ABANTES Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 2,383 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 29,382 |
| First Seen: | December 22, 2018 |
| Last Seen: | September 21, 2023 |
| OS(es) Affected: | Windows |
The ABANTES Ransomware is an encryption ransomware Trojan that was first observed in May 2018. The ABANTES Ransomware has not received wide distribution, even though the ABANTES Ransomware poses a significant threat to computer users. One of the aspects that makes the ABANTES Ransomware quite threatening is that, on the surface, the ABANTES Ransomware behaves like a prank program, or a mere screen locker (typical of low-tier threats). However, the ABANTES Ransomware is carrying out an encryption ransomware attack in the background, an advanced attack type that causes irreparable damage to the victim's data.
Table of Contents
How the ABANTES Ransomware Attacks a Computer
The ABANTES Ransomware has two aspects in its attack; a screen locker, a visual component, and the attack that it carries out in the background. The ABANTES Ransomware typically targets computers running the Windows operating system. The ABANTES Ransomware is optimized to carry out its attack in the Windows 7, but the ABANTES Ransomware is capable of infecting more recent versions of Windows as well. The ABANTES Ransomware's attack will display a program window named 'rules' and change the mouse pointer icon. The ABANTES Ransomware will replace the Desktop wallpaper image with a scary picture of a clown and replace icons on the infected computer with a red square that says 'abantes was here' in black lettering. The 'rules' program window associated with the ABANTES Ransomware contains the following message:
'Rules:
1. Don't Try To Kill Any Processes
2. Don't Try To Edit Entries In MSCONFIG
4. Don't Scan Your PC With A Antivirus
Because It May Delete Virus Files and Your PC Will Die
If You Break The Rules
Your PC Will Become Unusable'
This all seems typical of scareware or screen locker threats, merely blocking access to the victim's computer and displaying scary messages. However, the ABANTES Ransomware will use a strong encryption algorithm to encrypt the victim's files in the background, to take them hostage. While the victim is trying to bypass the ABANTES Ransomware program window, the ABANTES Ransomware will target the user-generated files in its attack, encrypting numerous media files, databases and other documents. The ABANTES Ransomware targets data that may include files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar
Protecting Your Data from the ABANTES Ransomware
While using Safe Mode you can bypass the ABANTES Ransomware screen locker component, the files encrypted by the ABANTES Ransomware will not be recoverable without a decryption key. Because of this, as with most encryption ransomware Trojans, the best protection for computer users is to have backup copies of all of their data and store these copies on safe places such as the cloud.
SpyHunter Detects & Remove ABANTES Ransomware
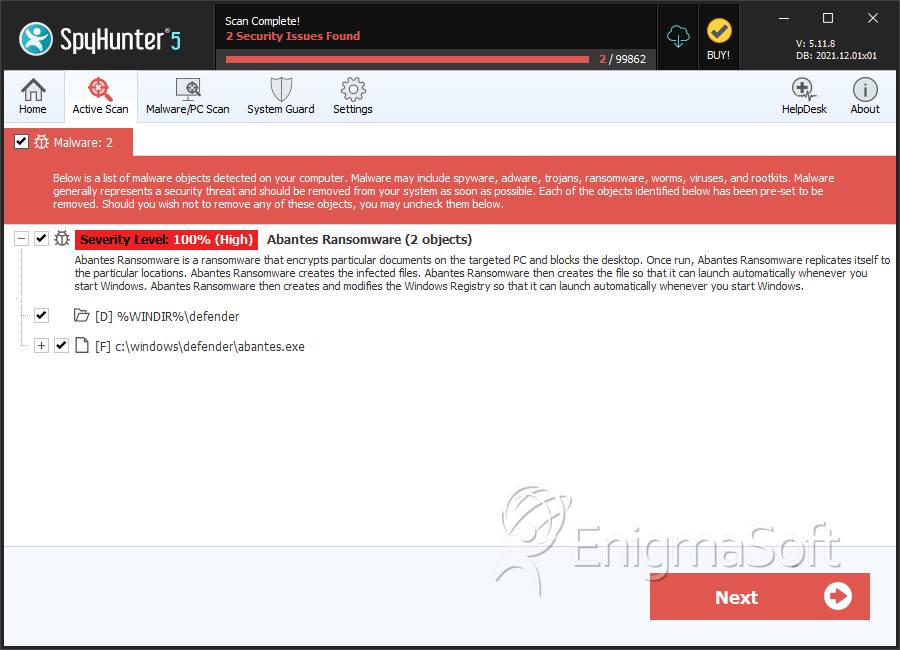
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | abantes.exe | 310b76bb435464213aaf2106f205df5b | 1 |
Directories
ABANTES Ransomware may create the following directory or directories:
| %WINDIR%\defender |

