Win32/Redyms
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 4 |
| First Seen: | March 19, 2013 |
| Last Seen: | March 26, 2020 |
| OS(es) Affected: | Windows |
Win32/Redyms is a family of browser hijacking Trojans that are associated with extremely dangerous malware, including versions of the TDL4 Rootkit and the Black Hole Exploit Kit. Malware in the Win32/Redyms family were first detected in January of 2013, although ESG security researchers note that it is highly likely that Win32/Redyms is derived from previous browser hijackers that have been active for years. Win32/Redyms poses a severe threat to a targeted computer and that any Trojan in this family should be deleted quickly with the help of a reliable anti-malware program. Fortunately, Win32/Redyms' avenues or attack are well known, and most security programs are well equipped to handle this threat. However, due to the fact that Win32/Redyms Trojans are relatively new, it is important to ensure that your security software is fully updated in order to remain protected from Trojans in Win32/Redyms' family.
Table of Contents
Common Symptoms Associated with a Win32/Redyms Infection
Win32/Redyms and its clones are easily detected because they are designed to redirect search engine results. This means that, after carrying out a search on Google, Yahoo, MSN Search, Bing or any other common search engine, Win32/Redyms Trojans will change the search result links so that they lead the computer user to other websites rather than to the web pages corresponding to the search results. Typically, Win32/Redyms will lead computer users to fake search engines designed to display sponsored search results. Inexperienced computer users may think that this is a normal occurrence, meaning that they are more likely to ignore the browser redirect and simply try, once more, to do their search on the malicious search engine that appeared as a result of the Win32/Redyms redirect. This exposes the victim's computer to additional malware and also allows criminals to profit greatly from advertising and affiliate marketing links.
Common Ways Criminals Use to Distribute Win32/Redyms Trojans
The most common file download that results in a Win32/Redyms infection is a fake installer for Adobe Flash. This is often downloaded after clicking on a malicious link distributed through social media spam. For example, a link may be passed around on Facebook claiming to lead to a racy video depicting a nude or controversial scene. However, when the computer user tries to watch the video, Win32/Redyms will indicate that Adobe Flash is not installed or claim that it is necessary to update Flash, 'helpfully' letting the computer user download the fake installer directly from the error message or leading the computer user to a phishing website designed to look identical to the Adobe Flash installer download page. Win32/Redyms Trojans are also commonly distributed through attack websites containing the Black Hole Exploit Kit.
SpyHunter Detects & Remove Win32/Redyms
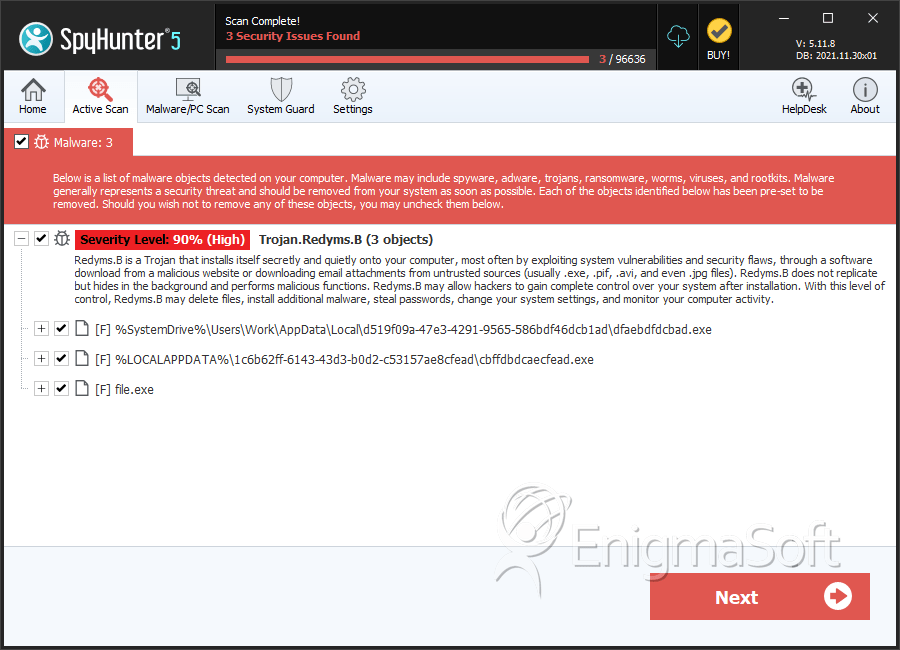
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | cbffdbdcaecfead.exe | 5fb8983f2c729cb8dd9c2d62ba4d84b0 | 1 |
| 2. | file.exe | 685250a844ffda0bd522ef4a3e1fae6e | 0 |
| 3. | file.exe | 0044d66e4abf7c4af6b5d207065320f7 | 0 |
| 4. | file.exe | a647dcd2f7d5d60b4e96c21aa2af1939 | 0 |
| 5. | file.exe | b513c1cd1f6cb11b39276b5eb61877e2 | 0 |
| 6. | file.exe | f4a4f984cdd2687d5d9b741f74cc60a5 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.