Cerberos Ransomware
PC security researchers first received reports of the Cerberos Ransomware infections in April 2017. The Cerberos Ransomware is a variant of an already existing ransomware Trojan, which tended to go by the name of Cyber Splitter and had been released in a couple of different versions. The team responsible for this threat signed the executable file responsible for the Cerberos Ransomware attack. The Cerberos Ransomware is being delivered in the form of a bogus update for Adobe Acrobat Reader currently, in an installer file named 'pdf.exe.' Another way in which the Cerberos Ransomware may be delivered is in the form of a corrupted email file attachment that is delivered in conjunction with a social engineering tactic.
Table of Contents
A Mythological Dog Messing Up with Your Files
The Cerberos Ransomware seems to be designed to infect computer users in the Americas and in Western Europe. The Cerberos Ransomware is linked to a large distribution network, although not as large as that associated with higher profile ransomware threats. Like other ransomware Trojans, the Cerberos Ransomware is designed to encrypt all files on the victim’s drives, including removable memory devices connected to the infected computer and storage connected on the infected computer's network. The Cerberos Ransomware uses the AES 256 encryption to make the victim’s files inaccessible completely, storing the decryption key on the Cerberos Ransomware’s Command and Control server to make it irretrievable for victims of the attack or PC security researchers attempting to combat the Cerberos Ransomware infection. The files that have been encrypted in the Cerberos Ransomware attack become inaccessible and are not recoverable without access to the decryption key. The Cerberos Ransomware will encrypt the following file types during its attack:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, .CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD,.WMV, .XLS, .XLSX, .XPS, .XML, .CKP, .ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
The Cerberos Ransomware delivers a ransom note alerting the victim of the attack in a program file named 'cerberos' displayed on the victim's computer. The Cerberos Ransomware's ransom message contains the following text:
'Your Files has been infected By the Cerberos Ransomware And Your Data has been crypted
Contact: cerberos-decrypter@lgmail.com'
Responding Appropriately to a Cerberos Ransomware Infection
The Cerberos Ransomware encrypts files in a way that does not allow computer users to recover the affected files without the decryption key. Because of this, it is important to have backup copies of all files. If computer users can recover the encrypted file by simply copying the backup copy after deleting the encrypted version, then the people responsible for the Cerberos Ransomware attack lose all power they have over the victim. Malware analysts strongly advise computer users to have backup copies, as well as a reliable security program that is fully up-to-date. An anti-virus program can help delete the Cerberos Ransomware infection and intercept the attack before the victim's files are compromised. If your computer has been compromised in the Cerberos Ransomware attack, it should be removed and then you can replace the compromised files with the backup copies. In many cases, it is preferable to use a disk image or wipe the infected drive entirely before restoring the affected files. PC security researchers do not advise computer users to contact the people responsible for this attack.
SpyHunter Detects & Remove Cerberos Ransomware
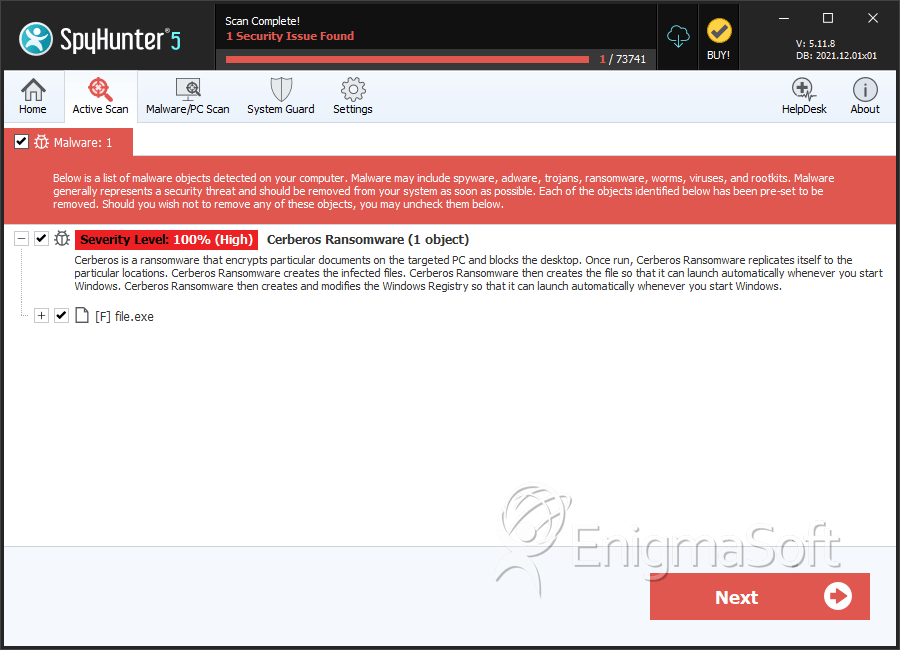
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 7ed0b77353e094d9a1042769a78ef6a0 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.