Trojan.MSIL.Injector.NEP
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 7,790 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 20,180 |
| First Seen: | November 26, 2014 |
| Last Seen: | January 13, 2026 |
| OS(es) Affected: | Windows |
Trojan.MSIL.Injector.NEP is distributed via spam emails. Also, Trojan.MSIL.Injector.NEP is part of the deployment kit used by CryptoWall ransomware. Trojan.MSIL.Injector.NEP may pretend to be harmless Microsoft Word document or a ZIP archive. This disguise is used to avoid detection and allows Trojan.MSIL.Injector.NEP to download CryptoWall on the victim's computer. Once in the system, CryptoWall ransomware will use the RSA-2048 encryption algorithm to lock access to video, document and image files. At this stage, CryptoWall instructs its victims to pay a ransom demand for retrieval of the files. Payment does not guarantee you a decryption key to decrypt your files. To avoid getting infected with Trojan.MSIL.Injector.NEP, it is recommended to not open spam emails or download suspicious files attached to them.
Table of Contents
SpyHunter Detects & Remove Trojan.MSIL.Injector.NEP
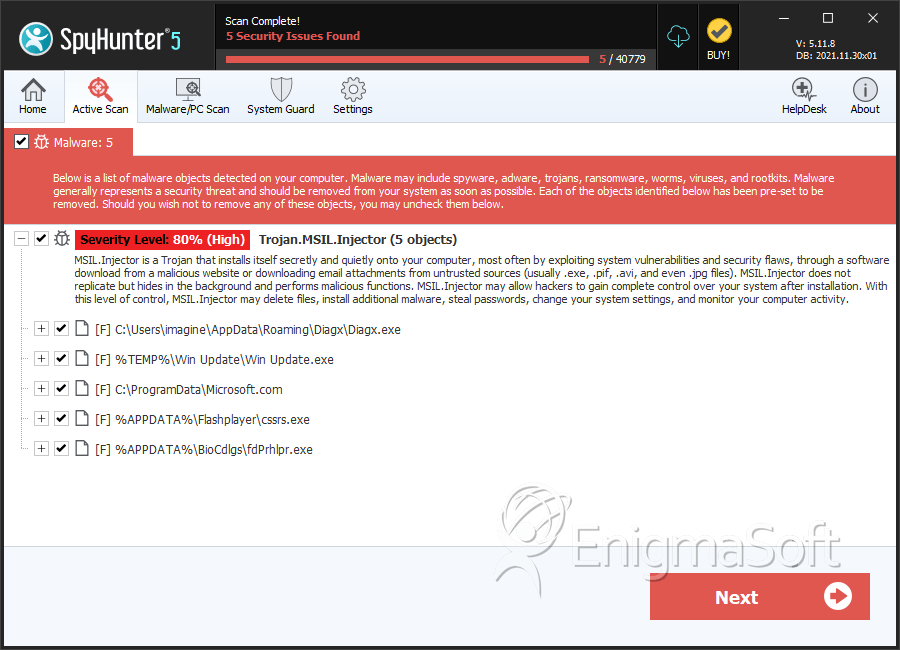
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Diagx.exe | 19492d5067392d2d2fe15ec161c7722a | 1,040 |
| 2. | Win Update.exe | 7f63ddfbd79cf30f7e057bade41d514a | 49 |
| 3. | Microsoft.com | d9016566f365b6c8d5cebc7313f7d4d5 | 46 |
| 4. | cssrs.exe | 411ef5e0cacfc3b2c0d8a22a61a3726a | 12 |
| 5. | fdPrhlpr.exe | 198d703ff2b28dba58367b5434232144 | 0 |
Registry Details
Analysis Report
General information
| Family Name: | Trojan.MSIL.Injector |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
a90a7c91f72744bd1c6fd2273a285b41
SHA1:
27f2a4f37290dc6573f8c297b593ae6c6f433e4c
File Size:
2.12 MB, 2116905 bytes
|
|
MD5:
39ba33756f13f9df5a7a7cf120b55b9b
SHA1:
9feb46e8db106bc8206e91b07dc2d48cad06b4f6
SHA256:
9DEA07F4E51D94A68DBE52D3CE49DDC776758B9E1D3719261A23E4D523409B83
File Size:
651.26 KB, 651264 bytes
|
|
MD5:
a78b51dbb7ca1d66bf2ff5fc787f30dd
SHA1:
16aab0bc72344ac6ca25fc8cb40c46cfdd7330e8
SHA256:
2F7414EACDC9BF8C158CAAAEA8A4117CE71404FFB019676D12FCEA305B57E70C
File Size:
4.45 MB, 4447816 bytes
|
|
MD5:
fad3fd6e8dec1f1b37b985c7515b63d2
SHA1:
8538305b5ac3c10164f4faa6c8ff899f689cf29a
SHA256:
B2425A52769BF77F6DC6DE59A7310478B3DB199204C112FC6723C81669A8526C
File Size:
347.05 KB, 347052 bytes
|
|
MD5:
5146c4ebf6976b707cbfb8d88833728c
SHA1:
12e5c992974ea4b1668744f45f992f2d667fb900
