BitPyLock Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | January 19, 2011 |
| Last Seen: | March 6, 2020 |
| OS(es) Affected: | Windows |
BitPyLock Ransomware Image
Cybercriminals worldwide have acquired quite a taste for ransomware threats since they are often perceived as an easy way to generate revenue and a rather safe method of tricking innocent users because there are rarely any negative repercussions for perpetrators. The BitPyLock Ransomware is one of the latest data-locking Trojans spotted circulating the Web. So far, it would appear that the BitPyLock Ransomware is targeting businesses mainly and not regular users. However, this does not mean that the attackers will not change their approach and opt to attack regular users in the future.
This Week in Malware Ep7: Bitpylock Ransomware Phishing Campaigns
Propagation and Encryption
The BitPyLock Ransomware is likely being propagated via bogus emails. Cybercriminals often mask spam emails as important messages from the government or a large corporation. Such fake emails tend to contain a fraudulent message and a corrupted attachment. If the targets execute the corrupted attached file, their systems will be infiltrated by the BitPyLock Ransomware. Upon compromising a target, the BitPyLock Ransomware will scan the data present on the victim's system. Next, the BitPyLock Ransomware will trigger its encryption process and lock all the targeted data. Rest assured that all commonly used file types will be locked by this threat swiftly – documents, presentations, databases, archives, spreadsheets, images, audio files, etc. All the encrypted files will have a new extension added to their filenames - '.bitpy.' For example, a file that was named 'silver-line.mp3' initially will be renamed to 'silver-line.mp3.bitpy' as soon as the BitPyLock Ransomware has completed its encryption process.
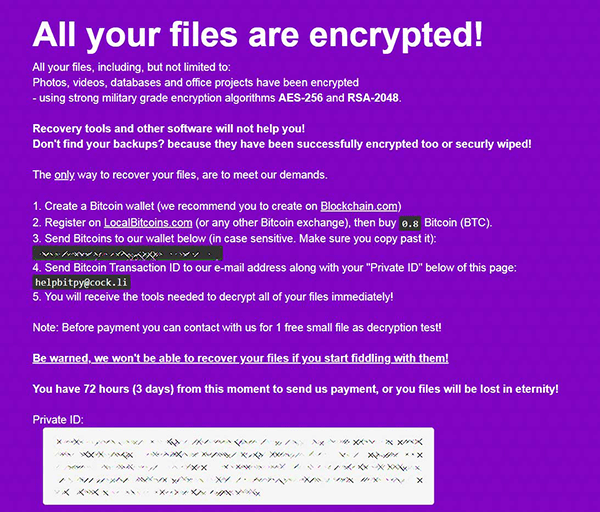
The Ransom Note
The BitPyLock Ransomware will drop its ransom note on the user' desktop named '# HELP_TO_DECRYPT_YOUR_FILES #.html.' The criminals explain to the users that their data has been encrypted securely, and if they want to recover their files, they will have to cooperate. Oftentimes, authors of ransomware claim that victims who attempt to unlock their files with a free decryption tool will instead end up damaging them. The attackers demand the payment be in Bitcoin as using a cryptocurrency instead of conventional payment methods helps cyber crooks protect their identity and avoid punishment for their crimes. The ransom fee in the case of the BitPyLock Ransomware is 0.8 Bitcoin (about $6,300 when this article was written). As means of communication, the creators of the BitPyLock Ransomware have provided an email address - ‘helpbitpy@cock.li.' To prove to victims that they are capable of reversing the damage, the attackers are willing to decrypt one file free of charge. In an attempt to put extra pressure on the victim, the attackers claim that unless the payment is processed within 72 hours, they will wipe out the decryption key the victim to recover their data.
We advise you against paying cyber crooks, no matter what they promise to provide you with in return. Most victims of ransomware who pay the fee demanded are left empty-handed because as soon as the attackers receive the payment, they lose interest in cooperating with the user. You should consider investing in a genuine anti-virus software suite that will not only remove the BitPyLock Ransomware from your computer but also will make sure you do not get infected again.

