Windows Easy Warden
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 11,299 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 11,926 |
| First Seen: | July 12, 2011 |
| Last Seen: | July 25, 2023 |
| OS(es) Affected: | Windows |
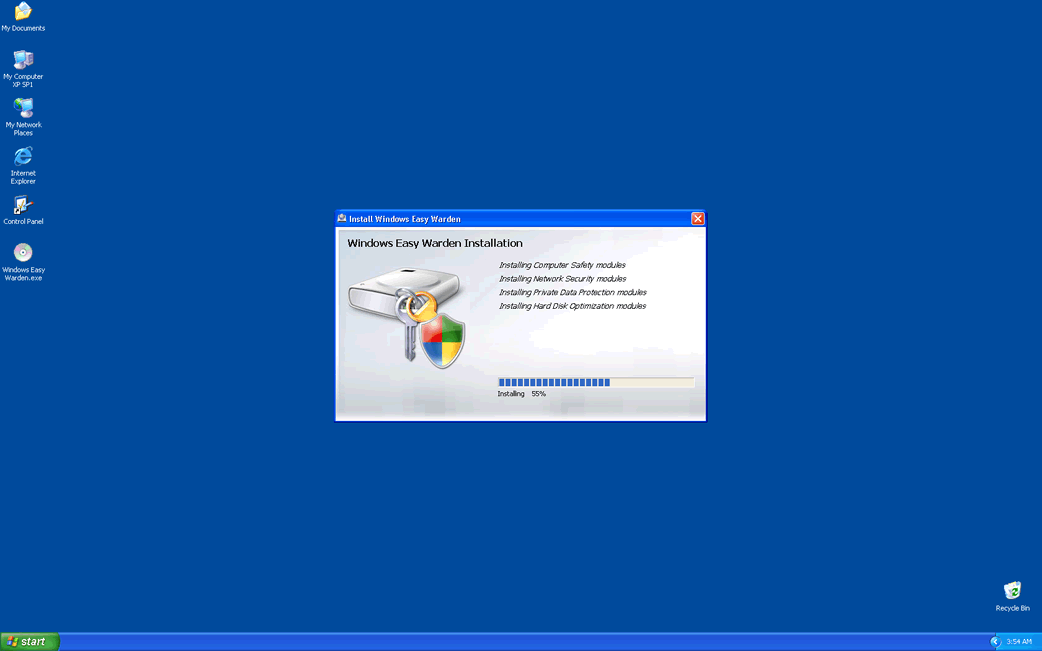
Windows Easy Warden Image
vWindows Easy Warden is a fake security program from a large family of rogue anti-spyware applications, the family. Windows Easy Warden mimics a legitimate security utility as part of a scam. The Windows Easy Warden scam consists in convincing the computer user that his/her computer is in danger. Then, Windows Easy Warden will aggressively push the computer user towards buying a "full version" of Windows Easy Warden. Since the real infection on the computer is Windows Easy Warden itself, paying for a "full version" is nothing more than a waste of money. Malware researchers recommend that you automatically remove Windows Easy Warden with a legitimate anti-malware tool.
Table of Contents
There Are a Huge Amount of Windows Easy Warden Clones
Windows Easy Warden belongs to a large family of rogue security programs. PC security analysts have found that all of these clones share extremely similar interfaces and affect computer systems in the same way. The only thing that changes from clone to clone is the program's name, which is displayed on the upper left corner of the interface. Even then, most Windows Easy Warden clones are made up of three words, with the first being "Windows" and the other two being security-related words that can go from the utterly nonsensical (e.g. Windows Proofness Guarantor) to the somewhat plausible (e.g. Windows Cleaning Tool). Clones of Windows Easy Warden include
Windows Easy Warden is Delivered by a Trojan
Malware researchers have found that Windows Easy Warden is delivered by the Fake Microsoft Security Essentials Alert Trojan. This Trojan receives its name from the fact that it shows a fake alert from Microsoft Security Essentials. This alert will typically indicate that the Unknown Win32/Trojan is present on the affected computer. It will then prompt the computer user to remove this supposed Trojan infection with Windows Easy Warden. To avoid being infected with the Fake Microsoft Security Essentials Alert Trojan, malware researchers recommend that computer users take extra care while browsing. This includes avoiding high-risk websites, not clicking on unknown links and avoiding downloads from unknown or unreliable sources.
Remove Windows Easy Warden Immediately
PC security specialists have identified Windows Easy Warden as a dangerous rogue. This program can potentially take over an infected computer, rendering it useless for practical use. Malware researchers agree that manual removal is not recommended without advanced computer knowledge. The best way to remove Windows Easy Warden is to use a legitimate anti-malware tool after starting up Windows in Safe Mode.
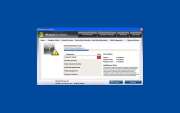
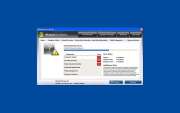
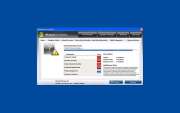
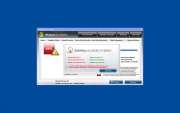
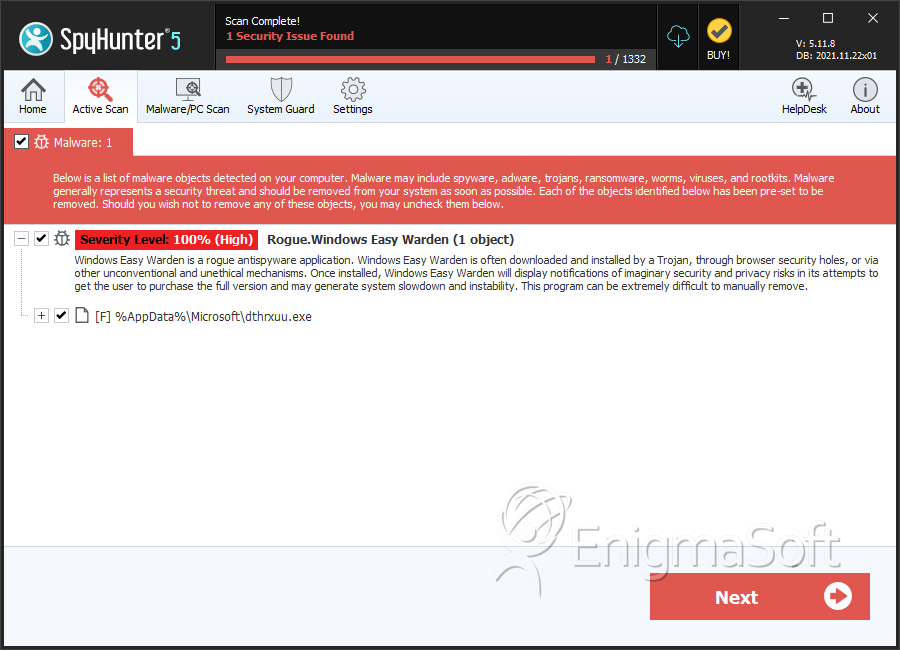
SpyHunter Detects & Remove Windows Easy Warden
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | dthrxuu.exe | 498cc2698b39ddd0e232930ff1783465 | 1 |
| 2. | %UserProfile%\Application Data\Microsoft\.exe |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.