Trojan.win32.genome.jdqq
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 21,622 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 3,188 |
| First Seen: | September 16, 2011 |
| Last Seen: | November 25, 2025 |
| OS(es) Affected: | Windows |
Trojan.Win32.genome.jdqq is a variant of Trojan.Win32.genome, a malicious program designed to collect vital data and send to a server and allow a hacker remote access. Trojan.Win32.genome.jdqq specifically targets systems using the Windows 32 platform and having weak or no Internet security in place. Trojans use decoys to mislead PC users and get them to click and blindly download infectious files and programs. Malware is often cloaked or hidden inside the legitimate download of freeware or shareware and may be disguised as useful adware tools:
- Jazzy toolbars
- Arbitrary search engines
- IQ tests
- Psychic readings
- Free games
- Daily horoscopes forecasts
- Contests and sweepstakes
- Free online scanners
Many victims are surprised when their anti-virus or security programs fail to stop an intrusion or properly alert them. However, many do not realize that some malware programs are stealth and can actually deactivate or destroy key anti-virus or security files, making them fail or misfire.
Trojan.Win32.genome.jdqq has skills comparable to an expert programmer and is known to make the following system changes to carry out is evil mission and defend itself against persons or tools hoping to keep this from happening:
- Run a script to find files that run or update security programs and 'delete' them. The shell of your programs may exist and will appear to run just fine and may even send you an 'all clear', when, in fact, malware is ever present and continuously attacking your system.
- Modify registry files and make an entry to loop Trojan.Win32.genome.jdqq's executable, so Trojan.Win32.genome.jdqq runs every time the system is started.
- Edit the firewall programs listing, to it approves Trojan.Win32.genome.jdqq's executable and allows Trojan.Win32.genome.jdqq to run freely.
- Edit host files to forcibly re-route web traffic to specific websites (i.e. arbitrary search engines so cybercriminals earns per-pay-click residuals or malicious websites that promote the sale of a rogue security program).
- Hijacks the web browser, so a victim cannot visit helpful websites and download a tool to detect and remove Trojan.Win32.genome.jdqq.
- Mask Trojan.Win32.genome.jdqq's files using acceptable filenames and extensions or by injecting Trojan.Win32.genome.jdqq's script into registry, system or .dll directory files.
Without your knowledge, Trojan.Win32.genome.jdqq can slip into your PC, copy and encrypt your data and deliver it to a hacker via a remote server. While a lot of tools or services might appear helpful, if they allow for exploits that can harm you, you should avoid using them. An example might be services allowing storing of vital data in browser caches. Trojans are programmed to look here first and steal passwords, usernames, PINs, certificates are anything else you stored for easy recall and access.
Trojan.Win32.genome.jdqq is able to open a port to communicate back and forth with a C&C (command and control) server and can help a hacker gain administrative control of your computer. Your computer can be turned into a zombie and a hacker can distribute a DNS attack or launch a mass email spam campaign. Unless you want a hacker using your money to buy the finest things in life, you need to move fast and remove Trojan.Win32.genome.jdqq. However, this Trojan is known to escape even the best of them and uses stealth programming tools to 'mutate', in hopes of countering combative efforts by the Internet security community. Rootkit technology also could be helping Trojan.Win32.genome.jdqq bury or camouflage Trojan.Win32.genome.jdqq's files, to elude detection and removal.
Trojan could also be hiding out in the system restore or deeper in your system, i.e. kernel, BIOS or MBR, where some anti-virus tools are not equipped to search. Unless you are highly skilled editing registry, system or .dll directory files, you should avoid chasing down Trojan.Win32.genome.jdqq for fear of deleting the wrong file and corrupting your hard drive.
Security experts recommend you rely on a reputable anti-malware tool that is equipped with an anti-rootkit component that is stealth to dig deep, find and safely remove all malware hiding out.
Until Trojan.Win32.genome.jdqq is removed along with other infectious programs that may have seeped inside, you should avoid using your Internet to conduct online banking.
Table of Contents
SpyHunter Detects & Remove Trojan.win32.genome.jdqq
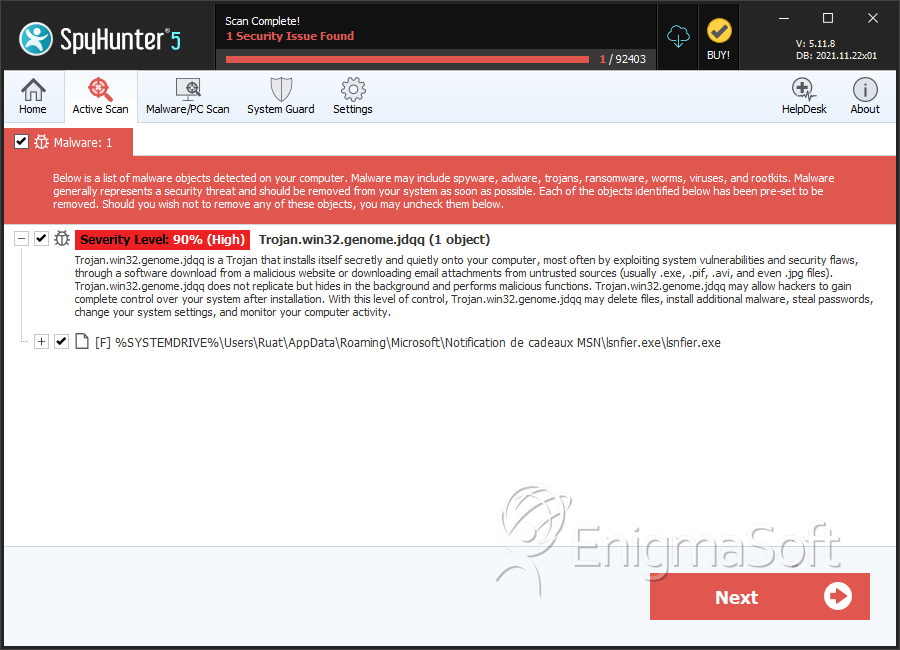
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | lsnfier.exe | bc9c9be7bb74d629362608ace470e7da | 2,415 |
| 2. | %System%\bazooka3\COMDLG32.OCX | ||
| 3. | %System%\bazooka3\Bazooka.exe | ||
| 4. | %System%\bazooka3\osenxpsuite2005.ocx |