TROJ_ARTIEF.DOC
There's been a spam e-mail campaign supposedly containing breaking news about a failed North Korean rocket launch. This spam email message contains a corrupt .rtf file attachment known as TROJ_ARTIEF.DOC. When opened, TROJ_ARTIEF.DOC installs the BKDR_POISON.DOC Trojan, a dangerous backdoor that allows cybercriminals to gain access to the infected computer system from a remote location. While, in theory, TROJ_ARTIEF.DOC could be used to deliver many other kinds of malware, this specific attack includes the presence of these two malware components working together to attack a computer system.
The main goal of installing a backdoor into the victim's computer seems to be to drop a keylogger into the victim's computer system. A keylogger is a kind of malware infection that can keep track of all keystrokes on the infected computer, as well as often being able to track mouse movements, take screenshots, and even use the victim's webcam while maintaining a low profile. Because of this, being exposed to the TROJ_ARTIEF.DOC means that your private information may have been compromised. If you have made the mistake of opening spam email attachments matching TROJ_ARTIEF.DOC's description, it is quite likely that there is a spy in your computer system.
Table of Contents
How TROJ_ARTIEF.DOC Attacks Your Computer System
Although TROJ_ARTIEF.DOC's name indicates that TROJ_ARTIEF.DOC is a Microsoft Word file (in DOC format), TROJ_ARTIEF.DOC is actually in RTF format. While these are usually text files that are completely harmless, TROJ_ARTIEF.DOC uses a known vulnerability in Microsoft Office which has been identified as CVE-2010-3333. This vulnerability allows TROJ_ARTIEF.DOC to execute a malicious, embedded executable file, which can then be used to circumvent the infected computer system's security and drop other malicious files onto the victim's computer system.
The TROJ_ARTIEF.DOC attack uses a tactic that is fairly common. Criminals will often send out spam email containing a breaking news story in order to pique a victim's curiosity. ESG security analysts constantly deal with these kinds of scams, which surface each time a particularly interesting story captures the public's imagination – particularly a celebrity death or an important geopolitical event. North Korea's failed missile launch, which had a strong presence in the news cycle, is an average example of the style of stories that criminals use to attack their victims. ESG malware researchers strongly advise that you only get your news from legitimate news sources, and never from suspicious, unsolicited email attachments.
SpyHunter Detects & Remove TROJ_ARTIEF.DOC
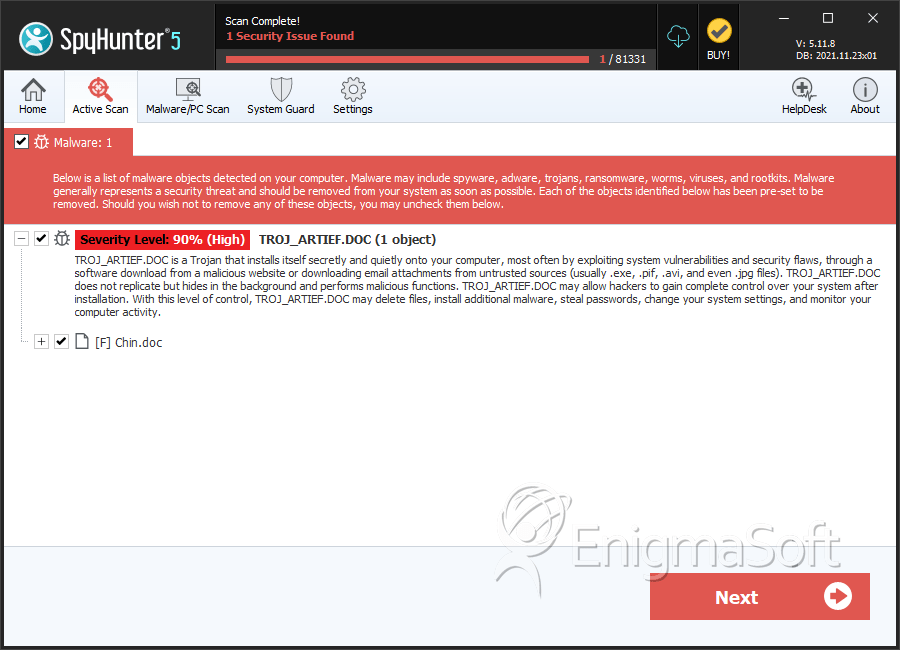
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %User Temp%\kser.exe | ||
| 2. | Chin.doc | 2a005bd66fb1e90269b2c0c8ef78ae6d | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.