CryptConsole v3 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 814 |
| First Seen: | February 27, 2015 |
| Last Seen: | April 11, 2022 |
| OS(es) Affected: | Windows |
The CryptConsole v3 Ransomware is a file encoder Trojan that is based on the Trojan with the same name — CryptConsole Ransomware released in January 2017. One of the latest versions called CryptConsole v3 Ransomware was picked up by malware analysts in June 2018. PC users who opened a supposedly safe Microsoft Word file were infected with the threat and were invited to pay 50 USD in Bitcoin to have their files decoded. The developers of the CryptConsole v3 Ransomware have been using the AES and RSA ciphers to lock the users’ content and suggest buying a decryptor for prices that range from 50 USD to 300 USD. We are monitoring the development of the CryptConsole family of Trojans, and the new variant does not leave traces on compromised devices. That prevents cybersecurity researchers from cracking the encryption procedure and, in many cases, the Trojans of the same class have no vulnerabilities to exploit. Hence, it is best to make backups as often as you can.
The CryptConsole v3 Ransomware Trojan is configured to apply a secure cipher to data containers saved to the local disks and removable media storage. Also, the CryptConsole v3 Ransomware may encipher files in shared folders that may interfere with the work of other users on the same computer network. The CryptConsole v3 Ransomware is observed to attach strings like '.heineken@tuta.io_[hex code],' '.sequre@tuta.io_[hex code]' and '.sequre@tuta.io_[random characters]' to filenames and encourage users to write a message to 'heineken@tuta.io' and 'sequre@tuta.io.' For example, 'Imagine Dragons-Believer.mp3' may be renamed to 'Imagine Dragons-Believer.mp3.sequre@tuta.io_f17662.' Unfortunately, the Shadow Volume snapshots by Windows are deleted upon loading the CryptConsole v3 Ransomware, and the System Restore Points are erased from the system. It is best to use backups and clean copies of your files as an alternative to paying money to the CryptConsole team.
You can remove the CryptConsole v3 Ransomware and associated variants using a trusted anti-malware utility. Services like Google backup and Sync, Spider Oak and Dropbox can help users protect valuable data in the cloud. The threat is known to write 'README.txt' to the desktop of compromised users and show the following text:
'Your files are encrypted!
YOUR PERSONAL ID
--------------------
[random characters]
--------------------
Discovered a serious vulnerability in your network security.
No data was stolen and no one will e able to do it while they are encrypted.
For you, we have automatic decryptor and instructions for remediation.
You will receive automatic decryptor, and all files will be restored
--------------------
To be sure in getting the decryption, you can send one file (less than 10MB) to sequre@tuta.io. In the letter inside include your personal ID (look at he beginning of the document). But this action will increase the cost of the automatic decryptor on 50 USD...
Attention!
Attempts to self-decrypting the files will result in the loss of your data.
Decoders other users are not compatible with your data, because each user';s unique encryption key.'
Table of Contents
UPDATE
The 'xzet@tutanota.com' Ransomware Trojan is a program that we have seen in the past but under a different brand. The 'xzet@tutanota.com' Ransomware Trojan is categorized by malware researchers as a variation of the CryptConsole v3 Ransomware. The original cyber threat was identified back in January 2017 with the 'xzet@tutanota.com' Ransomware coming out in April 2018. The 'xzet@tutanota.com' Ransomware is almost identical to the 'kurosaki_ichigo@tutanota.com' and the 'reter@keemail.me' Ransomware that belong to the same malware family.
It is suspected that the people behind the 'xzet@tutanota.com' Ransomware and earlier iterations are busy with pushing many new versions of their Trojans to infect more users and minimize detection ratio by AV companies. The 'xzet@tutanota.com' Ransomware is known to encrypt the same range of data formats as its predecessors. However, the 'xzet@tutanota.com' Ransomware Trojan works in conjunction with a new pair of email accounts and utilizes a slightly different encryption model. The 'xzet@tutanota.com' Ransomware is observed to encipher images, video, audio, text, and databases saved to the local disks. Affected users are likely to notice that their files feature generic white icons and Windows report an error when you try to open the encrypted files. For example 'St. Martin in the Wall Church.png' retains its name but you may not see a thumbnail for the image, and some users may be shown an alert that Windows recognizes the file as corrupted. The ransom note used with the 'xzet@tutanota.com' Ransomware is packed as 'HOW DECRIPT FILES.hta' and reads:
'Your files are encrypted!
Your personal ID
5MQ8LNVQBIIO7DODXK85SW5C1SE2QH1QFO525YEO
Discovered a serious vulnerability in your network security.
No data was stolen and no one will be able to do it while they are encrypted.
For you we have automatic decryptor and instructions for remediation.
