Troj/Bredo-VV
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
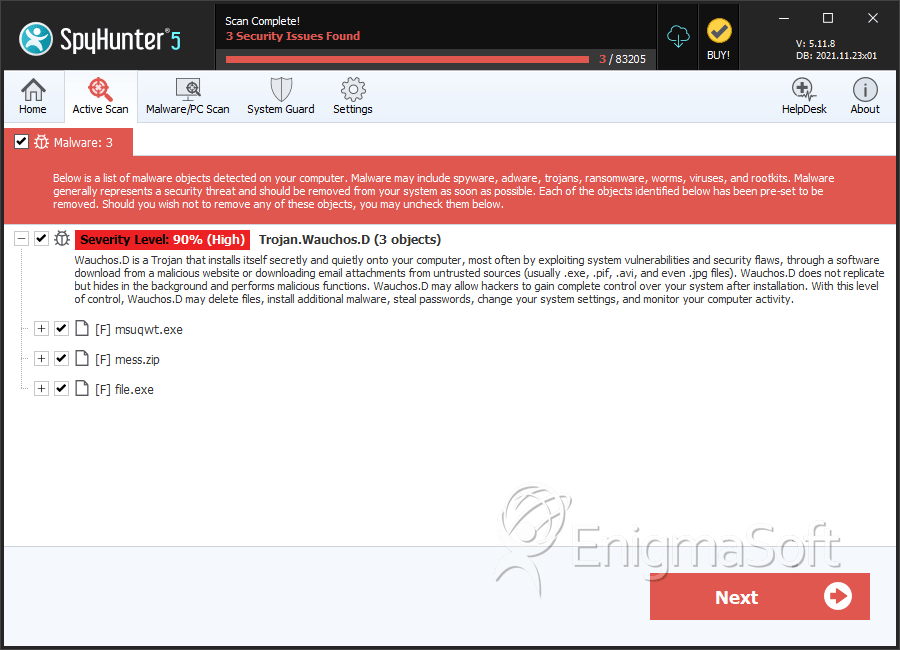
| Threat Level: | 90 % (High) |
| Infected Computers: | 3 |
| First Seen: | April 23, 2012 |
| Last Seen: | November 17, 2021 |
| OS(es) Affected: | Windows |
ESG security researchers are well acquainted with the Troj/Bredo-VV Trojan, a dangerous malware invader that allows criminals to install other threats on the infected computer. It seems that criminals are attempting to distribute this Trojan through a spam email campaign that uses classic social engineering tactics in order to carry out its attack. Basically, these emails contain a variety of messages and subject lines, all designed to make the victim believe that they contain a picture that is important in some way to the victim. These malicious emails claim that the supposed picture is included in a ZIP file attached to the email. This ZIP file, named IMG0893.zip, actually contains Troj/Bredo-VV infection.
The subject lines used by Troj/Bredo-VV scam range from simple messages like "RE:You HAVE to check this photo in attachment man" to comically alarming statements such as "RE:They killed your privacy man your photo is all over facebook! NAKED!" The message bodies in this malicious email will typically claim that the attached picture is in some way shocking or compromising. Of course, inexperienced computer users that fall for this scam are likely to be alarmed at the prospect of a private picture of themselves being available online, while others may simply be curious. Either way, opening the attached file is definitely a bad idea. Once infected, Troj/Bredo-VV, which has several variants, will often allow a criminal to install other malware, which can give them full control over the infected machine. If you have made the mistake of opening the scam email message mentioned above, ESG security researchers strongly recommends using a reliable anti-malware program to perform a complete scan of your computer system. Being exposed to Troj/Bredo-VV can significantly compromise your private information and online accounts, as well as the contents of your hard drive.
Table of Contents
Why Criminals Use Spam Emails to Distribute Troj/Bredo-VV
When most people imagine a hacker attempting to gain access to a target's computer system, they imagine a dramatic scene straight out of the movies – a computer screen filled with code and furious typing in an attempt to bring down the victim's defenses through brute force and ingenuity. However, reality is a bit more pragmatic. It is much more common for criminals to use social engineering (that is, lying) in order to take advantage of a computer user's ignorance or naiveté in order to convince them to download and install the malware infection themselves. While attempting to install Troj/Bredo-VV on the victim's computer system by attempting to override the victim's computer's security is possible, it is significantly more labor intensive than simply creating a scam email and convincing the victims to download and open Troj/Bredo-VV themselves.
Aliases
4 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Suspicious file |
| DrWeb | BackDoor.Andromeda.2 |
| Kaspersky | Trojan.Win32.Jorik.Androm.ba |
| F-Prot | W32/Trojan3.DLJ |
SpyHunter Detects & Remove Troj/Bredo-VV
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. |
C:\Documents and Settings\ |
||
| 2. | msuqwt.exe | 5b1e1534c828d398b0ae91820913911f | 0 |
| 3. | mess.zip | d60bfa876dc382908fbcde1c96d5b95f | 0 |
| 4. | file.exe | 7c99b75c3c8ef446ab098a1a7071c2ab | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.