Trojan.Win32.LockScreen
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 716 |
| First Seen: | March 19, 2012 |
| Last Seen: | March 1, 2023 |
| OS(es) Affected: | Windows |
The Lockscreen family of malware or Trojan.Lockscreen, responsible for the International Police Association (IPA) Ransomware, FBI Moneypak ransomware and 'Votre ordinateur est bloque en raison du delit de la loi de la France’ Ransomware' infection is comprised of various Trojans designed to threaten computer users so that they will pay a ransom. Malware in the Lockscreen family is known to target computer systems in the European Union with highly genuine-looking ransomware messages. These are designed to scare inexperienced computer users into thinking that their machine has been locked by their country's main law enforcement agency or by the IPA. The Lockscreen family of malware is not particularly sophisticated or difficult to remove, but poses a significant threat to inexperienced computer users unaccustomed to dealing with ransomware attacks. If you find that a threatening message is displayed on your screen when you start up Windows, and you cannot access your Desktop or files, you may have become infected with a ransomware Trojan in the Lockscreen family. ESG security analysts recommend the use of a strong, updated anti-malware program to remove this threat permanently.
Table of Contents
An Overview of the Scam that Malware in the Lockscreen Family Uses to Steal Your Money
Basically, malware in the Lockscreen family is designed to enter a computer, detect the infected computer's IP, and then make the necessary system settings modifications to carry out its scam. This includes making changes to the Windows Registry that allow Lockscreen malware to start up automatically when the victim launches Windows as well as blocking access to Windows components such as the Task Manager or the Windows Registry Editor. Then, Trojan.Lockscreen connects to a remote server in order to download the text and graphics for a ransom message directed towards the infected computer's country, which is deduced from its IP address. The message will try to dupe the victim into paying a fine ranging from fifty to one-hundred Euros if they wish to regain control of their computer system. The message will also threaten the victim with prosecution if this fine is not paid.
Although there are many highly-sophisticated ransomware infections that have the ability to encrypt the victim's files or cause lasting damage to the infected operating system, malware in the Lockscreen family is relatively benign. The main obstacle when removing a Lockscreen family infection is actually gaining access to the infected computer's anti-malware software. To do this, you can bypass the Lockscreen family threatening message by using an alternative boot method to start up Windows.
SpyHunter Detects & Remove Trojan.Win32.LockScreen
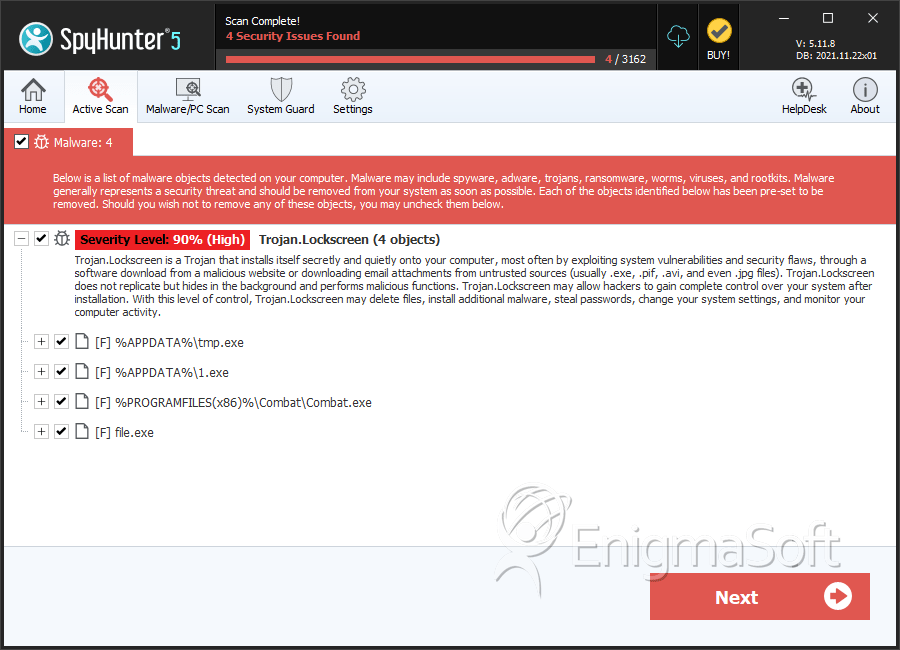
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | tmp.exe | cc38bd5181872b54c10bf1c3317fb2a2 | 689 |
| 2. | 1.exe | 403767a08cc494ea623bd407ac2b55da | 12 |
| 3. | 1.exe | 9b079876e1077eb7e74c56e8814c41a0 | 7 |
| 4. | Combat.exe | 6d7fcc24f48c0ddafe8e9c337dbca1da | 1 |
| 5. | %AppData%\Yniq\demuy.exe | ||
| 6. | %Temp%\tmp54873343.bat | ||
| 7. | %AppData%\Wigouq\anyrg.tmp | ||
| 8. | %AppData%\Wigouq\anyrg.unw | ||
| 9. | file.exe | 6D8DB0D28948A4D91A30E51C6901BBA0 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.