Windows Activity Inspector
Windows Activity Inspector Image
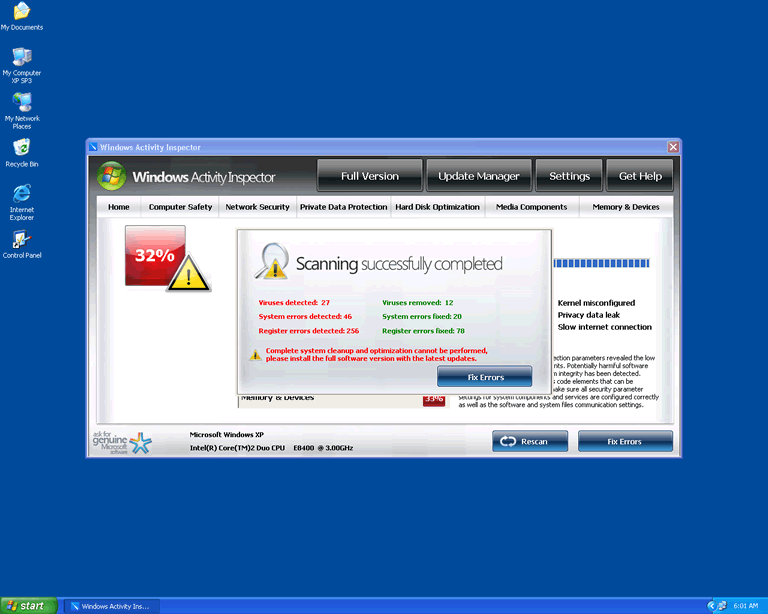
Windows Activity Inspector is just one more addition to the already huge family of rogue anti-spyware programs delivered by the Fake Microsoft Security Essentials Alert Trojan. Programs like Windows Activity Inspector take over a computer system and cause numerous harmful changes to its operation. These programs do this to blackmail the computer user into buying a fake security solution (in this case Windows Activity Inspector) supposedly to get rid of the problem. Don't fall for the scam; Windows Activity Inspector is a malicious application that should be removed immediately.
Table of Contents
Windows Activity Inspector and the Fake Microsoft Security Essentials Alert Family
Windows Activity Inspector belongs to the Fake Microsoft Security Essentials Alert family of rogue programs. This family of rogue anti-spyware applications gets its name because programs in it are typically delivered by the same Trojan. This Trojan causes the infected computer system to display a fake alert from Microsoft Security Essentials. This fake alert will usually say that a Trojan has been discovered on the computer system and that the computer user should download Windows Activity Inspector (or any other program in this group of rogue programs) to remove the Trojan. If the computer user mistakes this fake Microsoft Security Essentials alert for the real thing and downloads Windows Activity Inspector, this rogue security program will immediately proceed to take over the infected computer system.
How Windows Activity Inspector Disrupts Your Computer System’s Operation
Windows Activity Inspector makes several harmful changes to your computer. These are meant to cause panic and to make the removal of Windows Activity Inspector as difficult as possible. Some typical effects of Windows Activity Inspector include the following:
- Constant pop-up notifications and fake security alerts.
- System instability and decreased performance.
- Files that are suddenly blocked or hidden.
- Changes to Internet browser settings or blocked access to the Internet.
Removing Windows Activity Inspector
Windows Activity Inspector doesn't make it easy for computer users to remove Windows Activity Inspector. However, you can bypass most of Windows Activity Inspector's self-preservation measures by starting up Windows in Safe Mode. To start up in Safe Mode, all you need to do is press the F8 key when starting up. Then choose "Safe Mode" from the list of available options. Once you have gained access to your files, it is simply a matter of starting up your anti-malware utility to remove Windows Activity Inspector and Windows Activity Inspector's associated Trojans.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %UserProfile%\Application Data\Microsoft\.exe |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.