ChineseRarypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 12 |
| First Seen: | July 12, 2019 |
| Last Seen: | September 5, 2019 |
| OS(es) Affected: | Windows |
The ChineseRarypt Ransomware is a file-locking Trojan that has been spotted by malware researchers recently. This ransomware threat is not a variant of any of the popular ransomware threats.
Initially, researchers believed that this ransomware threat is not a variant of any of the popular ransomware threats. However, now some sources claim that ChineseRarypt Ransomware belongs to the Djvu Ransomware family. So far, it is known that this ransomware affects only computers running Windows operating system.
Table of Contents
Vectors of Distribution
Cybersecurity experts have been unable to confirm what infection vectors have been employed in spreading the ChineseRarypt Ransomware. However, some speculate that the cyber crooks responsible for the ChineseRarypt Ransomware are using spam email campaigns, alongside bogus software updates and likely corrupted pirated applications to spread their creation. In addition, ransomware can also be bundled with freeware or hide inside torrents. Otherwise, suspicious ads or offers on the Internet could also lead to corrupted pages infected with malware threats.
There is evidence that ChineseRarypt has entered systems through certain other software. Some of the programs and applications which are known for spreading this ransomware are: PasteFiler 1.2.1, Duke Nukem 3D 1.1, McSerialnumber Pro 1.0, viJournal Lite 2.5.2, Motion v5.1, iTunes Playlist Changer 1.2.2, Automator Multi-Item Processing Utility 1.0, Hidden Settings 0.8.5, ColorConverter 2.14.1120, Ultranium4 1.5, AKVIS ArtWork, Fantashow, SpeedRun 1.2, BF1942 Launcher 1.0, ProteinGlimpse 1.5. If you have any of these tools installed on your PC, you should remove it immediately. It looks like the malware is also available as a Ransomware-as-a-Service (RaaS) on underground hacking forums.
How It Works
Immediately after gaining access to a system, ChineseRarypt initiates a scan to detect the location of the files which will be targeted for encryption. As typical for ransomware threats, Chinese Rarypt targets files of all popular formats that are likely to contain valuable for the victim personal data like text documents, photos, and videos. On the other hand, files crucial for the proper work of the operating system should remain unaffected.
Instead of encrypting each file individually, like most other ransomware threats, ChineseRarypt first places all data into a password protected archive and then encrypts the entire archive. In some cases, the malware deletes folders that contain archived data so that the files cannot be recovered, while in other cases researchers claim that the user could access the archives after paying the required amount of ransom. Research shows that files encrypted by this ransomware become the extensions ".Chineserarypt" or ".Grovas".
After encryption is complete, ChineseRarypt Ransomware drops a ransom note called "HOW_TO_BACK_YOUR_FILES.txt." The authors of the malware have used all caps in naming the note, which is a common tactic used by ransomware authors as it reduces the chances of the victim to end up overlooking their ransom message. ChineseRarypt Ransomware copies the style of the famous Maoloa Ransomware:
"YOUR FILES ARE ENCRYPTED !!!
TO DECRYPT, FOLLOW THE INSTRUCTIONS:
To recover data you need decrypt tool.
To get the decrypt tool you should:
1.In the letter include your personal ID! Send me this ID in your first email to me!
2.We can give you free test for decrypt few files (NOT VALUE) and assign the price for decryption all files!
3.After we send you instruction how to pay for decrypt tool and after payment you will receive a decryption tool!
4.We can decrypt few files in quality the evidence that we have the decoder.
DO NOT TRY TO DO SOMETHING WITH YOUR FILES BY YOURSELF YOU WILL BRAKE YOUR DATA !!! ONLY WE ARE CAN HELP YOU! CONTACT US:
Decryptcn@protonmail.ch
ATTENTION !!! THIS IS YOUR PERSONAL ID WICH YOU HAVE TO SEND IN FIRST LETTER:
s2 1r xx A2 Jd Bj An Px hg 7C rj au LE BC s2 a6
26 1c 23 0s ku Fr KV OF l0 IV VX hz fE YK p+ KJ
***"
The attackers offer to unlock a few files for free, as long as they are not valuable. They do not mention what the ransom fee is but they give out an email address where the PC user is meant to get in touch – "Decryptcn@protonmail.ch." Other email addresses related to the cybercrooks behind ChineseRarypt include merosa@firemail.cc and merosa@india.com. Some analyzed samples suggest that the ransom amount requested by this threat range between $480 and $980 worth of Bitcoins.
