Adrozek Malware
The Adrozek Malware is a new malware strain recently spotted by Microsoft's 365 Defender Research Team. First detected in May 2020, Adrozek infections quickly spread across the globe, peaking at an average high of 30,000 per day in August. To date, Adrozek’s victims may have already gone well above the one million mark. The malware aims to inject sponsored ads into search results and monetize on pay-per-click schemes. To do that, it may dump unwanted browser addons or modify specific DLL and other browser settings to lure unsuspecting users into clicking on those ads, ultimately bringing in revenue for Adrozek’s actors through affiliate advertising platforms.
Table of Contents
Adrozek Has A Global Scope
Adrozek attacks four of the most popular web browsers out there — Microsoft Edge, Mozilla Firefox, Google Chrome, and Yandex. While it has already spread across dozens of countries worldwide, Europe and Southeast Asia have been the focal points of the infection so far.
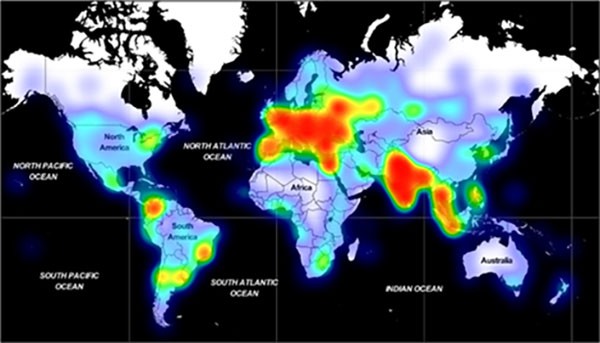
Geographical distribution of Adrozek Malware Infections - Source: Microsoft
The scale of Adrozek infections is grand and shows no signs of slowing down. Adrozek installers usually reach their targets as part of drive-by downloads. The sheer magnitude of the ongoing infection stems from the 159 domains currently hosting hundreds of thousands of polymorphic malware executables. What is more, each of those tracked domains reportedly hosts up to 250 thousand URLs. On average, each domain hosted more than 17 thousand URLs, and each URL contained more than 15 thousand Adrozek installers. Some domains turned out to be active for as long as four months, storing up to 250 thousand URLs. Clicking on an infected URL is all it takes for an Adrozek infection to take effect.
The Actual Infection Chain
Each Adrozek executable stored within an infected URL features obfuscated code and a unique file name that fits the following pattern:
- setup_[random_filename]_[random_numbers].exe
The infection process starts as soon as the targeted user has landed on a URL hosting an Adrozek executable. The latter downloads another executable and places it into the user's Temp folder. That executable contains a primary as well as a secondary payload. The former is an aggressive browser hijacker that affects the four popular browsers mentioned above. It usually comes masked as an audio program — QuickAudio[dot]exe, Audiolava[dot]exe, converter[dot]exe, etc. However, the latter is a password stealer that only hits Mozilla Firefox users with the intent to harvest whatever login credentials it may come across.
The underlying figure provides a detailed overview of the actual Adrozek infection chain.
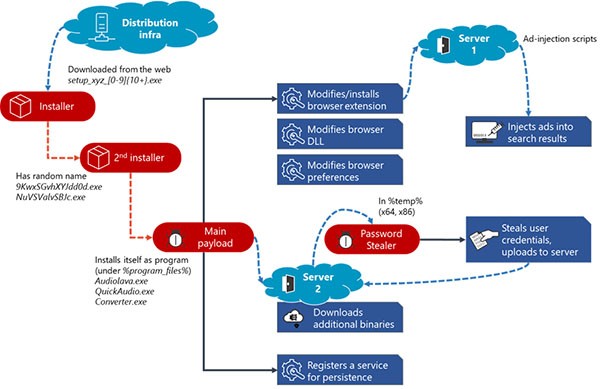
Adrozek Infection Chain - Source: Microsoft
The Main Payload
Although coming under the guise of audio software, the primary Adrozek executable has nothing to do with enhancing your audio settings. Instead, it aims to:
- Modify your browser’s default page, search engine, and new tab.
- Bring in unwanted extensions containing various malicious scripts.
- Change Browser DLLs to bypass security settings.
- Gain persistence by exploiting registry keys.
The changes in your browser settings seek to redirect you to sponsored affiliate-related search results. On the other hand, the unwanted extensions execute the malicious scripts contained therein to set up a connection with a remote C&C server. The latter sends back the scripts responsible for injecting the sponsored ads into the affiliate-related search results.
Here is a juxtaposition between a regular search engine page and an ad-infested, Adrozek-related one:
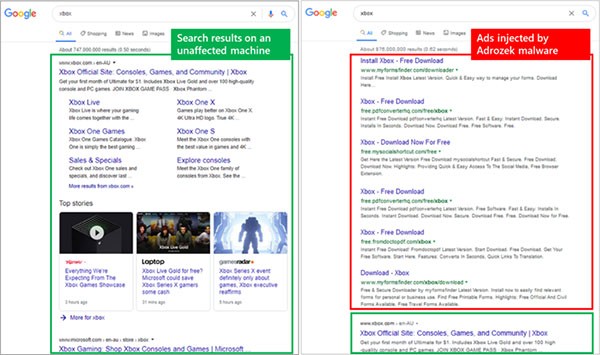
Clean Search Results vs. Adrozek-Related Search Results - Source: Microsoft
Adrozek also tampers with the browser's DLL files that serve as a shield against potential malware attacks. By changing those DLLs, Adrozek disables updates, safe browsing, and integrity checks, practically removing that shield and rendering the browser vulnerable to malicious attacks.
So far, the sponsored web links do not appear to have led any user to a malware-laden site. Instead, the actors at play aim to generate monetary gains from the sponsored ads they promote. However, there is no guarantee that an Adrozek-promoted web ad won't eventually bring you to a dubious domain containing malicious components — such as an Adrozek dropper held on a leash.
The Password Stealer (Firefox-Only)
Should you land on an Adrozek-infected URL from a Firefox browser, you run the risk of losing the login credentials stored on your browser. Adrozek reportedly drops a particular executable specifically made for Firefox browsers. That executable pursues one goal only — to collect all your active logins, saved passwords, and browsing history. Once it has retrieved the targeted data, the stealer sends it over to an external C&C server, exposing it to all sorts of risks.
How to Oppose Adrozek
The vast distribution of Adrozek installers shows that the crooks in charge lay great emphasis on an ad-based revenue model that may prove sustainable in the long term. The polymorphic structure of the payloads paves the way for multi-pronged attacks and varying degrees of damage across millions of devices worldwide. Using robust AV solutions capable of spotting malicious behavior on time will reduce the risk of Adrozek infections to a minimum. Concentrating on known websites and avoiding suspicious-looking links can go a long way towards keeping your device clean, as well.

