Trojan.Dropper.Dapato
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 12,982 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 6,622 |
| First Seen: | August 5, 2011 |
| Last Seen: | September 4, 2023 |
| OS(es) Affected: | Windows |
The Trojan.Dropper.Dapato program is classified as a Trojan that is programmed to show advertisements on the screen of infected users and generate Internet traffic to unreliable search engines. The Trojan.Dropper.Dapato program was reported for the first time by users in Poland, and the threat appears to target users in Central and Western Europe predominantly. Computer users may install the Trojan.Dropper.Dapato with a corrupted free software bundle, which may include adware like PubHotspot and riksware such as YTDownloader. We have detected that the Trojan.Dropper.Dapato is often found on infected computers in the company of the Vnlgp Miner, which is a legitimate program that is abused by threat authors who claim revenue from processing online payments using the hardware resources of compromised machines. The Trojan.Dropper.Dapato program can be found in:
C:\Documents and Settings\All Users\Application Data\TeamViewer_Tracer.exe
The file is likely to be hidden within the Windows Explorer. Unless you have enabled the 'Show Hidden Files' in the file manager, you mаy not spot the Trojan.Dropper.Dapato. Additionally, the Trojan is seen to create the following files in the AppData directory:
C:\Documents and Settings\All Users\Application Data\log.ewbb
C:\Documents and Settings\All Users\Application Data\log.ewbt
As stated before, the Trojan.Dropper.Dapato is programmed to generate ads and may redirects users to insecure search engines. Researchers found that the Trojan.Dropper.Dapato Trojan may exchange data packets with servers hosted on the following domains:
- 12kotov.ru
- initialpage123.com
- maniver.ru
- noblok.org
- qtipr.com
The transmissions are accomplished via a hidden instance of the default browser on your system. The Trojan.Dropper.Dapato Trojan might inject a corrupted DLL in Google Chrome and Mozilla Firefox to facilitate its operations. Moreover, the threat adds a Registry entry and a link to the Startup folder to enable its automatic start with Windows. Samples of the Trojan.Dropper.Dapato revealed that the file might come with a valid digital certificate, which may allow it to bypass the native certificate scanner on Windows 10. Computer users that are infected with the Trojan.Dropper.Dapato Trojan may notice that their browser shows pop-up advertisements and there are redirects from time to time. Extensions like Adblock Plus and uBlock Origin are unlikely to suppress the activity of the Trojan.Dropper.Dapato, and it is best to use a reliable anti-malware tool to clean your machine. AV scanners may detect files related to the Trojan.Dropper.Dapato as:
- BackDoor.Radmin.150
- HEUR/QVM07.1.4C7E.Malware.Gen
- ML.Attribute.HighConfidence
- UDS:DangerousObject.Multi.Generic
- a variant of Win32/Kryptik.FQVT
- malicious_confidence_71% (D)
- virus.win32.parite.b
Table of Contents
SpyHunter Detects & Remove Trojan.Dropper.Dapato
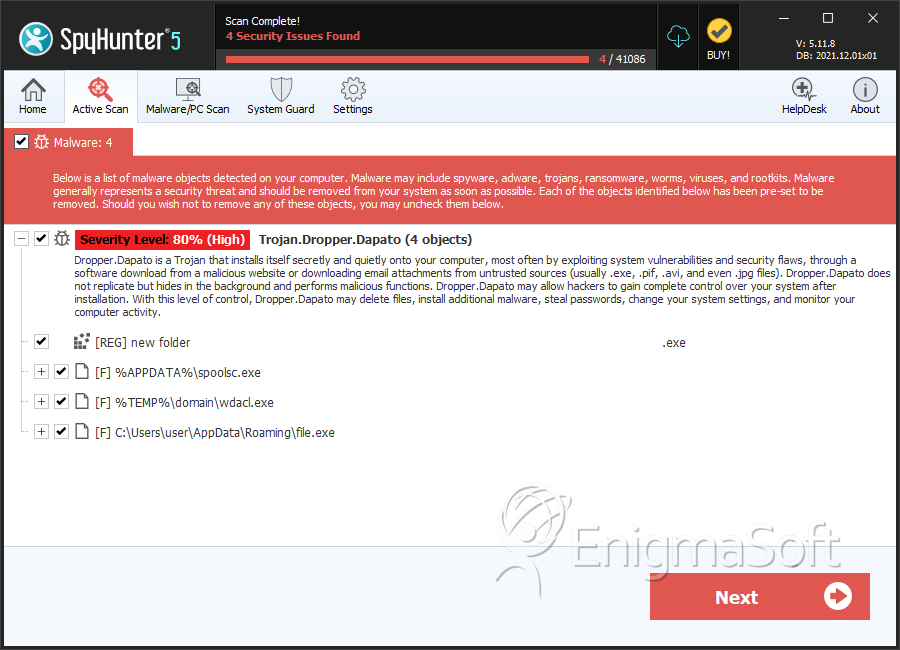
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | spoolsc.exe | 21ee45b249954072e602a7d50db6a5e3 | 25 |
| 2. | wdacl.exe | db453cc209f0577830f35203fc8c800a | 9 |
| 3. | spoolsc.exe | 0848c3bb5050da344ed0c551c98b0ba7 | 6 |
| 4. | spoolsc.exe | 2e14a731475a7e8aa4f0d3a7f52e5643 | 3 |
| 5. | wdacl.exe | 6fbd102b5a0a4753ac9cf0554324f0cd | 2 |
| 6. | spoolsc.exe | e6cde37176f0d29ce919586739f6b9b1 | 2 |
| 7. | wdacl.exe | 400c4960ae14565caacdfb6f3381fcde | 1 |
| 8. | wdacl.exe | b5eede0d712f5338bace185e6fb45261 | 1 |
| 9. | wdacl.exe | f4c07ec5d78bc4818938d3f97eaf16d5 | 1 |
| 10. | wdacl.exe | 09a652fe954b17c30a9dbae6db49837e | 1 |
| 11. | spoolsc.exe | e89906af6bee4e2f5120b4c348d86e31 | 1 |
| 12. | spoolsc.exe | 3398462231e58f8855c289cdc319f771 | 1 |
| 13. | spoolsc.exe | 2d7b8940303fa628d8b71512ba61c8b5 | 1 |
| 14. | spoolsc.exe | 5111d001f3b51e595b276e06108abf5c | 1 |
| 15. | spoolsc.exe | 3b4372705a7e7bb21a570a33a145e26b | 1 |
| 16. | file.exe | 54bad3613bdf02e3ba1375c9b047e1b6 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.