Trojan.Fraudrop
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 103 |
| First Seen: | August 7, 2012 |
| OS(es) Affected: | Windows |
Fraudrop is the name of a family of computer Trojans that may be employed by many threat agents that strive to compromise the security of computer networks. Trojans that are tagged as representatives of Fraudrop may be used to install other threatening programs on infected computers, and that includes ransomware, bots, Bitcoin miners, DDoS clients and viruses. The Trojan-Downloaders from the Fraudrop family of threats are associated with other threats like FreeKeylogger, Wixud Rimecud and OphionLocker that may inflict severe damages to your file system, hard drives and computer networks. Typically, Fraudrop Trojan-Downloaders are deployed as attached files to spam mail or may appear as ZIP archives, PDF and DOCX files. Most versions of the Fraudrop Trojan-Downloader are designed to connect via HTTP to predefined remote servers to download threats and ping their 'Command and Control' servers after a successful infiltration.
Network administrators may not be able to notice Internet traffic from Fraudrop right away because the majority of servers it uses to download threats are located on compromised websites that may utilize HTTPS encryption. The Fraudrop Trojan-Downloaders may hide its down landed corrupted binary in compressed folders. The operators of Fraudrop Trojans can issue commands via POST requests to infected computers to unpack and install additional threats. Most of the Trojan-Downloaders that are variants of Fraudrop are programmed to place their files in the Temp folder under the Windows installation directory to avoid early detection by security scanners. PCs that are compromised by the Fraudrop malware may run slower and exhibit interrupted Internet connection. You need to install a reputable anti-malware solution to eradicate cyber threats from the Fraudrop family of Trojan_Downloaders.
SpyHunter Detects & Remove Trojan.Fraudrop
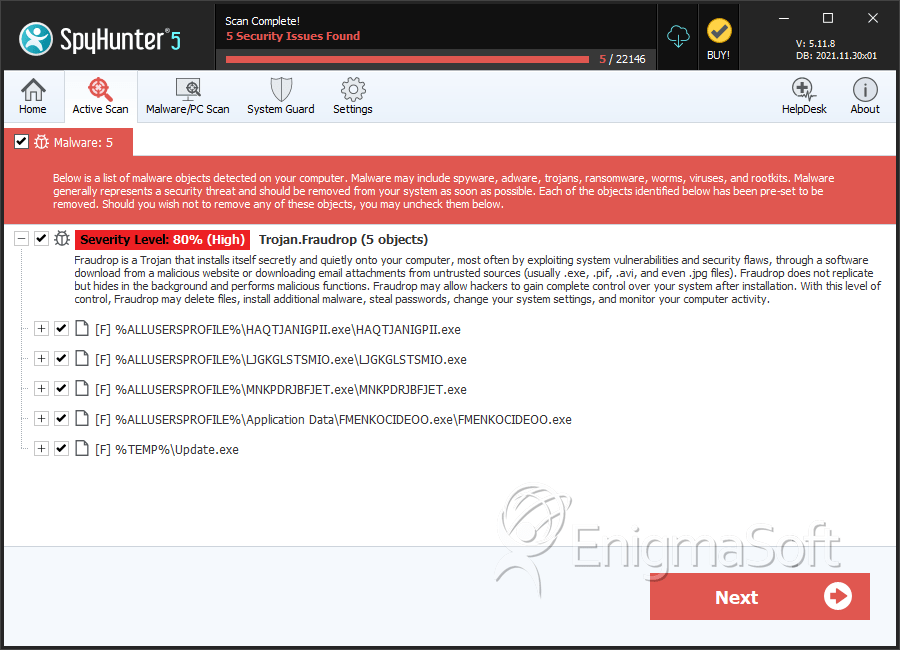
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | HAQTJANIGPII.exe | 5c1a9299aaa8871127a1ac3304619ee5 | 63 |
| 2. | LJGKGLSTSMIO.exe | 9e012beaa21413e2300572ad2468d4ed | 25 |
| 3. | MNKPDRJBFJET.exe | 7dbec606d21794cdd4981f4b33feb064 | 7 |
| 4. | FMENKOCIDEOO.exe | d9a238e87f979a7bfb7251012bda797d | 7 |
| 5. | Update.exe | 3b2e42880a70671edc93bd1783b008b0 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.