributed using targeted phishing attacks that may not be caught by anti-spam filters all the time. Once the CryptoJoker Ransomware is installed, it will begin its attack, as well as establishing contact with its Command and Control server to transmit the encryption data. The CryptoJoker Ransomware will scan all hard drives on the victim's computer and, unlike other types of threats, will allow the victim's computer to remain functional by only targeting specific file extensions. The CryptoJoker Ransomware and similar threats take advantage of computer users' need to recover specific files that may have a professional or sentimental value, rather than by destroying data or rendering the computer useless. Because of the CryptoJoker Ransomware's attack, the best protection against these types of attacks is the use of a reliable backup method, such as an external memory device or the cloud.
SpyHunter Detects & Remove CryptoJoker Ransomware
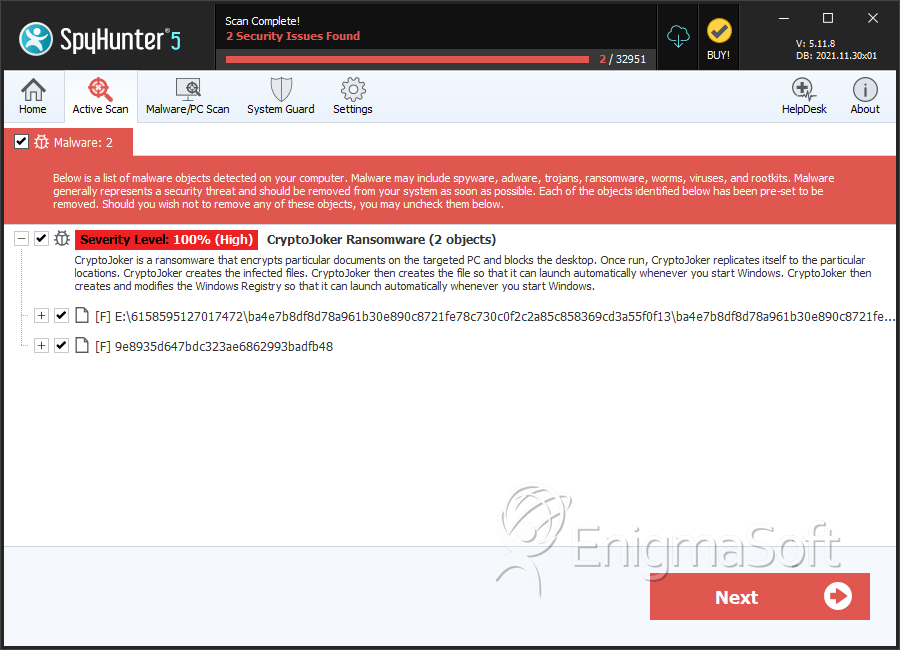
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ba4e7b8df8d78a961b30e890c8721fe78c730c0f2c2a85c858369cd3a55f0f13 | bca6c1fa9b9a8bf60eecbd91e08d1323 | 1 |
| 2. | 9e8935d647bdc323ae6862993badfb48 | 9e8935d647bdc323ae6862993badfb48 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.