Astaroth Trojan
 PC security researchers first observed the Astaroth Trojan towards the end of 2018. Threats like the Astaroth Trojan are known as Trojans in reference to the Trojan Horse, which was disguised as a gift but actually housed soldiers intended to destroy Troy. Trojans like the Astaroth Trojan are generally disguised as benign files but, in reality, contain a harmful payload, which carries out a vicious attack on the victim's computer the same way. The Astaroth Trojan is typically delivered to the victims via corrupted spam email attachments or embedded links, or through bogus online downloads. The Astaroth Trojan integrates methods that legitimate software uses to recover lost passwords to collect the victims' online login information and other data. The Astaroth Trojan poses a significant threat to computer users' data and security. Therefore, computer users must take steps to safeguard their PCs from threats like the Astaroth Trojan.
PC security researchers first observed the Astaroth Trojan towards the end of 2018. Threats like the Astaroth Trojan are known as Trojans in reference to the Trojan Horse, which was disguised as a gift but actually housed soldiers intended to destroy Troy. Trojans like the Astaroth Trojan are generally disguised as benign files but, in reality, contain a harmful payload, which carries out a vicious attack on the victim's computer the same way. The Astaroth Trojan is typically delivered to the victims via corrupted spam email attachments or embedded links, or through bogus online downloads. The Astaroth Trojan integrates methods that legitimate software uses to recover lost passwords to collect the victims' online login information and other data. The Astaroth Trojan poses a significant threat to computer users' data and security. Therefore, computer users must take steps to safeguard their PCs from threats like the Astaroth Trojan.
Table of Contents
The Great Duke of Hell Comes to Earth to Damage Your files
The Astaroth Trojan poses a significant threat because it uses files that are signed by legitimate antivirus companies mainly, allowing the Astaroth Trojan to bypass some computers' defenses. Once the Astaroth Trojan infiltrates a computer, this Trojan creates a scheduled task that allows the Astaroth Trojan to run automatically every time the infected computer starts up. The Astaroth Trojan is modular by nature, meaning that it is made up of various modules that are designed to carry out various aspects of the Astaroth Trojan attack. This allows threats like the Astaroth Trojan to be highly adaptable and flexible so that the criminals can react to security measures enacted by PC security providers. The Astaroth Trojan attack's main purpose seems to be to collect passwords from the infected computer.
How the Astaroth Trojan Infects Your Files
The Astaroth Trojan seems to have been designed to collect passwords for database managers, emails, Web logins, and VPN services mainly. The Astaroth Trojan also is capable of tracking keystrokes on infected computers, allowing the Astaroth Trojan to collect the victim's password or credit card information as it is being typed on the infected PC. The Astaroth Trojan attack's main objective is to collect this data to take advantage of the victims and collect their money or online data if possible. The Astaroth Trojan attack has various aspects that are quite innovative, and PC security researchers are still carrying out updates to ensure that the computer users can be safe from threats like the Astaroth Trojan. Some of these aspects, such as the way the Astaroth Trojan uses legitimate password recovery scripts as part of its attack, allow the Astaroth Trojan to bypass various anti-virus programs commonly used today.
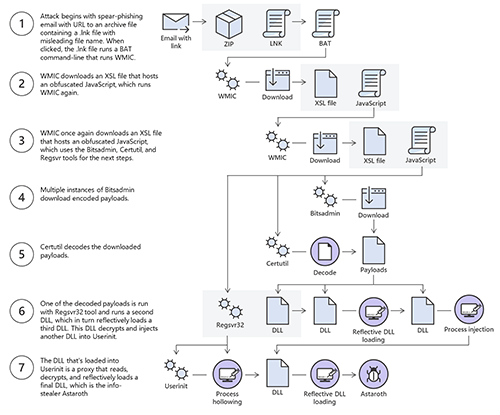
Microsoft's Security Intelligence team discovered a campaign that conducted a complex attack chain that runs the Astaroth threat in an infected system’s memory. Such a process is demonstrated through the image below from Microsoft.
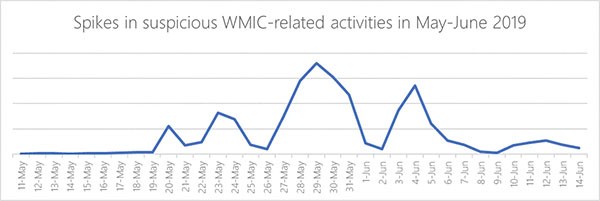
Microsoft also tracked the actions of suspicious Windows Management Instrumentation Console (WMIC) activities showing a spike in the chart below during the end of May 2019, which is a sensitive time that Astaroth was found to ramp up its attack efforts.
Protecting Your Computer from Threats Like the Astaroth Trojan
The best way to ensure that your computer is fully protected from threats like the Astaroth Trojan is to have a security software suite that is fully up-to-date installed on your computer and run regular scans of your PC with it. At present, the Astaroth Trojan campaign' main targets seem to be located in Brazil and Western Europe, and computer users in these regions are advised to be careful when handling any unsolicited email attachment or suspicious online content especially. One of the main aspects of the Astaroth Trojan attack is how it evades detection. Because of this, it is crucial that computer users ensure that their security software is fully up-to-date at all times and use multiple security measures apart from their anti-virus. This can guarantee that even if one security measure is bypassed in the Astaroth Trojan attack, another safeguard exists to ensure that the Astaroth Trojan attack is not carried out.