How to get the automatic decryptor:
1) 1000 USD
Buy BTC on one of these sites:
[links to Bitcoin exchange services]
bitcoin adress for pay:
12hvCB5iC534V9oBgQTpXF5VmzguaMAzCM
Send 1000 USD
2) Send screenshot of payment to xzer@tutanota.com. In the letter include your personal ID(look at the beginning of this document).
3) You will receive automatic decryptor and all files will be restored
*To be sure in getting the decryption, you can send one file(less than 10MB) to xzer@tutanota.com In the letter include your personal ID(look at the beginning of this document). But this action will increase the cost of the automatic decryptor on 100 USD...
Attention!
No Payment = No decryption
You really get the decryptor after payment
Do not attempt to remove the program or run the anti-virus tools
Attempts to self-decrypting files will result in the loss of your data
Decoders other users are not compatible with your data, because each user's unique encryption key
If you can't send a message, try to write with the other e-mail address, for example register mail.india.com'
Computer researchers note that the name — 'xzet@tutanota.com' Ransomware is simply a working title for an encryption Trojan associated with the 'xzet@tutanota.com' email account. There are nineteen more email accounts connected to the encryption program discusses in this article. PC users who open documents sent from unfamiliar senders may allow the Trojan at hand to enter their system and may be shown any of the following email addresses:
avira@keemail.me, berr@keemail.me, desparo@tuta.io, excaliburarthur@protonmail.com, heineken@tuta.io, helps@tutanota.com, lelouchlamperouge@tutanota.com, mirey@tutanota.com, monkeyd.luffy@keemail.me, redbul@tutanota.com, starbax@tutanota.de, symbyosis@protonmail.com, szems@tutanota.com, taiLung@protonmail.com, teresa@tutanota.de, xser@tutanota.com, xzer@tutanota.com, xzet@tutanota.com, zeman@tutanota.de.
It is recommended to remove the 'xzet@tutanota.com' Ransomware using a respected anti-malware instrument. Paying money to the CryptConsole threat actors will not be guaranteed to secure you a decryption tool for your machine. It is better to take charge and use a backup manager that can restore your data safely. USB drives and cloud storage services can help you save a clean backup copy of your data without fear of succumbing to the demands of crypto-threat operators.
SpyHunter Detects & Remove CryptConsole v3 Ransomware
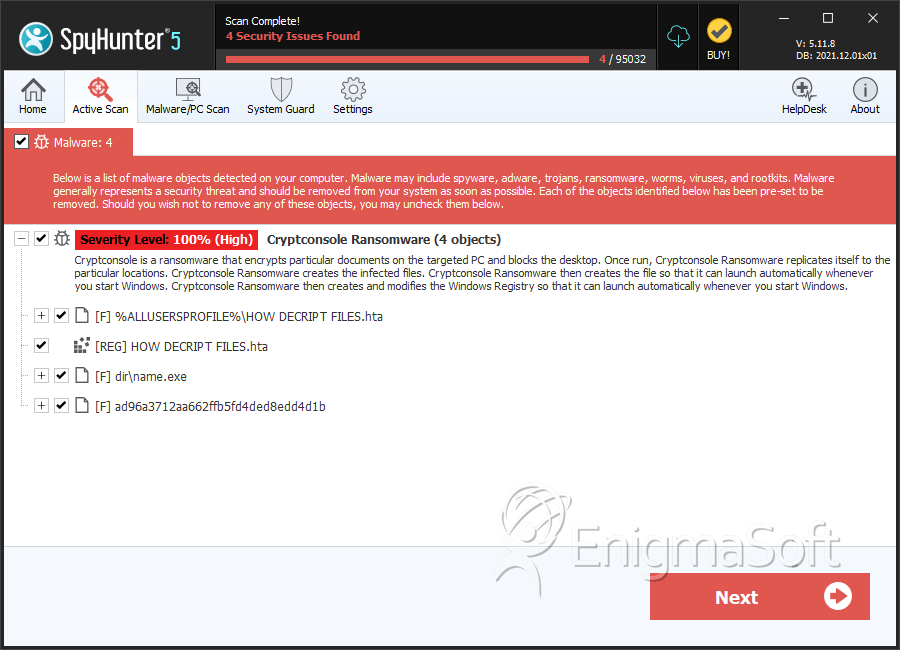
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | HOW DECRIPT FILES.hta | b916ea166673abba1a2927460bad933f | 708 |
| 2. | HOW DECRIPT FILES.hta | 267e56abfc553bf77a4366f5596c55ce | 62 |
| 3. | HOW DECRIPT FILES.hta | 251bc88dedd1399eba7fe0bb8a5a1fd6 | 14 |
| 4. | HOW DECRIPT FILES.hta | d7b8230c9909a9cf4a21a3f55cd95318 | 7 |
| 5. | name.exe | 1c240d1a748471b20047dbd94c2e6b9d | 2 |
| 6. | ad96a3712aa662ffb5fd4ded8edd4d1b | ad96a3712aa662ffb5fd4ded8edd4d1b | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.