PowerRAT
Malware poses a significant risk to personal and organizational security. Sophisticated threats like PowerRAT highlight how quickly cybercriminals can infiltrate systems and compromise sensitive data. Protecting devices from such intrusions is paramount to maintaining privacy, security, and operational integrity. Failure to act swiftly upon detecting these threats could result in catastrophic consequences, from financial loss to identity theft.
Table of Contents
What is PowerRAT?
PowerRAT is categorized as a Remote Access Trojan (RAT), a type of threatening software that grants attackers remote control over infected devices. Once installed, it allows cybercriminals to execute commands, install additional malware, and collect sensitive data from compromised systems. This versatility makes PowerRAT especially harmful, as it may be used to exploit various vulnerabilities and achieve multiple malicious objectives.
Proliferation Tactics: Spam Email Campaigns
PowerRAT has been observed in sophisticated spam email campaigns, mainly targeting Russian-speaking users. These campaigns often employ deceptive techniques, tricking victims into downloading fraudulent attachments. Once a user engages with the email and downloads a harmful file, PowerRAT begins its infection process, often through a PowerShell loader.
These campaigns commonly use Microsoft Word documents as lures, which appear improperly formatted until the user enables compromised macros. Upon doing so, the infection chain begins, giving the attacker control over the system.
The Functionality of PowerRAT
Once active, PowerRAT performs a wide range of tasks, including:
- Collecting system information such as computer names, usernames, operating system details, and complex drive information.
- Executing commands and PowerShell scripts to extend the attacker's control over the system.
- Downloading and installing additional malicious content, including other types of trojans, ransomware, or cryptocurrency miners.
These capabilities make PowerRAT not only a threat in itself but also a facilitator of chain infections, where multiple malware variants may infiltrate a system. This increases the potential for significant damage, as attackers can shift their tactics depending on their objectives.
Potential Risks: More than Just Data Theft
The consequences of a PowerRAT infection can be severe. Beyond its ability to steal data, the Trojan's flexibility means it may be used to cause widespread harm to users' systems. Some of the most significant risks include:
- Multiple system infections: PowerRAT can install additional threats, leading to further compromises of the device.
- Data loss and privacy issues: Sensitive information, including personal data and financial records, may be harvested or exposed.
- Financial losses and identity theft: Users may face monetary consequences if attackers gain access to their banking information or other financial data.
Distribution of PowerRAT via Phishing Lures
One of the more concerning aspects of PowerRAT's distribution is its reliance on phishing lures. Attackers use official-looking documents, like Word files, to trick victims into enabling harmful macros. However, phishing isn't limited to a single technique.
The campaigns spreading PowerRAT have been facilitated through the Gophish framework, an open-source toolkit designed for phishing. Though it is intended for legitimate use in security awareness training, malicious actors have leveraged it to deceive users and spread malware.
Interestingly, these campaigns also distribute the DarkCrystal RAT (dcRAT), demonstrating the flexibility of phishing attacks in spreading multiple threats at once.
Multi-Stage Infection Chain
The infection process of PowerRAT follows a multi-stage chain. After an initial document is opened, macros trigger a PowerShell script, leading to the malware's download. This complexity ensures that detection by traditional security measures may be more difficult, as the infection is spread across different layers of interaction with the device.
Other campaigns use JavaScript-embedded files disguised as legitimate software to trick victims. For instance, users may download what appears to be a VK (a popular Russian social networking service) installer, only to trigger the infection process for a completely different RAT.
Broader Distribution Tactics
While email spam and phishing are critical components of PowerRAT's distribution, they are not the only methods. The malware may also spread through drive-by downloads, where simply visiting a compromised website is enough to trigger an infection. Additionally, PowerRAT could be distributed via:
- Malvertising: Advertisements on websites that lead to unsafe downloads.
- Dubious download channels: Third-party websites, file-sharing platforms, or pirated software sites may host infected files.
- Fake software updates: Users could be tricked into downloading malware disguised as legitimate updates for their software.
PowerRAT could have the potential to self-propagate across local networks, allowing it to infect other devices within the same environment.
Conclusion: Vigilance and Protection are Key
The presence of threats like PowerRAT underscores the need for robust cybersecurity measures. Users must remain vigilant when interacting with emails, especially those containing suspicious attachments or links. Furthermore, ensuring that systems are equipped with the latest security patches and employing advanced security solutions can help mitigate the risk of infection.
In summary, PowerRAT is a malevolent and multi-functional trojan that not only grants attackers remote control over compromised systems but also facilitates further malware infections. Its versatility, combined with sophisticated distribution methods, makes it a threat that requires immediate attention and action.
SpyHunter Detects & Remove PowerRAT
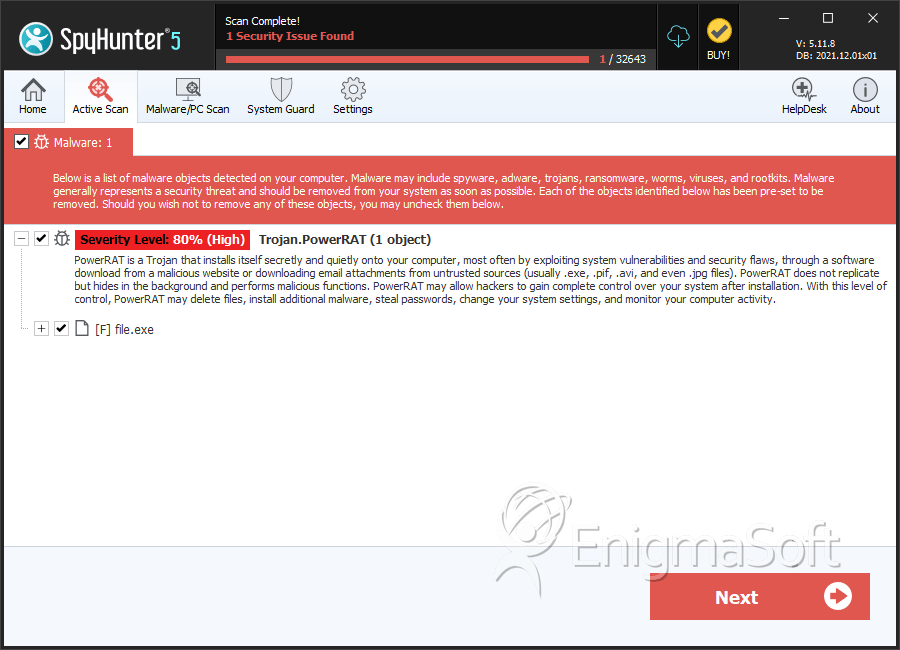
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 96989eb63e07cf96f0fbe71a9eb46899 | 0 |
