WAPageViewer Ads
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 9,962 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 8,242 |
| First Seen: | September 18, 2015 |
| Last Seen: | February 2, 2026 |
| OS(es) Affected: | Windows |
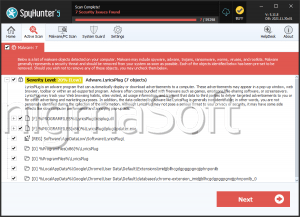
The WAPageViewer program may be promoted to you as an advanced EPUB, MOBI and PDF file viewer, but it is adware that might redirect you to phishing pages and slow down your PC. Security investigators report that the WAPageViewer adware may add a scheduled task in Windows named VSProtect to ensure its operations when you log on. Additionally, the WAPageViewer adware may change your DNS and proxy settings to reroute your Internet traffic through the servers of advertisers. The WAPageViewer adware might show pop-up and pop-under windows to promote third-party software like OfferMosquito and PlusHD. As stated above, the WAPageViewer adware may appear as VSProtect and attach a plug-in to your Internet browsers. The WAPageViewer name is just a front for the Visual Protect Service that would work in your Windows background and may block the native ads on Amazon, Best Buy and eBay. Computer users should note that the adware-powered Visual Protect Service process may utilize Web storage data, session cookies and read your Internet browsing history to facilitate the display of related marketing content. The WAPageViewer adware could be found in the Program Files directory and may have a separate auto-recovery module installed in the hidden AppData folder to make its manual removal difficult for users. The assistance of a reputable anti-spyware solution can purge the WAPageViewer adware and its associated files securely.
Table of Contents
Analysis Report
General information
| Family Name: | Adware.DealPly.AAI |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
51333bd7eeeea7534294e8e6aea12e73
SHA1:
0fc09675cc93efbaff9c3f9bfeece803a0074d3b
File Size:
2.16 MB, 2159104 bytes
|
|
MD5:
ae2662e1eafa59f46cc57049f88b4347
SHA1:
2fa54f78f6b244f24b986e80fe4e7ce6657cccb9
File Size:
2.00 MB, 2000384 bytes
|
|
MD5:
6b0d164368012e3ac1babc2b05d1a0cb
SHA1:
2e88d33300a3ca251398a7fa01c321e15f92ca51
SHA256:
FFE1046A9F0348DCC6683C3C55B7B92296DC92DBC5443516F20AC1D1C7EF3C30
File Size:
2.16 MB, 2163712 bytes
|
|
MD5:
7a25c685e80b28dbdd74c12ffe4e6cdc
SHA1:
3537963759d8967fb319a1aee857c7d427ddc718
SHA256:
D856F5761F6E79BD12347D11050D112A56ACFD3F150C9E3616EB232DD1237E31
File Size:
2.15 MB, 2153984 bytes
|
|
MD5:
e4d9a26b2b744c2c32d007e6fb1d2901
SHA1:
ddb55fb8072027611cbf42746d6e5def45a3bb0d
SHA256:
7A57F26F62C119455BC5A6363BB9370110C0F8AE4B5AB1D94BD0B3706BCEA274
File Size:
2.15 MB, 2152960 bytes
|
Show More
|
MD5:
af749fdb4c364d4bb49b5f3a305d4003
SHA1:
5cebaa444fc694b08a556977c06b4b7f33dd9b93
SHA256:
6F86976BB10A71F7D57D41CDB487A80E125102F56048C1DFC36D3069A9F44005
File Size:
2.15 MB, 2151424 bytes
|
|
MD5:
7536d0f41dd93f20240a6844cd32bcb2
SHA1:
fb1d65fa8ae060649f972ca0bb1292aa97230c93
SHA256:
347F2857ECCBCD47F9E046760219B2109165864A301B0D897C548C3DF9475542
File Size:
1.96 MB, 1961984 bytes
|
|
MD5:
f0522afc7d593dbca7bb3aa5f067cd42
SHA1:
81bfe248041534d39fd342515a79ef1d2970d21b
SHA256:
891FF844CDA7DE036A25398FFC69996204A355B65683AB5662E3194AAE5611BC
File Size:
1.98 MB, 1976832 bytes
|
|
MD5:
a2251a447d0be5894b31919c9afb0b7f
SHA1:
f5094aa6f8f20eb27115f6277876dd20681361f4
SHA256:
CCEC0B7D66F04571213B1FECA56ED8F1D7ACA46D68B632A8D3908DA43AEFBFC6
File Size:
2.15 MB, 2152448 bytes
|
|
MD5:
8bec2dccf638ba4e452f3c76930e1000
SHA1:
231906b4d26ebffd1d9b0c286776ac85d4a4a06e
SHA256:
0DF1B40F57E926F2FE95C233AE62ADCF44CFE41428A1B5D95B03C789C5D39590
File Size:
1.96 MB, 1963520 bytes
|
|
MD5:
1cf72d192a8f6e014720b72b4c93aab2
SHA1:
b195f14f3659d59d868cefdfe33359b488c3bde2
SHA256:
1BC1CE5E63D9FB42006CB8A2D6C0B05A8489CD61922CC51DBA40E02066AAF249
File Size:
1.99 MB, 1988608 bytes
|
|
MD5:
c57bbfce54a8fb33dbacfcc4da8c878a
SHA1:
9b754b195a8802fbdd99836cb508c2c6d61d97f9
SHA256:
7E9998250620B762105BB5850BA2BAFB0EB23231FCD90D02BD48F1215CCECCBD
File Size:
2.13 MB, 2125312 bytes
|
|
MD5:
55b3c3084cd67b579ff244b46d9224b2
SHA1:
ff2e7b48d0ff21cb724eb88cfc619301a1af6801
SHA256:
06FBBC2C343FDCCE0AA6C6708D04F21C4710600699EB1D880E620C3B5158C1F8
File Size:
1.98 MB, 1981440 bytes
|
|
MD5:
f88f0cc7b6ff55a2c5c77b076154ad9a
SHA1:
482861a757de7f51d8c2a28ddee326df5b131a97
SHA256:
5D8A45C3103299CBFC46473974A1C5393A7A577F2F079B8F68FFC8701BE2FB4B
File Size:
2.14 MB, 2138624 bytes
|
|
MD5:
2a34e64160c4abddc01acab092da3c33
SHA1:
266acf167761f064d3b4add5c33b6031a1a7b8c7
SHA256:
EB498B69CF90F6283B9FCF5C1F4AEE860573F39F7CDEB7DD7E00F4676CC816F5
File Size:
1.98 MB, 1978880 bytes
|
|
MD5:
3160c554ee32f53be57fe86f05d1cf45
SHA1:
9366b02c54a8a19c9c8963a92c49f9ec8b8c3d25
SHA256:
E3FF4B784C726A9DD12765230C1F06AB9528696DFBEA10EC954B76AB63C4A1A1
File Size:
2.16 MB, 2161152 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Legal Trademarks |
|
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- 2+ executable sections
- No Version Info
- VirtualQueryEx
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 5,608 |
|---|---|
| Potentially Malicious Blocks: | 0 |
| Whitelisted Blocks: | 5,567 |
| Unknown Blocks: | 41 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Banker.AM
- Banker.RF
- DealPly.AS
- DealPly.ASB
- Delf.OD
Show More
- Delf.ODB
- Filecoder.RR
- Installmonstr.EC
- MSIL.Agent.FG
- MyDoom.A
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| User Data Access |
|