Win 7 Internet Security 2012
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 16 |
| First Seen: | December 14, 2011 |
| Last Seen: | November 15, 2020 |
| OS(es) Affected: | Windows |
Win 7 Internet Security 2012 Image
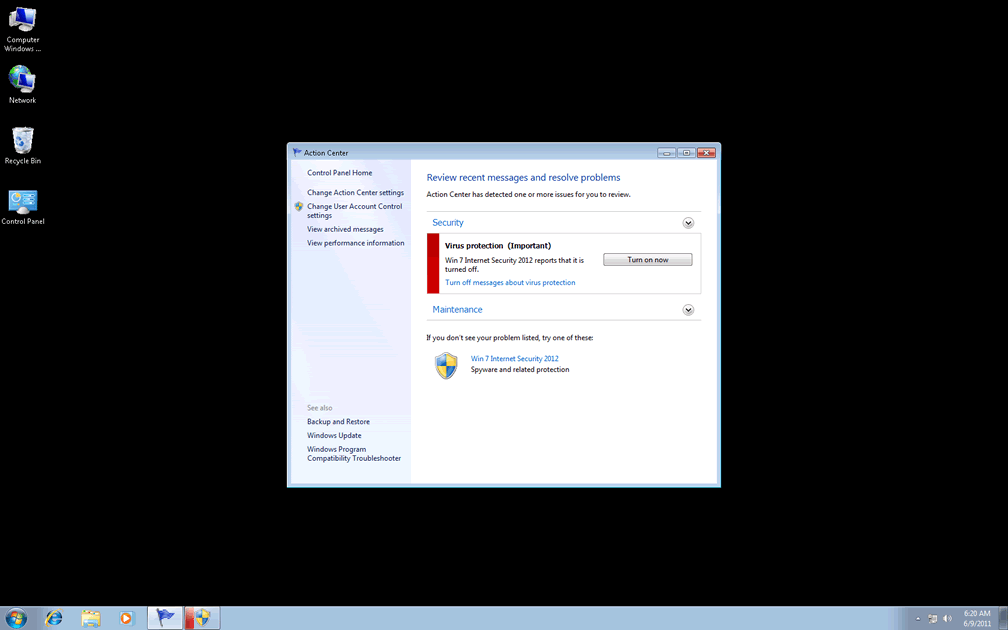
Win 7 Internet Security 2012 is a fraudulent security tool that will be installed on the corrupted computer system by simulating as an update for Windows security. When installed successfully, Win 7 Internet Security 2012 will configure itself to run automatically by adding its own entry on Windows registry. Win 7 Internet Security 2012 may gain control of the affected computer and command its operation to reroute a web browser to malicious websites. Win 7 Internet Security 2012 will block your Internet browser too. Each attempt to open a web browser will be accompanied by an alerting report about Trojan-BNK.Win32.Keylogger.gen infection supposedly keeping you from going online and using the Internet services via your web browser. That's tricky as well because there is no such thing as that computer trojan on your computer system. This web browser blocking is a part of the same routine as the already mentioned scanning and ad creating activity.
Win 7 Internet Security 2012 lures PC users and gives an impression of something you can rely on. Win 7 Internet Security 2012 scans your computer system but at the same time does not really check it for potential security threats. It means these reports following each scanner are full of malware infections listed in a long list. Even if you have a brand-new computer system, Win 7 Internet Security 2012 still warns you of numerous viruses in there. Win 7 Internet Security 2012 will be performing its bogus scanning activity with pop-up ads that do not actually reflect the real condition of your PC either. You should not ever trust Win 7 Internet Security 2012 and nor should you agree to its terms when it gets to type of helping you repair the PC and clean it of the imaginary malware threats. So the recommendations from Win 7 Internet Security 2012 to purchase its so-called licensed version should to be rejected. You need to uninstall Win 7 Internet Security 2012 without delay.
Table of Contents
Win 7 Internet Security 2012 Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Local\[RANDOM CHARACTERS].exe | |
| 2. | %AppData%\Local\[RANDOM CHARACTERS] | |
| 3. | %AllUsersProfile%\[RANDOM CHARACTERS] | |
| 4. | %Temp%\[RANDOM CHARACTERS] | |
| 5. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.