Troj/BredoZp-GY
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 11,320 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 1,939 |
| First Seen: | December 6, 2011 |
| Last Seen: | February 4, 2026 |
| OS(es) Affected: | Windows |
The term Troj/BredoZp-GY is used to refer to a malicious compressed file in ZIP format that is attached to a phishing email claiming to notify its victim to update his/her Adobe products. The Troj/BredoZp-GY file will usually be included in a malicious email that claims to contain upgrades for Adobe X Suite Advanced and Adobe Reader. While these emails contain email addresses that have spoofed the addresses for Adobe's website, they are in reality designed to infect your computer with the Zeus Trojan through to use of the Troj/BredoZp-GY malicious email attachment. Once installed, the Zeus Trojan can allow a criminal to take control of your computer system and to gain access to your online banking accounts and personal information. While it may be obvious to more experienced computer users that Adobe is unlikely to deliver its updates in this way, inexperienced computer users may fall for this scam and download the Troj/BredoZp-GY attachment. This is why ESG security researchers recommend teaching your co-workers, employees and family members about basic computer safety measures. While a strong anti-malware program is recommended, most malware infections can be prevented using common sense and following basic safe online behavior.
Table of Contents
Taking a Look at Troj/BredoZp-GY’s Malicious Email
The email which contains the Troj/BredoZp-GY malware infection will usually have a subject line claiming that it contains a critical software update, followed by a random number. It will start by addressing you with 'Hello dear,' which does not sound natural and should immediately set off red flags as to the authenticity of this email message. It then goes on to list some of the benefits of this fake update. Finally, it urges the victim to open the attached file in order to 'upgrade and enhance' his work , productivity and Adobe products. For added authenticity, it will contain a random tracking number and all sorts of legalese to make it seem that this message is actually from Adobe Systems. Each one of these email messages containing the Troj/BredoZp-GY attachment is different from the other, changing the random numbers and the Troj/BredoZp-GY file's name. Taking a look at the attachment in ZIP format reveal a file named 'Adobe Systems Software Critical Update Dec 2011.exe' which is really an installation for the Zeus Trojan. Needless to say, ESG security researchers strongly recommend that you do not download this email attachment attachment and under no circumstances open this executable file.
SpyHunter Detects & Remove Troj/BredoZp-GY
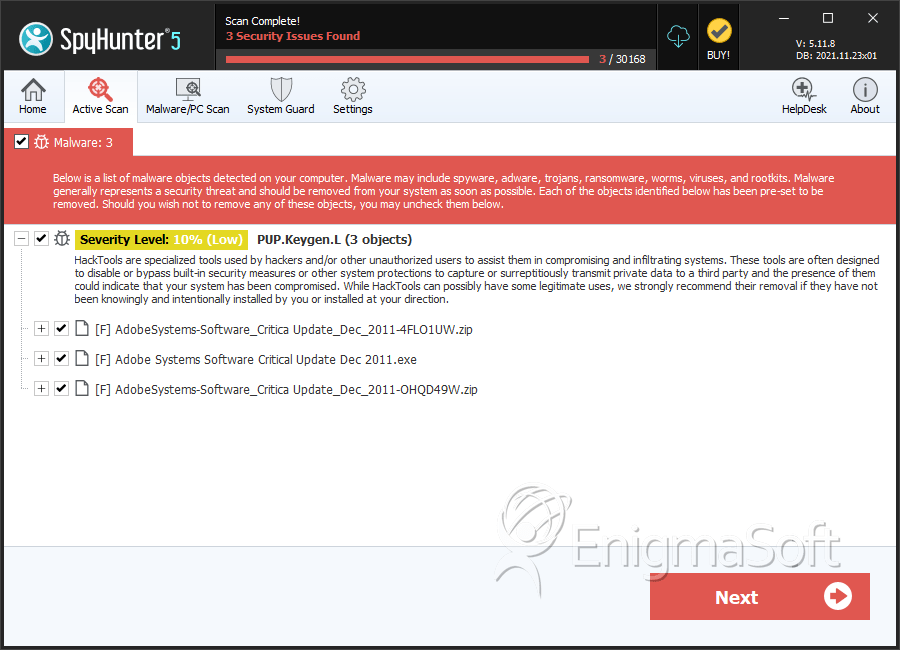
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | AdobeSystems-Software_Critica Update_Dec_2011-4FLO1UW.zip | 4d9640bf26e54efcaba882eed987c07a | 0 |
| 2. | Adobe Systems Software Critical Update Dec 2011.exe | 52b0e4177c20b6df8d7b502a474f4a7e | 0 |
| 3. | AdobeSystems-Software_Critica Update_Dec_2011-OHQD49W.zip | 730981f0fdc9f9e607003407b1178508 | 0 |
Analysis Report
General information
| Family Name: | PUP.Keygen.L |
|---|---|
| Packers: | UPX! |
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
7d23b8bfb683b74bbad1acc9491bff52
SHA1:
fa358cb6b8b8391192ecbb06cd6af43366f403c1
SHA256:
6FB7B263DE10CACDBCADB434B836D3FC81D8645F367CADB73FACDAC537809320
File Size:
96.77 KB, 96768 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has been packed
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.File Traits
- HighEntropy
- No Version Info
- packed
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 442 |
|---|---|
| Potentially Malicious Blocks: | 38 |
| Whitelisted Blocks: | 399 |
| Unknown Blocks: | 5 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block