CryptoGod Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 73 |
| First Seen: | June 12, 2017 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The CryptoGod Ransomware is a file encoder program based on the infamous HiddenTear open-source ransomware. An important distinction to make is that CryptoGod Ransomware has nothing to do with the CryptoGod Ransomware from June 2017. The CryptoGod 2018 Ransomware is used as a Trojan that encodes the targeted data on computers and offers the affected users to buy a decoder from the people who created the Trojan. The CryptoGod Ransomware does not introduce anything new to the crypto-threat scene, but it may evade some AV scanners. The program at hand is almost identical to the KwaakLocked Ransomware and the CyberSCCP Crypto Ransomware that we have reported in the past. However, the CryptoGod 2018 Ransomware is using a unique ransom message and marks the encoded files with the '.locked' extension.
The CryptoGod Ransomware is programmed to apply an AES-256 cipher to user-generated data like family photos, notes, presentations, downloaded music & video, databases, PDFs and eBooks. The threat is using the reliable AES cipher to make the files unreadable and leave a ransom message on the screens. The encoded files carry the '.locked' extension and something like 'Volborthite Mineral.docx' is renamed to 'Volborthite Mineral.docx.locked.' The ransom alert is produced as a program window titled 'CryptoGod di Patrizio Napoli per esame di stato 2018' that is Italian for 'CryptoGod by Patrizio Napoli for state exam 2018.' Some computer researchers believe that the CryptoGod 2018 Ransomware might be a school project given the simplicity of the CryptoGod 2018 Ransomware and its lack of a 'Command and Control' server configuration. The CryptoGod 2018 window offers the following text (rough translation from Italian):
'EXAMPLE RANSOMWARE BY PATRIZIO NAPOLI FOR STATE EXAMS 2018
5a B SIA
INSERT THE BITCOIN TRANSFER CODE
INSERT YOUR EMAIL
SEND DATA
----------
YOUR PERSONAL FILES ARE TO BE DELETED. YOUR PHOTOS, VIDEOS, ETC DOCUMENTS ...
BUT DO NOT WORRY! IT WILL HAPPEN ONLY IF YOU DO NOT FOLLOW THE RULES.
I HAVE ALREADY ENCRYPTED YOUR FILES, SO THAT YOU CAN NOT ACCESS YOU. EVERY HOUR I WILL SELECT ONE OF THEM AND I WILL CANCEL IT PERMANENTLY AFTER 24 HOURS I WILL CANCEL YOU ALL,
THEREFORE I WILL NOT BE ABLE TO RECOVER THEM.
I AM THE ONLY ABLE TO DECREASE YOUR DATA ..
NOW, KEEP YOUR FILES, YOU CAN NOT DECIDE IT WITHOUT PAYING.
THE AMOUNT TO PAY TO RESTORE THE FILES IS € 300 IN PAYSAFECARD CODES.
YOU CAN INSERT DIRECTLY BELOW YOUR PAYSAFECARD CODES,
THE NAME OF YOUR PC AND YOUR E-MAIL TO SEND THE CODE FOR DECODRYPTION OF FILES.'
The same text can be found in 'LEGGIMI.txt' (README.txt) that may be saved to the desktop and any folder with '.locked' files inside. Computer security researchers advise against interaction with the CryptoGod 2018 Ransomware developers. You may be unable to recover your files without the decryption key, but you can boot backups and the System Recovery Disks that hold older versions of your files. PC users should entrust the removal of the CryptoGod Ransomware to a credible anti-malware suite and install a good backup manager to counter similar threats. The CryptoGod 2018 Ransomware may run on compromised systems as 'CryptoGod.exe' and AV scanners may flag it as:
Gen:Heur.Ransom.HiddenTears.1
HEUR/AGEN.1016243
MSIL.Trojan-Ransom.Cryptear.R
Malware/Win32.Generic.C1020407
Ransomware-FTD!2C6482E7A221
Trojan ( 004ddd301 )
Trojan.Ransom.HiddenTears.1
Trojan.Win32.Z.Ransom.367104
W32/Ransom.MEFJ-8179
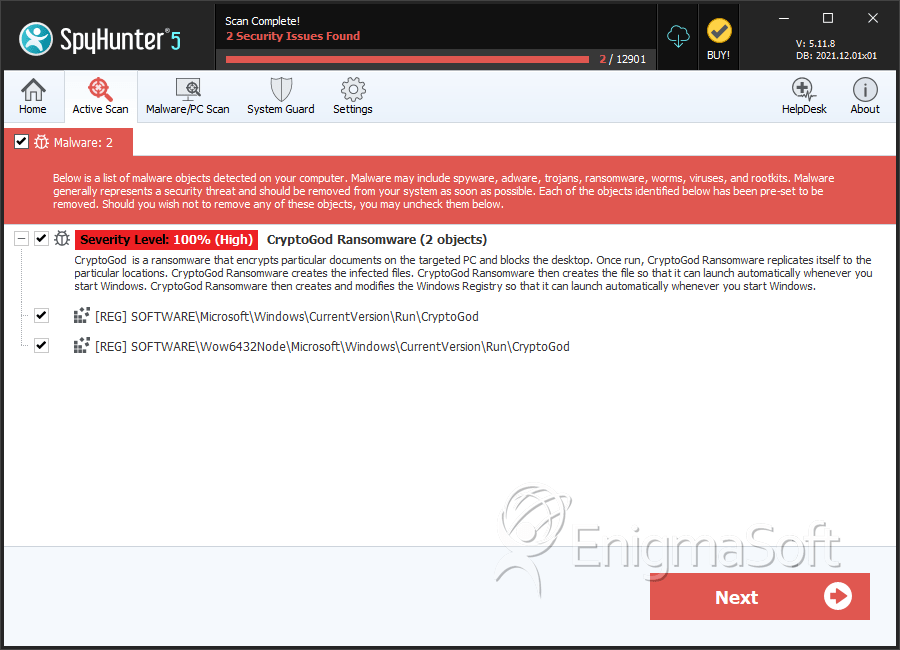
SpyHunter Detects & Remove CryptoGod Ransomware


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.