AES-NI Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | April 21, 2017 |
| Last Seen: | July 4, 2022 |
| OS(es) Affected: | Windows |
The AES-NI Ransomware is a ransomware Trojan that seems to be associated with the use of NSA exploits leaked by the hacking group Shadow Brokers. According to tweets released by the AES-NI Ransomware's creator, a Windows server vulnerability was used to install the AES-NI Ransomware, a low-quality ransomware Trojan. There is one thing clear about these claims; the AES-NI Ransomware has been responsible for numerous attacks in April 2017. Between April 10 and April 22 the detection of the AES-NI Ransomware has been at about 0 to 5 infected systems every day, with more than 100 victims by the end of the measurement period. This spike in infections seems to coincide with the leak of Windows exploits. However, PC security researchers consider that these exploits are not being used to deliver the AES-NI Ransomware, regardless of the con artists' claims. The most likely culprit is Remote Desktop Protocol (RDP), which may be used to carry out attacks by exploiting weak passwords and security protection.
Table of Contents
The AES-NI Ransomware Attack and Its Consequences
There is still doubt in regards to how the AES-NI Ransomware is being delivered to victims. However, it is clear that the AES-NI Ransomware infection is mainly spreading by exploiting vulnerabilities in the system security rather than through the use of corrupted email attachments (a common method used to deliver other ransomware Trojans). PC security researchers have taken steps to curtail the effects of the AES-NI Ransomware attack. Email addresses linked to the AES-NI Ransomware attack also have been blocked, and the operations of the AES-NI Ransomware have been hampered in various ways by malware researchers.
A Quick Look at the AES-NI Ransomware Infection
The AES-NI Ransomware Trojan has been around since at least December 2016 and also may be detected as the AES Ransomware or the AES256 Ransomware, using various aliases in its attack. The ransom note associated with the current the AES-NI Ransomware variant claims that this version is the 'NSA EXPLOIT EDITION' and asks for a ransom of 1.5 BitCoins (approximately $1800 USD at the current exchange rate), also claiming to decrypt files for free for computer users located in countries that on one occasion were members of the Soviet Union. The AES-NI Ransomware attack is strong, and there is no way to recover the files encrypted by the AES-NI Ransomware besides restoring them from a backup currently. PC security researchers strongly advise computer users to have file backups to nullify the effects of the AES-NI Ransomware and other ransomware attacks.
The following is the ransom note associated with this attack:
'==========================# AES-NI Ransomware #==========================
█████╗ ██████╗██████╗ ███╗ ██╗ ██╗
██╔═██╗██╔═══╝██╔═══╝ ████╗ ██║ ██║
██████║█████╗ ██████╗███╗██╔██╗██║ ██║
██╔═██║██╔══╝ ╚═══██║╚══╝██║╚████║ ██║
██║ ██║██████╗██████║ ██║ ╚███║ ██║
╚═╝ ╚═╝╚═════╝╚═════╝ ╚═╝ ╚══╝ ╚═╝
SORRY! Your files are encrypted.
File contents are encrypted with random key (AES-256 bit; ECB mode).
Random key is encrypted with RSA public key (2048 bit).
We STRONGLY RECOMMEND you NOT to use any "decryption tools".
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get RSA private key.
In order to get private key, write here:
0xc030@protonmail.ch
Also there is one fast way to contact us.
If you are familiar with Jabber, write us to JID: zooolo@darknet.nz (it is Jabber, not e-mail address!)
You can get Jabber account for example at https://www.xmpp.jp/signup
IMPORTANT: In some cases malware researchers can block our e-mails.
If you did not receive any answer on e-mail in 48 hours,
please do not panic and write to BitMsg (https://bitmsg.me) address:
BM-2cVgoJS8HPMkjzgDMVNAGg5TG3bb1TcfhN
or create topic on https://www.bleepingcomputer.com/ and we will find you there.
Also it will be better if you download Tor browser here: https://www.torproject.org/download/download-easy.html.en
Download, install and run it; then visit our site (from Tor browser): http://kzg2xa3nsydva3p2.onion/index.php
Please do not visit this site from standard browser: it just will not open. You need Tor Browser to open .onion sites.
There is a form, you can write us there if all e-mails are blocked and we will contact you very fastly.
If someone else offers you files restoring, ask him for test decryption.
Only we can successfully decrypt your files; knowing this can protect you from fraud.
You will receive instructions of what to do next.
You MUST refer this ID in your message:
PC#EB53D6F20CF4C8BDCFD536DE4B29906C
Also you MUST send all ".key.aes_ni" files from C:\ProgramData if there are any.
==========================# AES-NI Ransomware #=========================='
Preventing the AES-NI Ransomware Attacks
If this ransomware Trojan is indeed being delivered using the leaked NSA exploits, then it is crucial to install all security patches and have file backups. Strong security protection and passwords can prevent the attacks that allow con artists to install these threats on the victims' computers.
SpyHunter Detects & Remove AES-NI Ransomware
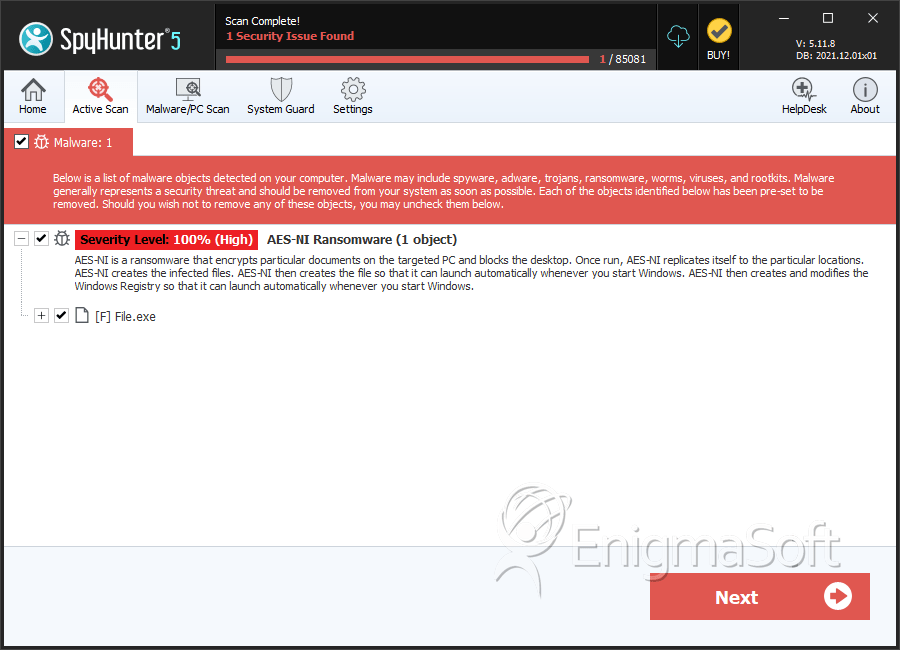
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | File.exe | 83e824c998f321a9179efc5c2cd0a118 | 0 |

