Coban Ransomware
The Coban Ransomware is an encryption ransomware Trojan that is part of the CryptoMix, CriptMix, or CryptoShield family of encryption ransomware Trojans. There are some slight differences between the Coban Ransomware and previous members of this family, however. The threat payload that the Coban Ransomware delivers is the same as the previous version and is delivered using corrupted Microsoft Word documents, which have enabled macros that may be attached to spam email messages. However, the Coban Ransomware is slightly different in that its attack includes new obfuscation and other websites involved in the attack, which can bypass some security measures that have already become standard against previous variants in this ransomware family. Like most other encryption ransomware Trojans, the Coban Ransomware carries out an attack that involves enciphering the victims' files using an effective encryption algorithm, taking them hostage and preventing the victim from accessing their data.
Table of Contents
How the Coban Ransomware Carries out Its Attack
The Coban Ransomware uses the AES 256 encryption to make the victim's files inaccessible. The Coban Ransomware will target the user-generated files, which include a wide variety of file types. The Coban Ransomware targets different file types ins its attacks, which include but are not restricted to:
.aif, .apk, .arj, .asp, .bat, .bin, .cab, .cda, .cer, .cfg, .cfm, .cpl, .css, .csv, .cur, .dat, .deb, .dmg, .dmp, .doc, .docx, .drv, .gif, .htm, .html, .icns, .iso, .jar, .jpeg, .jpg, .jsp, .log, .mid, .mp3, .mp4, .mpa, .odp, .ods, .odt, .ogg,.part, .pdf, .php, .pkg, .png, .ppt, .pptx, .psd, .rar, .rpm, .rss, .rtf, .sql, .svg, .tar.gz, .tex, .tif, .tiff, .toast, .txt, .vcd, .wav, .wks, .wma, .wpd, .wpl, .wps, .wsf, .xlr, .xls, .xlsx, .zip.
The Coban Ransomware will point out the files enciphered by the attack appending the '.COBAN' file extension to the end of each encrypted file's name. Once the Coban Ransomware concludes the files' encryption, it will no longer be possible to recover them without having access to the decryption key, which the crooks hold in their possession. The Coban Ransomware targets commonly used file types with a high probability of hitting data that may be important personally or professionally to the victim.
How the Coban Ransomware Delivers Its Ransom Note
The Coban Ransomware demands a ransom payment from the victims as soon as it finishes the files' encryption. To do this, the Coban Ransomware will display a ransom note, which is delivered in a text file that is displayed on the infected computer's desktop. The Coban Ransomware's ransom note is named '_HELP_INSTRUCTION.txt' and contains the following text:
'All your files are already encrypted due to a vulnerability in the system!
For decoding it is necessary to pay ransom by bitcoins.
Bitcoins can be bought here - localbitcoins.com in many ways.
Write to us at mail ms.decry@aol.com and tell us your unique ID in the subject line. DECRYPT-ID-[8 CHARACTERS]-[4 CHARACTERS]-[4 CHARACTERS]-[4 CHARACTERS]-[12 CHARACTERS] number'
As is apparent from the Coban Ransomware's ransom note, the victim is asked to pay a ransom using Bitcoins to receive the decryption key necessary to restore the affected files. Computer users must avoid paying this ransom or following the instructions in the Coban Ransomware ransom note. Instead, they should take precautions to ensure that their data is preemptively protected against the Coban Ransomware and other, similar threats.
Protecting Your Data from Ransomware Trojans Like the Coban Ransomware
Ensure that you can restore your data in case it becomes inaccessible due to the Coban Ransomware or other ransomware attacks. The best way to do this is to have backup copies of your data. If you have backup copies of your data, then you can recover from a Coban Ransomware attack by simple restoring your data from the backup copy after removing the Coban Ransomware infection itself with the help of an up-to-date security program suite.
SpyHunter Detects & Remove Coban Ransomware
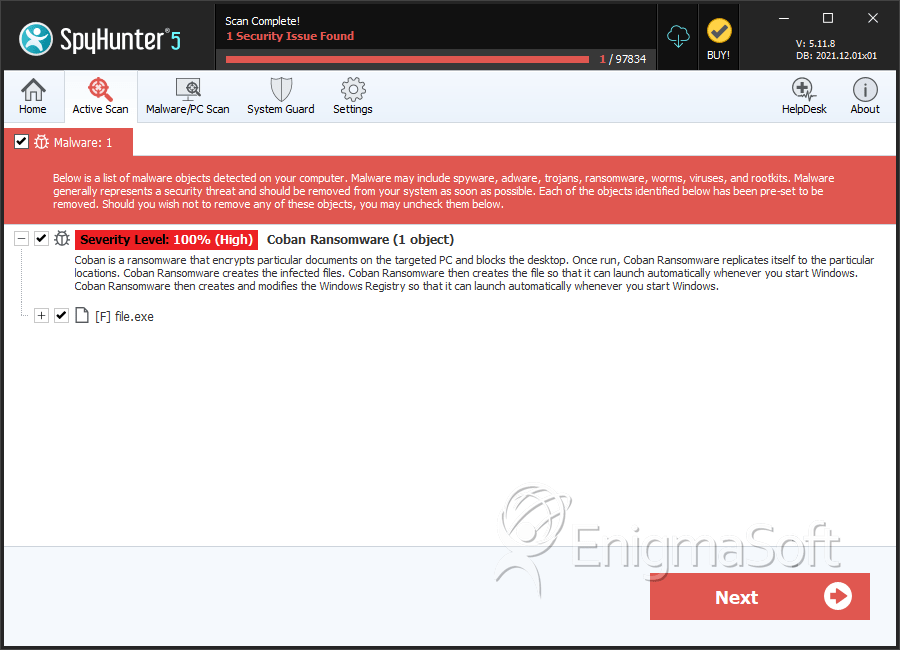
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | e2e992f1884ad6778856ff78d8c2e68f | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.