Windows Cleaning Tool
Windows Cleaning Tool is a rogue anti-spyware program from what is now known as the fake Microsoft Security Essentials Alert scam. Windows Cleaning Tool is essentially the same application as Windows Monitoring Utility, Windows Trouble Solver, and dozens of other similar applications. All of these clones have what is basically the same interface with only some minor changes. This is a feature that can be used to recognize programs in the fake Microsoft Security Essentials alert family, like Windows Cleaning Tool. Windows Cleaning Tool is thought to originate from the Russian Federation, in the European Union, and became widespread in 2012.
Table of Contents
How Windows Cleaning Tool Tries to Steal Your Money
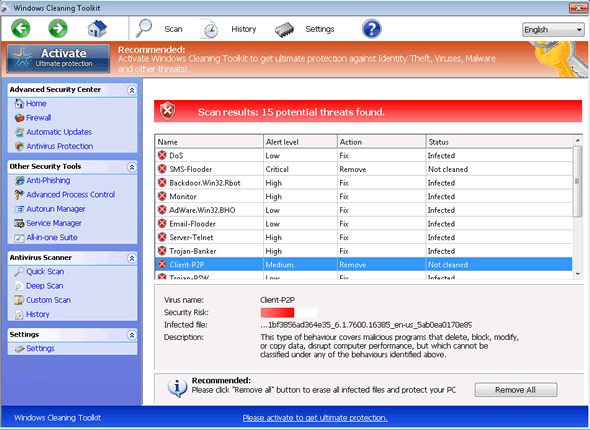
Windows Cleaning Tool is designed to scare users into giving this rogue security program their credit card details. The way Windows Cleaning Tool works is by displaying fake security alerts from Microsoft Security Essentials and performing fake system scans. The results of these invariably show dozens of viral infections on the computer system, often displaying processes that are completely harmless or even essential for the computer to function properly. The program will then tell the user that to remove these infections it is necessary to purchase a specific anti-spyware program, in this case Windows Cleaning Tool. In reality, this program does not have the least capacity for removing spyware or viruses. Windows Cleaning Tool is simply a program designed to receive the user's credit card information and relay it to a third party. Windows Cleaning Tool does not remove spyware or viruses in any way. What Windows Cleaning Tool does do is make a computer system useless. Windows Cleaning Tool uses a Trojan tol block access to the Internet, block access to essential programs and files, and slow down the computer's performance. Entering one's credit card information will not help at all, and should not be done under any circumstances. If you already have, if you move fast and call your credit card company, you may be able to prevent the charges.
How Did Windows Cleaning Tool Enter Your Computer?
Programs like Windows Cleaning Tool are usually delivered through a Trojan. This is a kind of program that exploits security vulnerabilities to enter a computer system and deliver a harmful application; this is usually a virus, adware, spyware, or some other sort of malicious software. Trojans are usually acquired by visiting infected websites or using a corrupted flash application. Some commons sources of infection are adult video sites, which instead of playing a video, deliver a Trojan into your computer and disguised files in file sharing networks. Other ways of infecting your computer with rogue anti-spyware programs like Windows Cleaning Tool are by opening email attachments from un unknown source and clicking on free online computer scans.
How Can You Prevent Being Infected with Windows Cleaning Tool?
The best thing you can do is running a legitimate anti-virus or anti-spyware utility on your computer. You can also avoid infection by using common sense when browsing the Internet. Follow these simple guidelines to reduce drastically your chances of being infected by Windows Cleaning Tool:
- Don't open email attachments from unknown sources.
- Avoid potentially harmful websites, like adult video websites and file sharing networks.
- Don't use free online computer performance scans. Use your legitimate security programs to scan your computer instead.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %UserProfile%\Application Data\Microsoft\[RANDOM CHARACTERS].exe |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.