Troj/Bredo-ZT
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 32 |
| First Seen: | June 27, 2012 |
| Last Seen: | December 13, 2022 |
| OS(es) Affected: | Windows |
A widespread spam email campaign is responsible for numerous infections with the Troj/Bredo-ZT Trojan. This spam email campaign will usually claim in the subject line that it contains information of a 'Wire Transfer'. It uses spoofed email addresses in order to make the victim believe that this supposed wire transfer is coming from a trusted source, such as LinkedIn or various online services. This message will contain a file attachment that will actually install Troj/Bredo-ZT on the victim's computer system when it is opened. ESG security researchers strongly advise against opening spam attachments and to keep your anti-spam filter fully up-to-date to make sure that these kinds of malicious email messages do not make it into your inbox in the first place.
Troj/Bredo-ZT itself is a downloader Trojan that is designed to infiltrate the victim's computer rapidly after the first contact, install other malware, and then delete itself in order to prevent PC security researchers from analyzing it in order to understand malware attacks better. When the victim opens the file attachment in the malicious email message described above, Troj/Bredo-ZT will be launched automatically. In some cases, an actual document resembling a wire transfer report may be opened in order to distract the victim while Troj/Bredo-ZT does its dirty work in the background. ESG malware researchers have observed the following process in malware very similar to Troj/Bredo-ZT:
- Troj/Bredo-ZT will establish a backdoor into the victim's computer system. A backdoor is simply an unauthorized hole in the victim's computer's security that can be used to send out and receive data while bypassing the victim's security software. Much like an open physical backdoor can allow a robber to enter and exit a building without being detected, a backdoor in a computer's security allows criminals to gain unauthorized access to the infected computer system.
- Using the installed backdoor, Troj/Bredo-ZT will connect to a remote server. It will relay basic information on the infected computer system, such as IP address, web browser and operating system version, and then download other malware.
- Once Troj/Bredo-ZT has downloaded and installed other malware, the Troj/Bredo-ZT will delete all of its files in order to complicate detection and prevention of this malware attack.
SpyHunter Detects & Remove Troj/Bredo-ZT
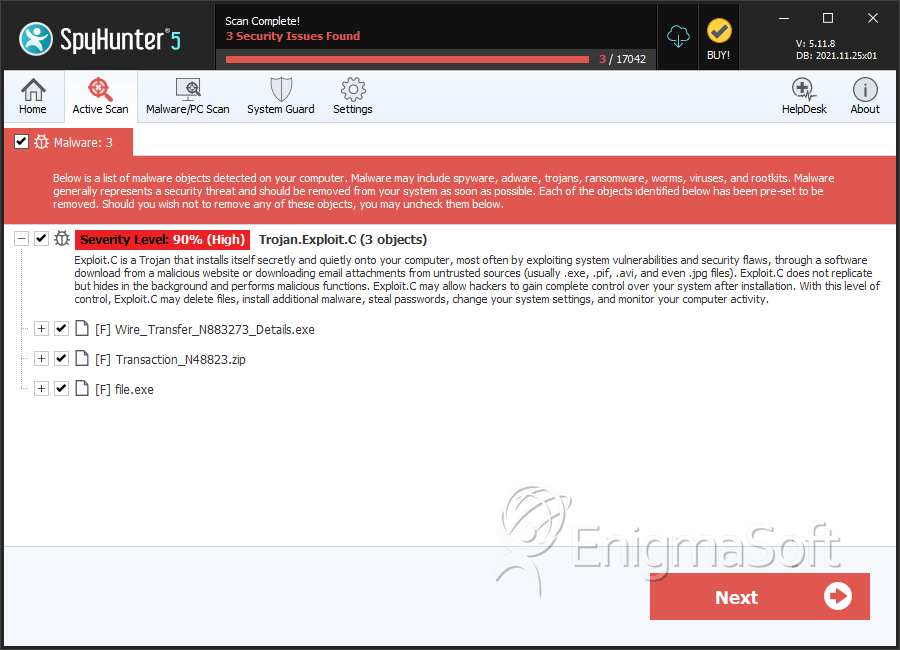
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Wire_Transfer_N883273_Details.exe | a0fb84626eb64b273cdaf802dd09451e | 0 |
| 2. | Transaction_N48823.zip | a3f5df415903a755a7f385a238d53b8e | 0 |
| 3. | file.exe | 40eac511eb5e5d9b71e768d3d3d25602 | 0 |
| 4. | file.exe | 8e6bf45bbdfbbd5d4082f8bbc8a236a0 | 0 |
| 5. | file.exe | aaf1b4500c6443ab9b52e55bc21f2266 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.