Virus.AutoRun.fb
Table of Contents
Aliases
11 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Sophos | Mal/DiskNite-A |
| Prevx1 | Heuristic: Suspicious File With Covert Attributes |
| McAfee | Generic VB.b |
| F-Secure | Virus.Win32.AutoRun.fb |
| eTrust-Vet | Win32/VMalum.JYO |
| CAT-QuickHeal | Worm.AutoRun.fb |
| BitDefender | Trojan.VB.NIM |
| AVG | Worm/VB.BVK |
| Avast | INF:DiskKnight |
| AntiVir | Worm/Autorun.X.1 |
| AhnLab-V3 | Win32/AutoRun.worm.126976 |
SpyHunter Detects & Remove Virus.AutoRun.fb
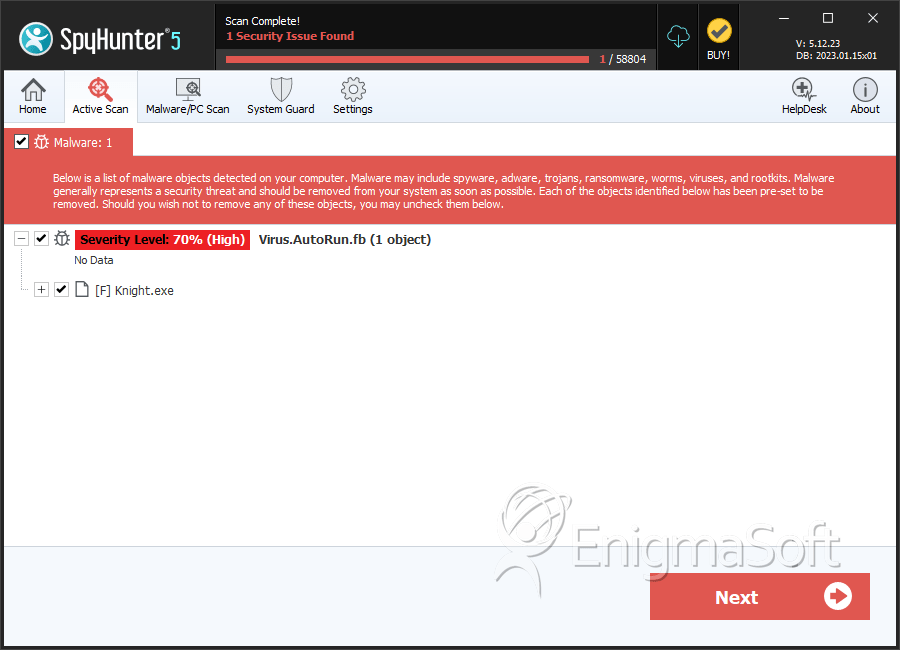
File System Details
Virus.AutoRun.fb may create the following file(s):
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Knight.exe | ac0408d0daff20338a32e6bceafceece | 0 |
Analysis Report
General information
| Family Name: | Trojan.Autorun.FB |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
89eafdaa5f800e88c22cd36ac303fda2
SHA1:
22942533f8c9f11142f9b09048280815933887a5
SHA256:
F2A071371F59AA8C522BB2A9701BDBB3D887E127DFC6DD7DE4100CEDE1584DBF
File Size:
1.99 MB, 1992704 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have resources
- File doesn't have security information
- File has TLS information
- File is 64-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Traits
- GetConsoleWindow
- No Version Info
- x64
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 12,541 |
|---|---|
| Potentially Malicious Blocks: | 1,318 |
| Whitelisted Blocks: | 11,207 |
| Unknown Blocks: | 16 |
Visual Map
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
x
x
x
x
x
x
0
?
0
0
0
x
x
x
0
x
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
0
0
x
x
x
x
x
x
x
x
x
x
x
x
0
0
?
x
x
?
?
?
?
?
?
?
?
?
?
?
?
x
x
0
?
