Crypren Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | May 16, 2016 |
| OS(es) Affected: | Windows |
The Crypren Ransomware is a ransomware infection that replaces the victim's files' extension with the extension '.ENCRYPTED' after encrypting them using the RSA-2048 encryption. The Crypren Ransomware demands the payment of $250 USD to decrypt the victim's files. It may not be possible to recover from these infections, which may require that computer users wipe their hard drive and recover their files from a backup. However, there is currently a decryption utility available, although it may be difficult to run the utility in a Windows OS since its creator made it on Linux.
Table of Contents
How the Crypren Ransomware may Enter a Computer
The Crypren Ransomware may be distributed through corrupted email attachments distributed through spam email. The most common emails associated with the Crypren Ransomware may claim to be associated with a shipping firm like FedEx or DHL and contain a bogus notification on a shipment. When computer users open an attached file or click on an embedded link in these corrupted email messages, the Crypren Ransomware is installed on the victim's computer. As soon as the Crypren Ransomware enters the victim's computer, it begins encrypting the victim's files.
Analyzing the Crypren Ransomware Infection
The Crypren Ransomware uses its encryption algorithm to encrypt the victim's files. The following are the files that are targeted by the Crypren Ransomware and similar ransomware threats (new files may be added to this list every day):
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt.
Once your files are encrypted, the Crypren Ransomware changes their extensions. The Crypren Ransomware also drops text and HTML files containing payment information and a ransom note in each directory where files were encrypted. The Crypren Ransomware also changes the affected computer's Desktop image so it will also display a ransom note. The Crypren Ransomware also deletes Shadow Volume Copies of affected files as well as System Restore points, making these recovery methods ineffective.
The content of the ransom note that has been associated with the Crypren Ransomware is the following:
YOUR PERSONAL FILES HAS BEEN ENCRYPTED
Your data (photos, documents, databases, etc.) have been encrypted with a private and unique key generated for this computer. This means that you will not be able to access your files anymore until they are decrypted. The private key is stored in our servers and the only way to receive key to decrypt your files is making payment.
The payment has to be done in Bitcoin to a unique address that we generated for your. Bitcoins are the virtual currency to make online payments. If you don’t know how to get Bitcoins, you can cluck the button 'How to buy Bitcoins” below and follow the instructions. If you have problem with this task use Internet.
You have only 1 week to submit the payment. When this time ends, the unique key will be destroyed and you won’t be able to recover your files anymore. Your unique key will be destroyed in 1 week from encryption! To recover your files, you must send 0,1 Bitcoins (~$37) to the next Bitcoin address: –
Dealing with the Crypren Ransomware
Although there is currently a decryption utility for the Crypren Ransomware, it may be impossible to recover from similar ransomware threats. Therefore, the best method for dealing with the Crypren Ransomware and similar threats is prevention. PC security analysts strongly recommend that computer users keep a backup of their files on an external memory device.
SpyHunter Detects & Remove Crypren Ransomware
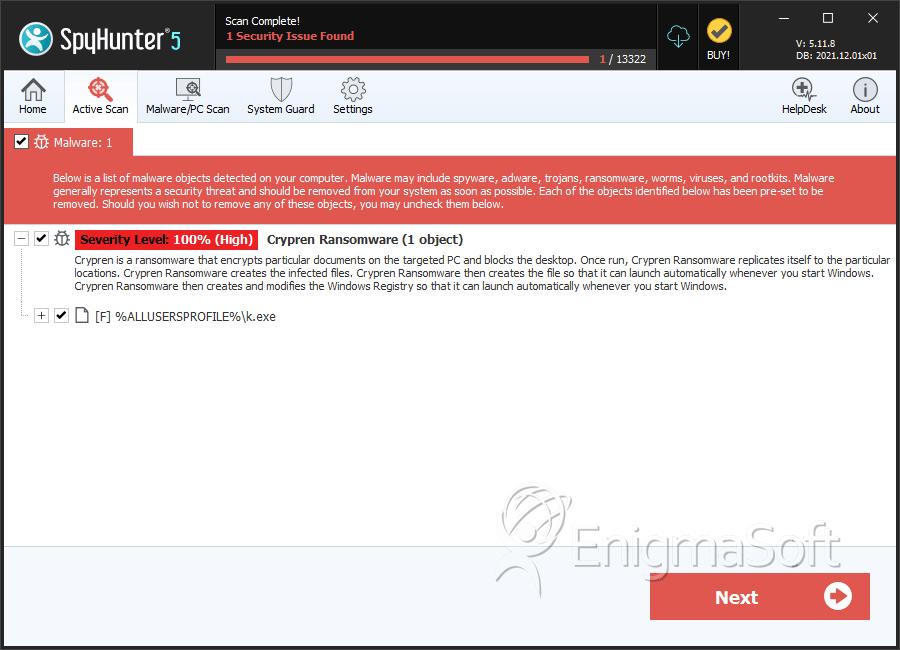
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | k.exe | f6a8d7a4291c55020101d046371a8bda | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.