Trojan.Shylock.B
Trojan.Shylock.B is a Trojan that opens a back door on the compromised PC and attempts to steal confidential information. Trojan.Shylock.B propagates by exploiting the Oracle Java SE Rhino Script Engine Remote Code Execution Vulnerability (CVE-2011-3544) and Oracle Java SE Remote Java Runtime Environment Code Execution Vulnerability (CVE-2012-0507). When Trojan.Shylock.B is executed, it creates the potentially malicious file. Trojan.Shylock.B may also proliferate by substituting the certain file types on removable drives and network shares. Trojan.Shylock.B then opens a back door and contacts the command-and-control (C&C) server in order to download more infected files.Trojan.Shylock.B gathers information about the corrupted machine and transfers it to the C&C server. Trojan.Shylock.B also sets up itself into a process called 'svchost.exe' in order to obtain instructions from the C&C server.
SpyHunter Detects & Remove Trojan.Shylock.B
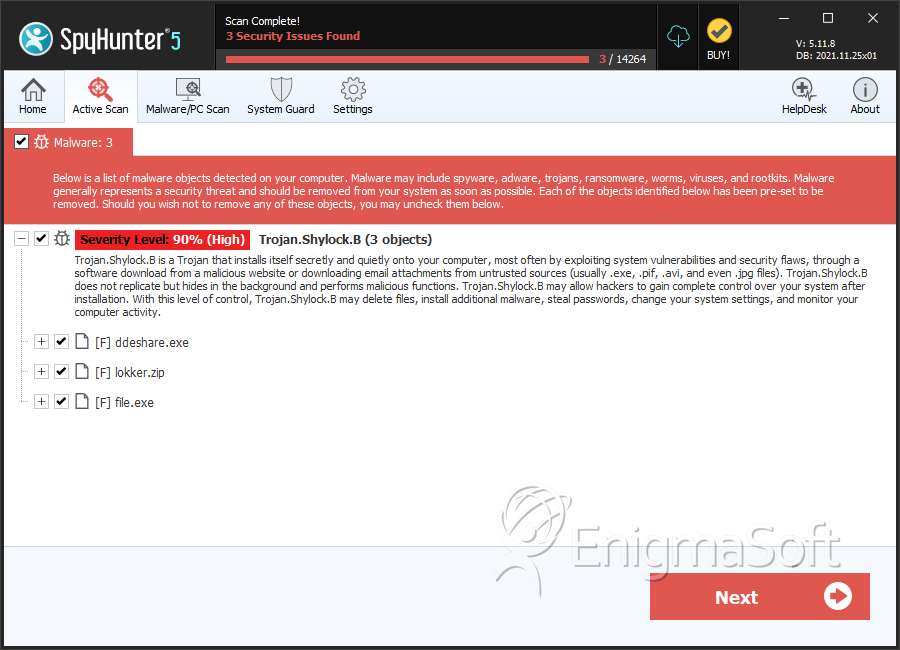
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %Temp%\[ONE LETTER].tmp.exe | ||
| 2. | Copy of [ORIGINAL FILE NAME].[EXTENSION] | ||
| 3. | [ORIGINAL FILE NAME].lnk | ||
| 4. | ddeshare.exe | 52edfd92c348938f1410eac1dc024717 | 0 |
| 5. | lokker.zip | 939a971cfc3d777d47432a2084f30aa5 | 0 |
| 6. | file.exe | 6955abf8e938bfa0f40780554e17810f | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.