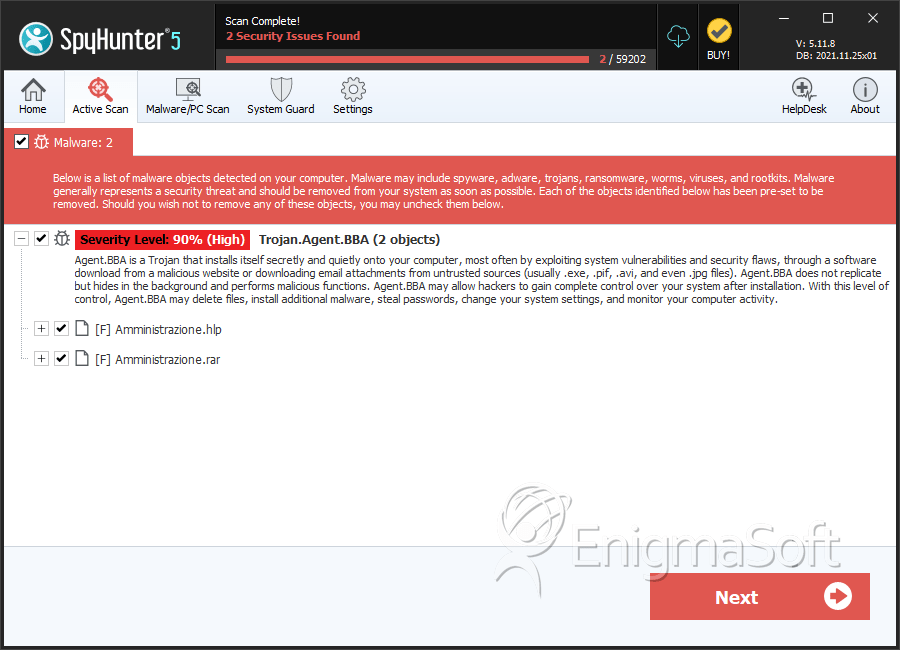
Troj/HlpDrp-B
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 57 |
| First Seen: | September 11, 2012 |
| Last Seen: | October 26, 2022 |
| OS(es) Affected: | Windows |
Troj/HlpDrp-B is a malicious file named Amministrazione.hlp (the Italian word for 'Administration'). Do not be misled by the HLP extension. While files that have this extension are normal Windows Help files, criminals can alter these kinds of files in order to install malware on the victim's computer. Troj/HlpDrp-B is one of these kinds of booby-trapped HLP files that, when opened, will install a dangerous malware infection on the victim's computer. First detected in August of 2012, the Troj/HlpDrp-B file is installed on the victim's computer via a combination of social engineering and malware tactics. ESG security researchers advise computer users to be suspicious of HLP files, especially if they are accompanied by suspicious error messages.
Table of Contents
How the Troj/HlpDrp-B Amministrazione.HLP Scam Works
Criminals use social engineering tactics to scam inexperienced computer users into opening Troj/HlpDrp-B and installing the malware component included in this innocuous HLP file. When the file is opened, an error message is displayed. This error message reads:
Help could not read the current Help file.
Make sure there are no errors on the disk, or if the file is on a network drive, that the server is active. (163)
However, while the victim is distracted by this error message, the Troj/HlpDrp-B Trojan will drop a malicious executable file on the victim's computer. This file is named Windows Security Center.exe and is detected as Troj/DarkDrp-A or Mal/DarkDrp-AT. This executable, in turn, creates a malicious DLL file named RECYCLER.DLL. This malicious DLL file is detected as Troj/Agent-OVJ or as Mal/DarkShell-A. This DLL file is actually a keylogger, a malware infection designed to track all keys pressed on the infected computer's keyboard.
Understanding the Troj/HlpDrp-B Attack
The DLL component in this malware attack is part of the infamous DarkShell Trojan, which is closely associated with a dangerous botnet known as GhostNet. The goal of the Troj/HlpDrp-B attack is to install the keylogger component in the victim's computer. Once installed, it will store all keystrokes detected on the infected computer in the UserData.dat file, located in the Application Data directory in Documents and Settings. Once installed, the DLL component will attempt to send the data it captures to a remote server, a domain named images.zyns.com that has been closely associated with various malware attacks. To prevent Troj/HlpDrp-B infections, ESG security researchers advise computer users to be careful when handling HLP files. As you can see, these can be used to deliver malware. Troj/HlpDrp-B in particular jeopardizes your privacy and can place your banking accounts and other personal information at risk.
SpyHunter Detects & Remove Troj/HlpDrp-B
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | RECYCLER.DLL | ||
| 2. | Windows Security Center.exe | ||
| 3. | Help could not read the current Help file. | ||
| 4. | \Documents and Settings\username\Local Settings\Application Data\UserData.dat | ||
| 5. | Make sure there are no errors on the disk, or if the file is on a network drive, that the server is active. (163) | ||
| 6. | Amministrazione.hlp | ff05577e9f26181bce7bceb9defb5534 | 0 |
| 7. | Amministrazione.rar | bc045fd0478d3a26054bea6a70919b2d | 0 |