0
0
0
0
0
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
0
x
x
x
x
x
x
x
x
x
0
x
x
x
0
0
x
x
0
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
0
0
x
x
x
x
x
x
x
x
0
x
0
0
x
0
x
x
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
0
x
x
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
0
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
0
x
x
1
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
0
x
0
x
x
x
x
x
x
x
x
x
0
x
0
x
x
x
x
x
x
x
x
x
x
0
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
0
x
0
x
0
x
x
x
x
x
0
x
x
0
0
0
x
0
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
0
0
x
x
x
x
x
x
x
0
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
0
x
x
0
0
0
0
0
0
x
x
x
x
x
x
x
0
0
0
x
x
x
x
x
x
x
x
x
x
x
x
0
0
0
0
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
0
x
x
x
x
0
x
x
x
0
x
x
x
x
x
0
x
x
x
x
0
x
0
x
x
x
0
0
0
0
x
x
x
x
0
0
0
x
0
x
x
x
x
x
x
x
x
x
x
0
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
x
0
0
x
0
0
x
0
x
x
0
0
x
0
0
x
0
0
x
0
0
0
x
x
0
0
0
0
x
0
0
0
x
0
0
x
0
0
x
0
0
0
x
0
0
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
0
0
0
0
0
0
0
x
0
0
x
0
x
x
x
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
0
x
0
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
0
x
0
x
0
x
x
x
x
0
x
0
x
x
0
0
0
0
0
x
0
x
x
0
0
0
x
0
x
0
0
x
x
x
x
0
x
x
0
x
0
0
0
0
x
x
0
x
0
x
0
0
x
0
x
0
x
0
0
x
0
x
0
x
0
x
0
x
x
x
x
0
x
0
x
0
0
0
x
0
0
x
x
x
x
0
0
x
0
0
x
x
0
x
x
x
x
x
0
x
x
0
x
x
x
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
0
0
x
0
0
x
0
0
x
x
x
0
0
x
x
0
x
x
0
0
0
0
x
x
x
0
0
0
0
x
x
x
0
0
x
x
0
0
0
x
x
x
x
0
x
x
0
0
0
0
x
x
x
x
x
x
0
x
x
x
x
x
0
x
x
0
x
x
x
0
0
x
x
x
0
x
x
0
0
x
0
0
x
x
0
0
0
0
x
x
0
0
0
0
0
0
0
0
x
0
0
x
0
x
x
0
x
0
x
x
0
0
0
0
x
0
x
0
0
x
0
0
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
x
0
0
0
0
x
0
0
0
0
0
0
x
0
x
0
x
x
0
0
x
x
0
0
x
x
x
x
x
0
x
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
0
x
x
x
x
x
x
x
0
x
x
0
0
0
0
0
0
0
0
x
0
x
x
x
0
0
0
0
x
x
0
x
x
x
x
x
0
x
x
x
0
x
0
x
x
x
x
x
0
x
x
x
x
0
x
0
x
x
0
0
0
x
0
0
0
x
x
0
0
0
x
0
x
0
x
x
x
x
x
0
0
0
0
0
0
x
0
0
0
0
x
0
0
0
x
0
0
0
x
0
0
0
0
0
0
0
0
0
0
0
x
0
0
0
x
0
0
x
x
0
0
0
x
0
x
0
x
x
x
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
x
0
0
0
0
0
0
0
0
x
x
0
0
0
x
x
x
0
0
0
0
0
0
0
0
0
x
x
0
0
0
0
0
x
0
0
x
x
0
0
0
x
x
0
x
0
x
x
0
0
0
0
0
x
0
0
0
0
x
x
0
0
0
0
x
x
0
0
x
0
x
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
...
Data truncated
0 - Probable Safe Block
? - Unknown Block
x - Potentially Malicious Block
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Autorun.FB
- Shellcode.BP
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| Keyboard Access |
|
| Anti Debug |
|
| User Data Access |
|