Available Technical Details
ChineseRarypt uses the RSA-2048 algorithm to encypt files on the infected machine. According to some analyses by cyber security experts, the ransomware installs itself into the C:\Program Files folder, while its malicious files can also be found in the %TEMP%, %USERPROFILE%\Downloads, and %USERPROFILE%\Desktop paths. The executable can, in some cases, be found under the name "ChineseRarypt Ransomware.exe" in the Program Files folder. Other published data indicates that some of the files infected by ChineseRarypt are wmdmps.dll 11.0.5721.5145, System.Web.Extensions.Design.ni.dll 3.5.30729.5420, basecsp.dll 6.0.6001.18000, WpdMtpUS.dll 6.0.6001.18000, Microsoft.Build.Engine.dll 2.0.50727.5420, winnsi.dll 6.0.6001.18000,, dfrgsnap.dll 5.1.2600.1106, wmiprov.dll 5.1.2600.5512, System.ni.dll 2.0.50727.1434, tlntsvrp.dll 5.1.2600.1106.
ChineseRarypt Ransomware Operators Should Never Be Trusted
It is advisable that you not to contact the creators of the ChineseRarypt Ransomware. Such individuals often trick users into paying them money and end up not delivering on their end of the deal. A safer solution is to download and install a reputable anti-virus application, which will wipe off ChineseRarypt Ransomware from your PC. Files encrypted by ChineseRarypt can be recovered only after the infected system has been cleaned up with the help of a professional malware removal tool.
SpyHunter Detects & Remove ChineseRarypt Ransomware
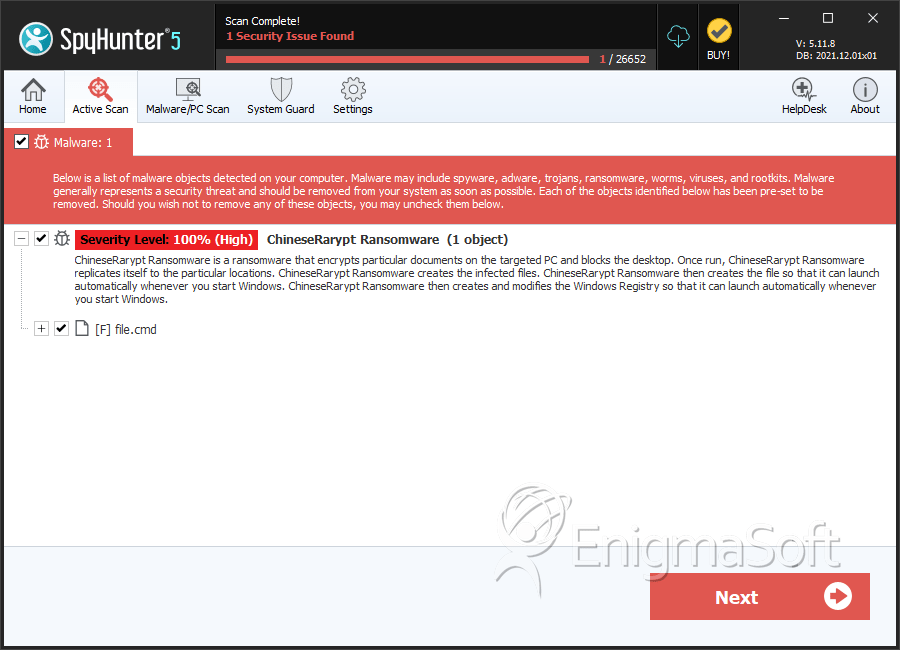
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.cmd | f18b3b2dc6556d60663d70ac411c0ac8 | 6 |

