AutoTRON Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 12 |
| First Seen: | April 26, 2018 |
| Last Seen: | January 26, 2019 |
| OS(es) Affected: | Windows |
PC security researchers first observed the AutoTRON Ransomware, a ransomware Trojan, on April 22, 2018. There is little to differentiate the AutoTRON Ransomware from the many other encryption ransomware Trojans that are being used to carry out attacks on computer users currently. In fact, the AutoTRON Ransomware has snippets of code from other ransomware Trojans embedded in its code, although this is not uncommon and does not indicate any connection between the AutoTRON Ransomware and other threat families. The AutoTRON Ransomware, like most threats of this type, is designed to take the victims' files hostage and then demanding that the victim pays a large ransom to recover the files that were encrypted by the attack. It is paramount to take steps to protect your files from threats like the AutoTRON Ransomware, which is becoming more common in the last few years increasingly, in large part due to the rise of RaaS services (Ransomware as a Service) and of open source ransomware engines that can be used to create these threats easily.
Table of Contents
The AutoTRON Ransomware Targets the User-Generated Files Primarily
The AutoTRON Ransomware may be distributed by using corrupted spam email messages. This is not an uncommon way of distributing threats like the AutoTRON Ransomware. Victims will receive a spam email message with an attached Microsoft Word document that includes damaged embedded scripts that can download and install the AutoTRON Ransomware onto the victim's computer. The AutoTRON Ransomware will use an encryption algorithm to make the victim's files inaccessible, targeting the user-generated files, which may include files with the following file extensions:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
Once the AutoTRON Ransomware has encrypted the victim's files, the AutoTRON Ransomware will identify the blocked content by adding the file extension '.TRON” to the end of the file's name, after the original file's file extension.
How the Con Artists may Profit from Using the AutoTRON Ransomware
When the AutoTRON Ransomware encodes a file, it will not be recognized by the Windows Explorer or be opened by the victim's applications. The AutoTRON Ransomware will have taken the victim's files hostage since they will become inaccessible. The AutoTRON Ransomware will deliver a ransom note in a text file dropped onto the infected computer's desktop. This file, named 'README.txt,' will suggest that the victim write an email to 'bitcoin.change.manager@gmail.com.' Fortunately, unlike other ransomware threats, it is possible for computer users to restore the files encrypted by the AutoTRON Ransomware currently. There are public decryption programs available that should be used to accomplish it. However, this is an exception. In most cases, the victims of ransomware Trojans that carry out attacks similar to the AutoTRON Ransomware will have no recourse to recover their files. Because of this, the best protection against these threats is to have file backups on external devices. Having file backups allows computer users to recover their files without having to contact the con artists or negotiate to pay a large ransom. Apart from file backups, PC security researchers strongly advise computer users to install a strong and up-to-date anti-malware application to prevent these threats from being installed.
SpyHunter Detects & Remove AutoTRON Ransomware
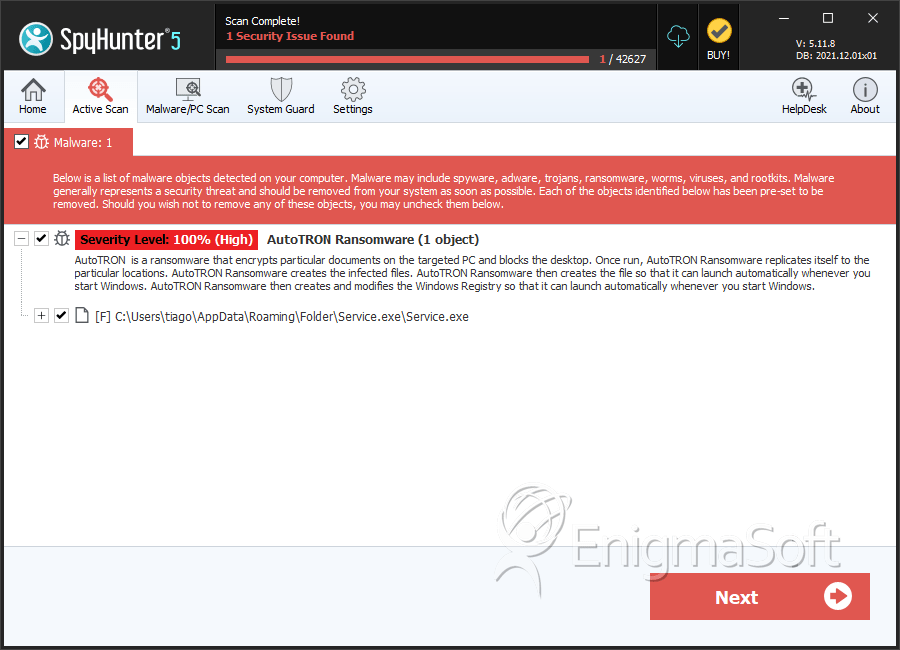
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Service.exe | 1f37eebe61bc9252bd72e643f4223896 | 2 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.