AiraCrop Ransomware
The AiraCrop Ransomware is a ransomware Trojan that belongs to the Crysis family of threats. Like other ransomware Trojans, the AiraCrop Ransomware is designed to encrypt the victims' files to demand the payment of a ransom. The AiraCrop Ransomware may be distributed by including it as a file attachment in spam email messages frequently. These email messages may appear to come from social media platforms such as Facebook, Twitter and Instagram. Attachments used to deliver the AiraCrop Ransomware may be Microsoft Word files that exploit vulnerabilities in this program's use of macros. These files, with the extension DOCX, will establish a connection to a remote server and download and execute the AiraCrop Ransomware's file onto the victim's computer.
Table of Contents
The AiraCrop Ransomware Encrypts Various File Types
Files that have been encrypted by the AiraCrop Ransomware will have the extension '.the AiraCropencrypted!,' making it easy to know which files have been affected by the AiraCrop Ransomware. The AiraCrop Ransomware will encrypt the victim's files using a strong encryption algorithm, making them inaccessible to the computer users. The AiraCrop Ransomware takes the victim's files hostage, demanding the payment of a ransom in exchange for the decryption key. The AiraCrop Ransomware will encrypt almost 170 different file types. The following are some of the file extensions that are targeted for encryption by the AiraCrop Ransomware Trojan:
.odc, .odm, .odp, .ods, .odt, .docm, .docx, .doc, .odb, .mp4, sql, .7z, .m4a, .rar, .wma, .gdb, .tax, .pkpass, .bc6, .bc7, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps.
After encrypting the victim's files, the AiraCrop Ransomware will drop a ransom note on the victim's computer, demanding the payment of a ransom. The AiraCrop Ransomware will drop a text file on the victim's Desktop, which is named 'How to decrypt your files.txt.' The message inside the AiraCrop Ransomware's ransom note reads:
'Encrypted Files!
All your files are encrypted. Using encryption AES256-bit and RSA-2048-bit.
Making it impossible to recover the files without the correct private key.
If you are interested in getting is key, and retrieve your files
visit one of the links and enter your key;
[links to pages on the TOR Network]
Alternative link:
[links to pages on the TOR Network]
To access the alternate link is mandatory to use the TOR browser available on the link
https://www.torproject.org/download/download
Key:
[a 66-byte long key]'
Dealing with an AiraCrop Ransomware Infection
Victims of the AiraCrop Ransomware are provided with a payment website where they are asked to pay the AiraCrop Ransomware's ransom. The amount demanded by the AiraCrop Ransomware depends on the amount of data that was encrypted by the AiraCrop Ransomware. PC security analysts advise against paying the AiraCrop Ransomware's ransom. There is no reason to believe that the con artists responsible for the AiraCrop Ransomware will provide the decryption means, and even if they do, paying the AiraCrop Ransomware's ransom allows these con artists to continue developing these kinds of threat attacks.
SpyHunter Detects & Remove AiraCrop Ransomware
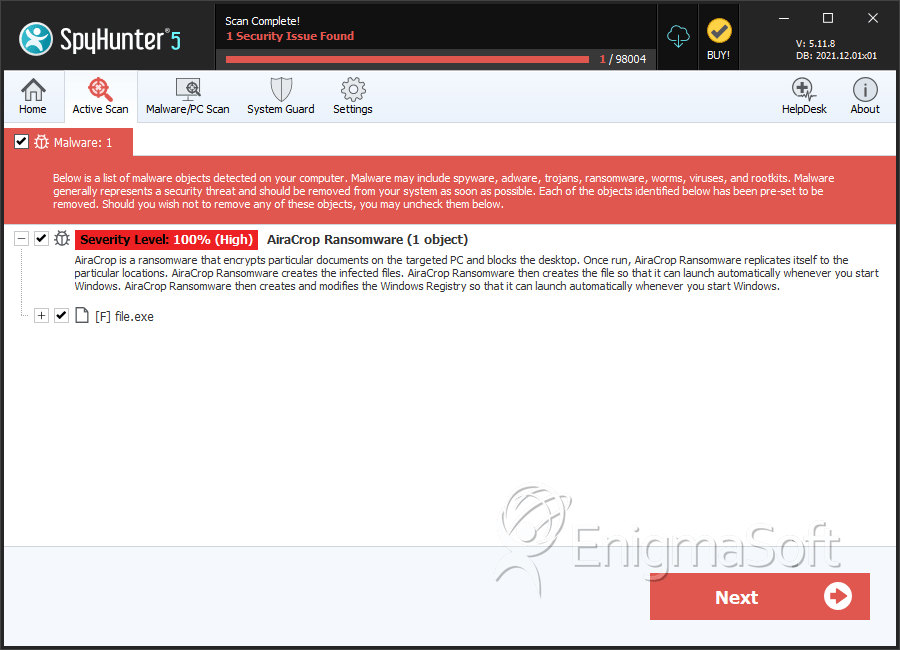
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 54217c1ea3e1d4d3dc024fc740a47757 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.