Win32/Hioles
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 1 |
| First Seen: | March 14, 2012 |
| OS(es) Affected: | Windows |
Win32/Hioles is a relatively new malware infection which was first detected in early 2012. Microsoft has already released new patches protecting computer from this threat, which PC security analysts have classified as severe. To protect yourself from Win32/Hioles and other recent malware threats, ESG malware researchers recommend that you maintain your system and anti-virus software always refreshed so it can be provided with the latest malware definitions. Win32/Hioles in particular is a Trojan infection that opens a backdoor in the infected computer system's security. Then, using this opening, Win32/Hioles establishes a connection with a remote server. Through this link, criminals can instruct Win32/Hioles to download and install other malware, which can allow the infected computer system to fall under the control of criminals or to become part of a large botnet. Often, the only symptoms linked to a Win32/Hioles infection will be notifications from your security software, which makes it essential to ensure that your security software is updated so it will detect this threat.
Table of Contents
How the Win32/Hioles Trojan Attacks Your Computer System
Win32/Hioles can take a couple of different forms. ESG security analysts have found that the most common versions of the Win32/Hioles Trojan exists as an EXE executable file or as a Dynamic Library Link file with a DLL extension. The EXE file associated with the Win32/Hioles tends to use a name composed of the letters 'kb' followed with six random numbers. The EXE version of the Win32/Hioles Trojan can also be named svchost, like the common Windows file process. The DLL version of the Win32/Hioles Trojan will usually have a random name and will be loaded in the System32 folder or in the AppData folder. In both cases, the Win32/Hioles Trojan changes the Windows Registry so that it will run Win32/Hioles automatically upon start-up.
ESG security analysts have observed several malicious domains from which Win32/Hioles can receive its commands (such as gogogobaby12(dot)com or grabsfakus(dot)com). Win32/Hioles can then serve as a reverse proxy, that is, criminals can use the infected computer in order to register an email account in order to send out spam email, visit malicious websites, or carry out other criminal activities. To avoid a Win32/Hioles infection, ESG malware analysts recommend using a reliable anti-malware program; ensuring that your operating system, anti-malware software and firewall are fully updated; and avoiding websites typically regarded as unsafe (for example, pornographic websites or websites containing illegal content).
SpyHunter Detects & Remove Win32/Hioles
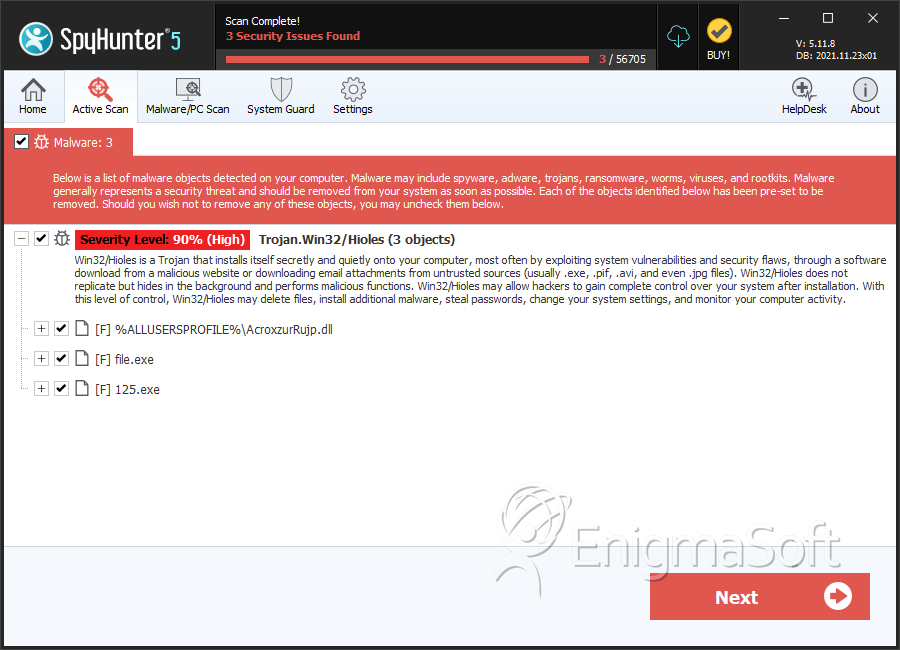
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | AcroxzurRujp.dll | e86a7c27b01397f818bc342fce3e9024 | 1 |
| 2. | %AppData%\svchost.exe | ||
| 3. | %TEMP%\svchost.exe | ||
| 4. | %AppData%\"UjharyAjsigc.dll" | ||
| 5. | %AppData%\kb.exe (for example, "kb291709.exe") | ||
| 6. | %TEMP%\kb.exe (for example, "kb291709.exe") | ||
| 7. | %windir%\System32\"UjharyAjsigc.dll" | ||
| 8. | file.exe | 093ba818b0282fa5701bdd5df3f66843 | 0 |
| 9. | file.exe | 0710873cbb938be3baf0dfe7ab74d82c | 0 |
| 10. | file.exe | 2bc9b7ca57496f3a23f12b1f7c23c365 | 0 |
| 11. | 125.exe | 051f562666fee70d9cd7dced1d8a2439 | 0 |

