7h9r Ransomware
The 7h9r Ransomware is an encryption ransomware Trojan that has claimed numerous victims. The 7h9r Ransomware uses a very strong encryption algorithm to encrypt the victim's files. After encrypting the victim's files, the 7h9r Ransomware demands the payment of a ransom by dropping a ransom note that asks that victims contact the email address 7h9r341@gmail.com to receive instructions on how to pay the ransom. Infected computer users should remove the 7h9r Ransomware Trojan immediately with the help of a reliable security program that is fully up-to-date. The bad news is that infected computer users may not be capable of decrypting the files encrypted with the 7h9r Ransomware without access to the decryption key currently. However, it is possible that a decryption utility may be released by PC security analysts eventually.
Table of Contents
The Infection Vectors Utilized by the 7h9r Ransomware
The most common way of distributing the 7h9r Ransomware is through corrupted email spam attachments. In some cases, the 7h9r Ransomware will bypass email services that scan and block threatening attachments by embedding links that redirect computer users to attack websites. When computer users are directed to these websites, the 7h9r Ransomware is installed automatically. It is also possible that the 7h9r Ransomware could be installed using corrupted JavaScripts or an exploit kit that leverages vulnerabilities on the victims' computers.
How the 7h9r Ransomware Carries out Its Attack
After being installed, the 7h9r Ransomware drops its threatening executable file on the victim's computer and makes changes to the Windows Registry. These changes allow the 7h9r Ransomware to run automatically as soon as Windows starts up. The 7h9r Ransomware is designed to encrypt the victim's files. The 7h9r Ransomware scans all the drives on the infected computer for files with the following extensions:
.3gp .apk .asm .avi .bmp .cdr .cer .chm .ckp .conf .cpp .css .csv .dacpac .dat .db3 .dbf .dbx .dcx .djvu .doc .docm .docx .epub .fb2 .flv .gif .ibooks .iso .java .jpeg .jpg .key .md2 .mdb .mdf .mht .mhtm .mkv .mobi .mov .mp3 .mp4 .mpeg .mpg .mrg .pdf .php .pict .pkg .png .pps .ppsx .ppt .pptx .psd .rar .rbw .rtf .sav .scr .sql .sqlite .sqlite3 .sqlitedb .swf .tbl .tif .tiff .torrent .txt .vsd .wmv .xls .xlsx .xml .xps .zip.
The 7h9r Ransomware encrypts files with the above extensions using an advanced encryption algorithm. The 7h9r Ransomware appends the extension '.the 7h9r' to all files that it encrypts. The 7h9r Ransomware also drops a file named 'README_.txt' in each directory where it encrypts a file. The following is the short message that is included in the ransom note:
'Your files were encrypted. If you want to decrypt them you must send code WE8765twx1009jdR|742|0|2 to email the 7h9r341@gmail.com.
Then you will receive all necessary instructions. Attempts to decipher on their own will not lead to anything good, except irretrievable loss of information.
If you still want try to decipher them, please make a copy of files, this is our life hacking for you. (If you change the file we can’t decrypt them in future)''
When computer users contact this email address, they are asked to make a payment using BitCoins. There is a certain element of negotiation, and the payment amount tends to vary, depending on the desperation of the victim and the severity of the infection.
Preventing the 7h9r Ransomware Infections
These infections can be prevented by making sure to follow good security practices. Computer users should avoid unsolicited email attachments or visit websites or file sharing networks that are associated with threats commonly. The most important steps computer users can take to become invulnerable to encryption Trojans is to keep a backup of all files on an external device or the cloud. This way, computer users can recover the encrypted files by restoring them from the backup copies, rather than paying a large ransom. A reliable security program also can intercept this threat before the 7h9r Ransomware enters a computer.
SpyHunter Detects & Remove 7h9r Ransomware
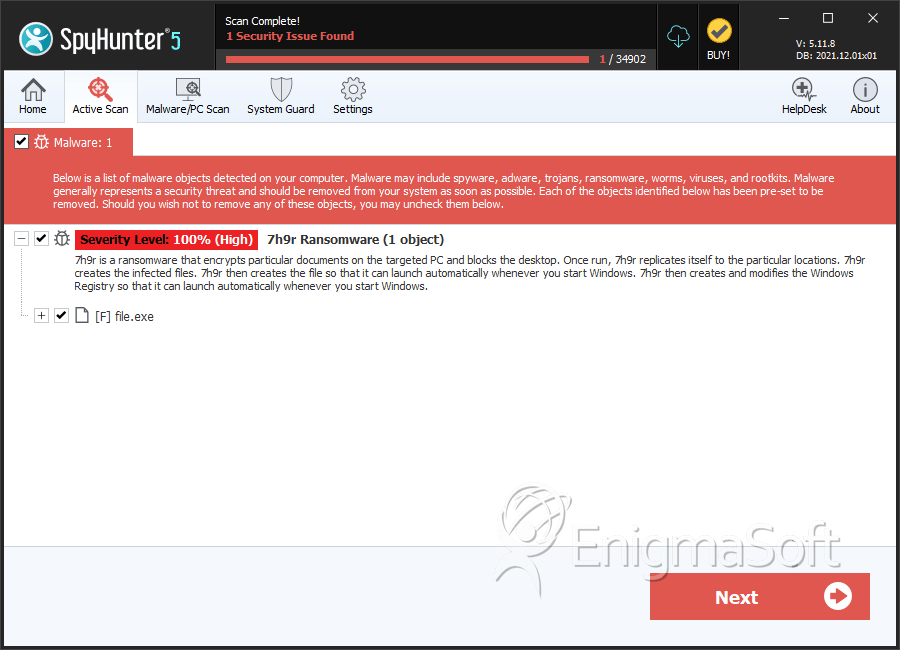
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | c0b834f87051efead202bcec26501444 | 0 |

