Cryakl Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 82 |
| First Seen: | July 28, 2016 |
| Last Seen: | August 31, 2020 |
| OS(es) Affected: | Windows |
Encryption ransomware Trojans are among the most common types of threats active today, and may represent a real danger to computer users. PC security analysts have observed new varieties of these infections appearing nearly every day in the last year. The Cryakl Ransomware is one more of these infections. Like many other encryption ransomware Trojans, the Cryakl Ransomware is designed to take the victim's data hostage, demanding the payment of a ransom to return access to the victim's files. To do this, the Cryakl Ransomware encrypts the victim's files, demanding that the victim makes a ransom payment to obtain the decryption key.
Table of Contents
The Cryakl Ransomware’s Executable File’s Name Tries to Fool PC Users
The Cryakl Ransomware's executable file is named schvost.exe, making it easy to be confused with legitimate system files. Once the Cryakl Ransomware drops its executable file on the victim's computer, the Cryakl Ransomware begins encrypting the victim's files. The Cryakl Ransomware searches the victim's hard drives for files with certain file extensions, and then uses an asymmetric encryption algorithm to encrypt this data. The Cryakl Ransomware targets files with the following extensions (among many others):
.dif, .dip, .djv, .djvu, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dtd, .dwg, .dxf, .eml, .eps, .fdb, .fla, .flv, .frm, .gadget, .gbk, .gbr, .ged, .gif, .gpg, .gpx, .gz, .h, .htm, .html, .hwp, .ibd, .ibooks, .iff, .indd, .jar, .java, .jks, .jpg, .js, .jsp, .key, .kml, .kmz, .lay, .lay6, .ldf, .lua, .m3u, .m4a, .m4v, .max, .mdb, .mdf, .mfd, .mid, .mkv, .mml.
The files encrypted by the Cryakl Ransomware become inaccessible and can be recognized easily because the Cryakl Ransomware adds the extension '.the Cryakl' to each encrypted file. According to the Cryakl Ransomware's ransom note, the victim has 72 hours to pay a ransom to receive the decryption key to recover the encrypted files. The following is the ransom note that is associated with the Cryakl Ransomware:
All your files have been
encrypted by the Cryakl virus.
All the files were encrypted using
cryptographically strong AES algorithm.
Pay us in Bitcoins to get them back.
You have 72 hours.
The Cryakl Ransomware's ransom note is quite short and to the point and, curiously enough, contains no contact information or detailed payment instructions. In most cases, these ransom notes will include a contact email or a link to a payment website (generally on the Dark Web).
Dealing with the Cryakl Ransomware
You should abstain from paying the Cryakl Ransomware's ransom. There are several reasons why including that one can't trust con artists to honor their promises and restore the files. You should also avoid funding further attacks by helping these con artists to sustain their ransomware attacks financially. However, the most important reason to abstain from paying the Cryakl Ransomware's ransom is that malware analysts have observed that a utility for decrypting files affected by the Cryakl Ransomware is readily available. Malware researchers have made a Cryakl Ransomware decryptor available publicly, and computer users can take advantage of it to restore their files.
Preventing the Cryakl Ransomware Attacks
The most common way of distributing the Cryakl Ransomware and similar threats is through the use of corrupted email messages. PC security researchers have observed that the Cryakl Ransomware may be distributed in corrupted email attachments or embedded links that lead the victim to an attack website. Because of this, being cautious when dealing with unsolicited email messages is the most effective measure computer users can take to prevent the Cryakl Ransomware attacks. A reliable spam filter to prevent these messages from arriving in the first place is also important. Malware analysts also recommend the use of a reliable security program that is fully up-to-date so as to intercept the Cryakl Ransomware before it initiates its attack. A combination of strong security software and following good safety precautions online can prevent the Cryakl Ransomware and numerous other ransomware Trojan attacks. Other steps may include avoiding potentially risky websites and unknown software downloads.
Update December 12th, 2018 - '.doubleoffset File Extension' Ransomware
The '.doubleoffset File Extension' Ransomware an encryption ransomware Trojan that is a variant of Cryakl, an encryption ransomware family released in Fall of 2018. The '.doubleoffset File Extension' Ransomware carries out a typical encryption ransomware attack, making the victim's files inaccessible by using a strong encryption algorithm and then demanding a ransom payment from the victim. You should take preventive measures to limit the damage that threats like the '.doubleoffset File Extension' Ransomware can do to your data.
