Win32/TrojanDownloader.Zurgop.AZ
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 588 |
| First Seen: | August 22, 2013 |
| Last Seen: | December 24, 2023 |
| OS(es) Affected: | Windows |
Win32/TrojanDownloader.Zurgop.AZ is one of the names by which the Smoke malware loader or Trojan loader is known. This malware infection has been around for quite a long time, with a major period of activity in Spring of 2012. However, the use of Win32/TrojanDownloader.Zurgop.AZ in association with several other malware scams, including the dangerous Avatar rootkit which first made its appearance in Summer of 2013.
There is a constant race between criminals and malware researchers, with the former creating more resilient, self-protecting malware to combat new developments in security software created by the latter. The goal of criminals is to create malware that can thwart removal and analysis while attacking new platforms and exploiting new vulnerabilities in software used by a wide variety of people. Win32/TrojanDownloader.Zurgop.AZ is created with various modules, which can be purchased separately from the creators of this malware threat. Win32/TrojanDownloader.Zurgop.AZ is a severe threat to your computer and a strong anti-malware application should be used to ensure that this malware threat does not threaten your computer.
Table of Contents
The Dangerous Features of Win32/TrojanDownloader.Zurgop.AZ Loader
Security analysts have a clear idea of Win32/TrojanDownloader.Zurgop.AZ's features because they are prominently featured on underground forums where people can purchase Win32/TrojanDownloader.Zurgop.AZ in order to carry attacks. The following are some of the features that may be integrated into Win32/TrojanDownloader.Zurgop.AZ:
- Win32/TrojanDownloader.Zurgop.AZ can be used to target computer systems in a particular geographical region, which makes it ideal for delivering police ransomware threats and other location-sensitive infections.
- Win32/TrojanDownloader.Zurgop.AZ can hide its activities by concealing itself behind a trusted memory process.
- Win32/TrojanDownloader.Zurgop.AZ allows its controller to keep track of several statistics, which may then be useful in carrying out further attacks or controlling the victim's computer.
- Win32/TrojanDownloader.Zurgop.AZ is quite small, often less than 15KB in size.
- Win32/TrojanDownloader.Zurgop.AZ may be used to steal passwords and login credentials for a large list of popular applications and Web services.
- Win32/TrojanDownloader.Zurgop.AZ may also be used to turn the infected computer into a kind of proxy server, allowing criminals to carry out their online activities anonymously.
Due to the fact that Win32/TrojanDownloader.Zurgop.AZ can extract passwords from your Web browser and other applications, ESG security analysts strongly advise against storing your passwords on your Web browser and making sure to handle your login information carefully.
SpyHunter Detects & Remove Win32/TrojanDownloader.Zurgop.AZ
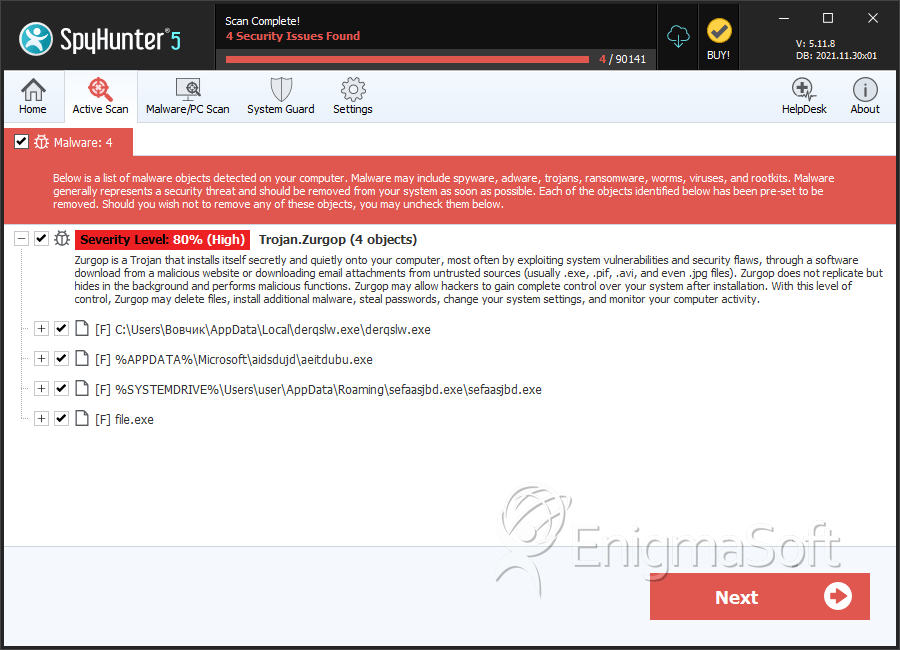
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | derqslw.exe | f1e0b3adc0466a38ab590507ce87a453 | 12 |
| 2. | sefaasjbd.exe | 7304109f82cb8149e3b8eaff5264bd4f | 2 |
| 3. | aeitdubu.exe | 5dd4523222b81697472beb907832c6ed | 1 |
| 4. | %appdata%\%variable1%\%variable2%.exe | ||
| 5. | %startup%\%variable2%.lnk | ||
| 6. | file.exe | 40091059896624e1395aff51325ac90d | 0 |