SHA256:
03EF846C042BA4E039261612B54D8AFF369FF9EEDA7A76FA82594B46975622A2
File Size:
9.39 MB, 9390524 bytes
|
Show More
|
MD5:
452dd2c618b8a02823fbdc7d4e17d030
SHA1:
049e588d56b9ca3b22e6be4d5990231194710d58
SHA256:
7E646188F2B4FE0DD3D4C2F817EBF274A4BDC3AA9DA70F9791C7BAD663925771
File Size:
666.11 KB, 666112 bytes
|
|
MD5:
6bfe328347cda0a7e87614d5015bb024
SHA1:
a4e4599a5d9ef8077e4d50df8f78a1bb9ece8ba2
SHA256:
888573A1B710CED190065DD070AE854253485980757385D2D9E64DF149F8AD6D
File Size:
768.36 KB, 768359 bytes
|
|
MD5:
b002a9d2b9beb6ed3f6fbd6f4dc816a9
SHA1:
7d8933bdfe82c63afc6874231a7d834969db5481
SHA256:
CC2459BC2EB7B2EAD464EB6CF52FBE9291EB937F3054F7D9AC41DCB6FC8346FA
File Size:
1.89 MB, 1887579 bytes
|
|
MD5:
101e62bdca44f60d917c17f5462aacec
SHA1:
f5b5102a3c8ca6ee7963d61127ae643b894a27b9
SHA256:
087F7114BB7CF84E9EE561D3458E33D04A256E57F39C0A4CAF8DE61733529255
File Size:
203.26 KB, 203264 bytes
|
|
MD5:
2f4615e22aef04f23fb1226ca95ed905
SHA1:
7177b860d42452c94a30d7ad3c58123861bd303a
SHA256:
02FF19FEDDC3C8704297998F546BDCE52D2AC98B9E1A51D51FF34C37F70BBA43
File Size:
7.98 MB, 7983159 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is .NET application
- File is 32-bit executable
- File is 64-bit executable
Show More
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version |
|
| Comments |
|
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Legal Trademarks | Mr: Thusitha Wijethunga |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- .NET
- .sdata
- big overlay
- dll
- HighEntropy
- NewLateBinding
- ntdll
- VirtualQueryEx
- WriteProcessMemory
- x64
Show More
- x86
- ZwQueryInformationProcess
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 7 |
|---|---|
| Potentially Malicious Blocks: | 1 |
| Whitelisted Blocks: | 2 |
| Unknown Blocks: | 4 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\is-dutjb.tmp\7d8933bdfe82c63afc6874231a7d834969db5481_0001887579.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-qkv3i.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\is-qkv3i.tmp\idp.dll | Generic Write,Read Attributes |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| User Data Access |
|
| Encryption Used |
|
| Anti Debug |
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Umqchqld\AppData\Local\Temp\is-DUTJB.tmp\7d8933bdfe82c63afc6874231a7d834969db5481_0001887579.tmp" /SL5="$30292,1019830,888320,c:\users\user\downloads\7d8933bdfe82c63afc6874231a7d834969db5481_0001887579"
|
