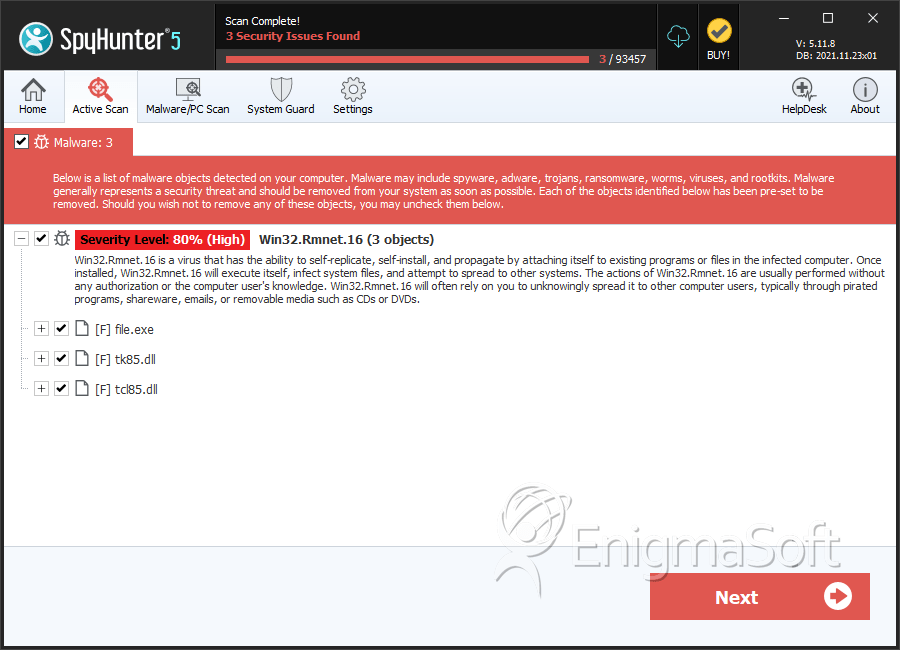
Win32.Rmnet.16
Win32.Rmnet.16 is a virus that uses a digital signature to sign control server IP-addresses which are no longer inserted in the malicious program resources but created using a special routine. Additionally, the module can end processes of the majority of well-known anti-virus software, which makes Win32.Rmnet.16 more hazardous. Win32.Rmnet.16 is written in C and Assembly and is composed of a few functional modules. The injector that dislocates Win32.Rmnet.16 in the computer system injects its code into browser processes, saves its driver into a temporary folder and runs it as a Microsoft Windows Service. Then, the injector copies the body of Win32.Rmnet.16 into a temporary directory and startup folder. The body file has a random name and the extension .exe. The backdoor payload of Win32.Rmnet.16 can accomplish commands obtained from a remote server, specifically, to drop and execute arbitrary files, update itself, to take screenshots and transfer them to cyber-crooks, and even make the affected PC system non-operational. Win32.Rmnet.16 can alter the MBR and encrypt and save its files at the end of the disk. After restarting, control is sent to malicious code in the affected boot record, which reads and decrypts modules in the memory and then runs them. Get rid of Win32.Rmnet.16 as early as possible.
SpyHunter Detects & Remove Win32.Rmnet.16
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 20cf03337dcc36caeadd560f0763234a | 0 |
| 2. | file.exe | 3fa4b347a707a6397817496563f624db | 0 |
| 3. | tk85.dll | c7fd191cb40819c8aec4cce070f6e06e | 0 |
| 4. | tcl85.dll | 25199b2fbcf6c75657c0d49b66d94af2 | 0 |
| 5. | file.exe | 851394f4f760cda9409e40f4b8006ae7 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.