Trojan.Ramage
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 23 |
| First Seen: | December 28, 2011 |
| OS(es) Affected: | Windows |
Trojan.Ramage is a dangerous backdoor Trojan that is closely related to botnet activity and Distributed Denial of Service attacks. These kinds of attacks usually involve overloading a particular server or website with requests. However, this is usually only possible by using different computers, as the number of requests must necessarily be quite high. However, there is no need the criminals to go out and buy thousands of computers. Rather, they infect computer systems with malware such as Trojan.Ramage in order to force it to do the dirty work for them.
Trojan.Ramage has several aliases, including Ontonphu and Win32/Flooder.Ramagedos. This kind of malware infection is also known as a Trojan flooder. In fact, Trojan.Ramage infection has both a backdoor element and a flooder element. The backdoor element creates a hole in the infected computer system's security which allows a criminal to gain access to the infected computer and for the Trojan to contact a remote server in order to receive its instructions. The flooder element is controlled from this remote server and is what Trojan.Ramage uses in order to flood a particular website or server with requests.
Table of Contents
What Happens When Trojan.Ramage is Installed on a Computer System?
The Trojan.Ramage malware infection is designed to infect computer systems with the Windows operating system. While Trojan.Ramage is not very complicated, Trojan.Ramage carries out its main task well; that is, connecting to a remote server, relaying information about the infected computer system, downloading its instructions and then carrying out DDoS attacks on selected targets. As part of its infection process, Trojan.Ramage will typically install its executable file in the Application Data folder, although Trojan.Ramage will often include other executable files in order to mislead the victim. These files are named after popular programs and computer components such as Intel, Netscape, Sysinternals, WinRAR, Policies, svchost or svclock. This is done so that a curious computer user will not be comfortable deleting them for fear of getting rid of a legitimate Windows component or program. As part of its installation process, Trojan.Ramage will also make dangerous changes to the Windows Registry which allows Trojan.Ramage to start up automatically, run undetected in the background, disable legitimate anti-malware software, and carry out its various malicious tasks on the infected computer. Of course, a basic part of Trojan.Ramage installation process is making the necessary changes to the infected computer's firewall in order to allow unauthorized inbound and outbound traffic.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | BackDoor.Generic14.CLFV |
| Ikarus | Backdoor.Win32.Usinec |
| AhnLab-V3 | Trojan/Win32.Agent |
| Sophos | Mal/Agent-AFJ |
| McAfee-GW-Edition | Artemis!DA301589A5CA |
| DrWeb | BackDoor.Pigeon.63400 |
| Kaspersky | Trojan.Win32.Agent.qqmc |
| AVG | SHeur3.CFPC |
| Fortinet | W32/Jorik_Lethic.DV!tr |
| Ikarus | Trojan.Win32.Jorik |
| AhnLab-V3 | Trojan/Win32.Jorik |
| AntiVir | TR/Crypt.XPACK.Gen |
| DrWeb | Trojan.DownLoad2.43630 |
| Comodo | Heur.Suspicious |
| Kaspersky | Trojan.Win32.Jorik.Lethic.dv |
SpyHunter Detects & Remove Trojan.Ramage
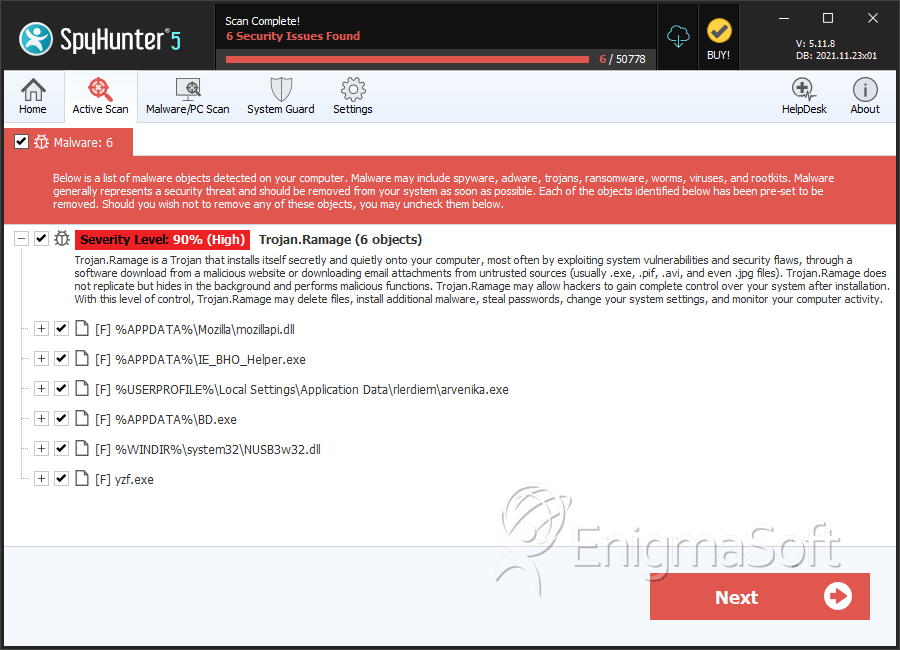
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | mozillapi.dll | 4bdb0b5d7a25cc8bc3f525334d36498e | 2 |
| 2. | IE_BHO_Helper.exe | 5ae3451b76c76c20e6fe58289bb8302c | 1 |
| 3. | arvenika.exe | 86fb10936f9e6f39ad164fa9a3e2e32c | 1 |
| 4. | BD.exe | 4e9eeea67db4c22135935a670aa0396b | 1 |
| 5. | NUSB3w32.dll | da301589a5ca17d4af751b8a161904de | 1 |
| 6. | %UserProfile%\Application Data\Netscape.exe | ||
| 7. | %Windir%\Sxc\svchost.exe | ||
| 8. | %UserProfile%\Application Data\Intel.exe | ||
| 9. | %UserProfile%\Application Data\Policies.exe | ||
| 10. | %UserProfile%\Application Data\ODBC.exe | ||
| 11. | %UserProfile%\Application Data\Sysinternals.exe | ||
| 12. | %System%\drivers\svclock.exe | ||
| 13. | %UserProfile%\Application Data\WinRAR.exe% | ||
| 14. | yzf.exe | 199057c435e1de81a5964cca20401abb | 0 |
| 15. | yzf.exe | 4fba8fbdfa83efa1ff0affc13df3552a | 0 |
| 16. | yzf.exe | 51788e27cf3bd96ad3152d295cd6aaec | 0 |
| 17. | yzf.exe | 01a764a621d1cae4764386fc7b7dd30a | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.