How the '.doubleoffset File Extension' Ransomware Carries Out Its Attack
The '.doubleoffset File Extension' Ransomware uses a strong encryption algorithm to make the victim's files inaccessible. The '.doubleoffset File Extension' Ransomware's attack targets the user-generated files, which may include files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
Once the victim's files have been modifieded, the '.doubleoffset File Extension' Ransomware delivers a ransom note demanding a ransom payment in exchange for the decryption key. Unfortunately, once a threat like the '.doubleoffset File Extension' Ransomware attacks someone's files, they are no longer recoverable.
How the '.doubleoffset File Extension' Ransomware Threatens Your Files
The '.doubleoffset File Extension' Ransomware variant in the Cryakl Ransomware family was observed on December 10, 2018, and is nearly identical to other members of this ransomware family. The '.doubleoffset File Extension' Ransomware's attack marks each file encrypted by its attack by adding the file extension '.doubleoffset' to the end of the file's name. The '.doubleoffset File Extension' Ransomware displays a program window that has the title 'Pay for decrypt' and contains the following short message:
'Your files was encrypted! To decrypt write us
biger@x-mail.pro'
The '.doubleoffset File Extension' Ransomware also delivers this same message to each directory where it encrypts the data, dropping it in a text file named 'README.txt.' PC security researchers strongly advise computer users to avoid contacting the criminals at the provided email address or following any other instructions from the '.doubleoffset File Extension' Ransomware's creators.
Dealing with the '.doubleoffset File Extension' Ransomware Infection
The most practical protection against threats like the '.doubleoffset File Extension' Ransomware is to have file backups. Having backup copies of your data and storing these backups on a password protected location is the most successful way of ensuring that your data is safe from these threats. Apart from file backups, malware researchers recommend that computer users take steps to protect their PCs by using a strong security program and establishing healthy security protocols, such as taking precautions when dealing with unsolicited email messages and ensuring that all computer users know how to navigate the Web safely.
SpyHunter Detects & Remove Cryakl Ransomware
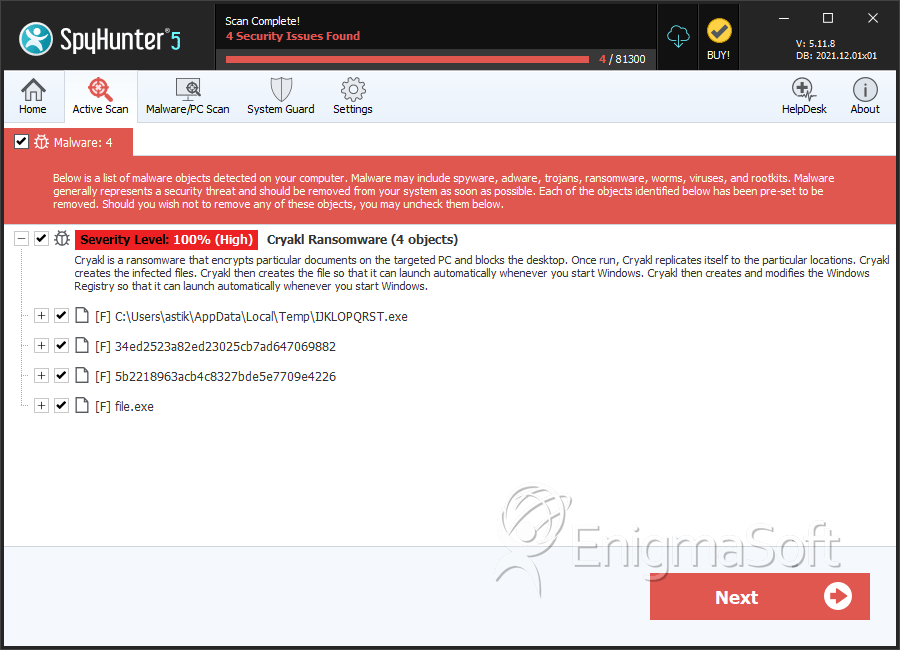
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | IJKLOPQRST.exe | 199833c673f8d894b1b6f6789c195057 | 9 |
| 2. | 34ed2523a82ed23025cb7ad647069882 | 34ed2523a82ed23025cb7ad647069882 | 4 |
| 3. | 5b2218963acb4c8327bde5e7709e4226 | 5b2218963acb4c8327bde5e7709e4226 | 0 |
| 4. | file.exe | 326cb4b4e4a6cff116c2a9547040d473 | 0 |
| 5. | file.exe | defa18530a4c0becd7dc14bb6484adcb | 0 |

