Win 7 Home Security 2012
Win 7 Home Security 2012 Image
Since early 2011, the Ppn.exe file process has become increasingly widespread. This malicious file created in the Russian Federation, has infected a great number of computers all over the world. Win 7 Home Security 2012 is one of many different names the Ppn.exe file can take. The thing that makes Ppn.exe unique is how it constantly shifts disguises. Win 7 Home Security 2012 is one of the masks this file wears when infecting a computer system running the Windows 7 operating system.
Table of Contents
Understanding the Purpose of Win 7 Home Security 2012
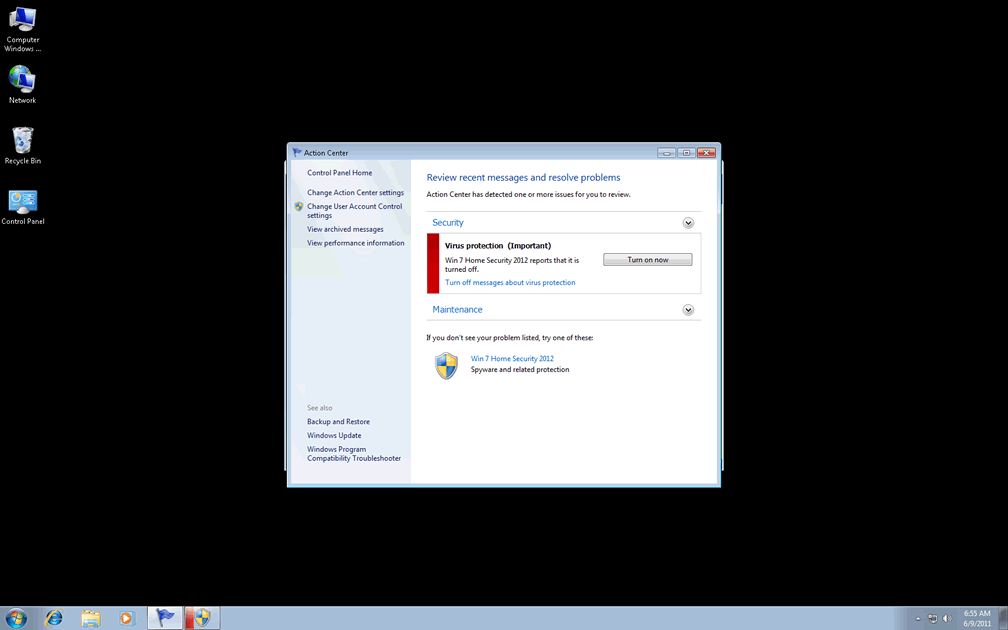
Ignore this application's name; even though "Win 7 Home Security 2012" sounds like what a real security application would be named, Win 7 Home Security 2012 is a clever counterfeit. Win 7 Home Security 2012 is what is known as a rogue security application. Win 7 Home Security 2012 is a kind of malicious software known as scareware. This denomination comes from the program's purpose. Win 7 Home Security 2012 is designed to work in a predatory way. Win 7 Home Security 2012 targets inexperienced computer users by using Trojans and malicious scripts to cause all kinds of problems with a computer system. Win 7 Home Security 2012 will then pose as a real security application. Win 7 Home Security 2012 does this to scare the computer user into thinking that Win 7 Home Security 2012 has detected a great number of problems on the machine. In fact, the thing causing constant pop-ups and performance problems is Win 7 Home Security 2012 itself. The final objective of this program is to have the computer user give Win 7 Home Security 2012 his credit card information. This would be done to purchase a license to use the program for supposedly fixing the computer. Since Ppn.exe, wearing the Win 7 Home Security 2012 mask has no way of fixing computer problems, all Win 7 Home Security 2012 will do is steal the credit card information and leave a damaged computer behind.
The Thing that Makes Win 7 Home Security 2012 Unique
While most rogue anti-spyware or rogue security applications have many clones (identical copies of the same program with different names), all of the versions of Ppn.exe are essentially the same file. Ppn.exe, sometimes named Kdn.exe, changes masks depending on the operating system it is infecting. When being installed, it will access a repository of skins and themes and download one corresponding to the infected operating system. There are three sets of skins for the Ppn.exe file process, one corresponding for each of the most used Windows operating systems (Windows XP, Windows Vista, and Windows 7.) As Win 7 Home Security 2012's name says, Win 7 Home Security 2012 is one of the possible skins from the Windows 7 set.
Actions You Can Take To Avoid Downloading Win 7 Home Security 2012
- Be careful when browsing the Web. This means avoiding high risk websites, like adult video sites and file sharing networks.
- Use a trusty anti-virus or anti-spyware application. These should come from a trusted source.
- Don't trust free online malware scans, or banner advertisements claiming that there are performance problems on your computer.
- Don't open email attachments from unknown sources and avoid downloading files if you are not absolutely sure about what they contain.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | [RANDOM CHARACTERS].exe | |
| 2. | %AppData%\Local\[random].exe | |
| 3. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] | |
| 4. | Uninstall Win 7 Home Security 2012.lnk | |
| 5. | %AppData%\Local\[RANDOM CHARACTERS] | |
| 6. | Win 7 Home Security 2012.lnk | |
| 7. | %AllUsersProfile%\[random] | |
| 8. | %Temp%\[RANDOM CHARACTERS] |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.