Trojan:Win32/Skeeyah.A!plock
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 4,789 |
| First Seen: | March 9, 2015 |
| Last Seen: | May 19, 2023 |
| OS(es) Affected: | Windows |
The Trojan:Win32/Skeeyah.A!plock detection refers to a security breach caused by a trojan that can be instructed to download and run malware on your PC. Additionally, the Trojan:Win32/Skeeyah.A!plock can be contacted via remote servers and extract files from your system, and it may install a keylogger to steal your banking and social media user credentials. Trojans such as the Trojan:Win32/Skeeyah.A!plock are predominantly deployed via spam campaigns, and web surfers should avoid download of files in spam emails or click on links inside them. Infection with the Trojan:Win32/Skeeyah.A!plock should not be taken lightly because it can expose your OS to other malware and corrupt your installed programs. Additionally, trojans can hijack system resources and insert registry keys in Windows and lock your computer and caution is strongly advised. A reputable anti-malware shield can secure your online activities and protect you from trojans like Trojan:Win32/Skeeyah.A!plock.
Table of Contents
SpyHunter Detects & Remove Trojan:Win32/Skeeyah.A!plock
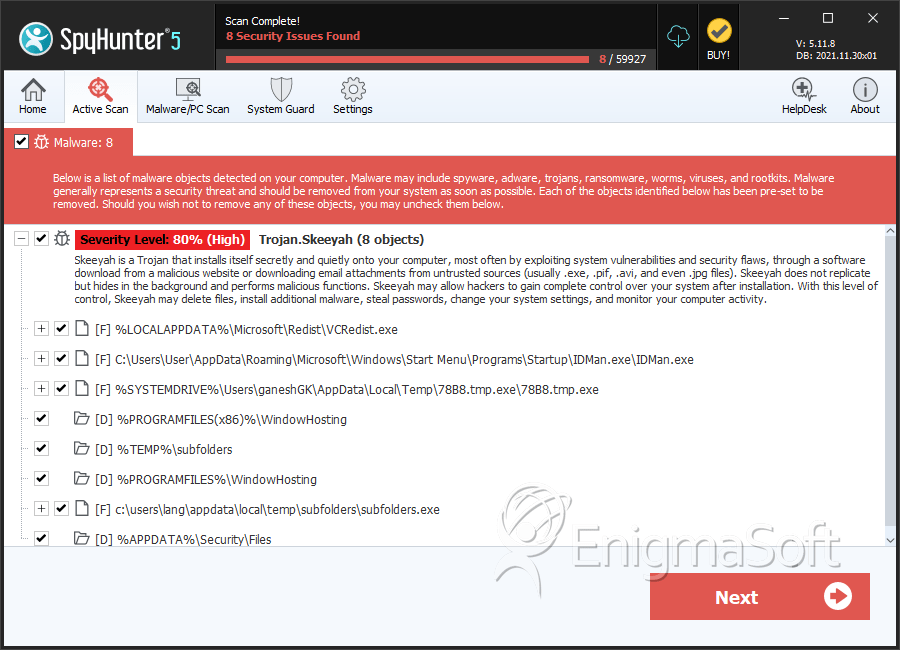
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | IDMan.exe | 19ecd2966fe29f7e9952dcd89a8bd65a | 658 |
| 2. | WSecurity.exe | 7cc54e9beedbe286c8b2a11eafaa8720 | 136 |
| 3. | 78B8.tmp.exe | 09a357acd6fdadef860bd0d416a67883 | 58 |
| 4. | VCRedist.exe | aafdd58cb2dabc2061d0a633d4d4be2f | 16 |
| 5. | JavaUpdate.exe | b1a9de8f56ba71067f7bd25e9854717d | 9 |
| 6. | subfolders.exe | 82a393779547e7c2e647c24cc6f383c3 | 8 |
| 7. | taskhost.exe | 966b978a9fb85139d305715597ac76ed | 4 |
| 8. | Security.exe | b2a0522844429d41278ae093323bd9db | 1 |
Registry Details
Directories
Trojan:Win32/Skeeyah.A!plock may create the following directory or directories:
| %APPDATA%\Security\Files |
| %APPDATA%\Security\Guard |
| %APPDATA%\Security\Logs |
| %APPDATA%\Security\Screenshots |
| %PROGRAMFILES%\WindowHosting |
| %PROGRAMFILES(x86)%\WindowHosting |
| %TEMP%\subfolders |
