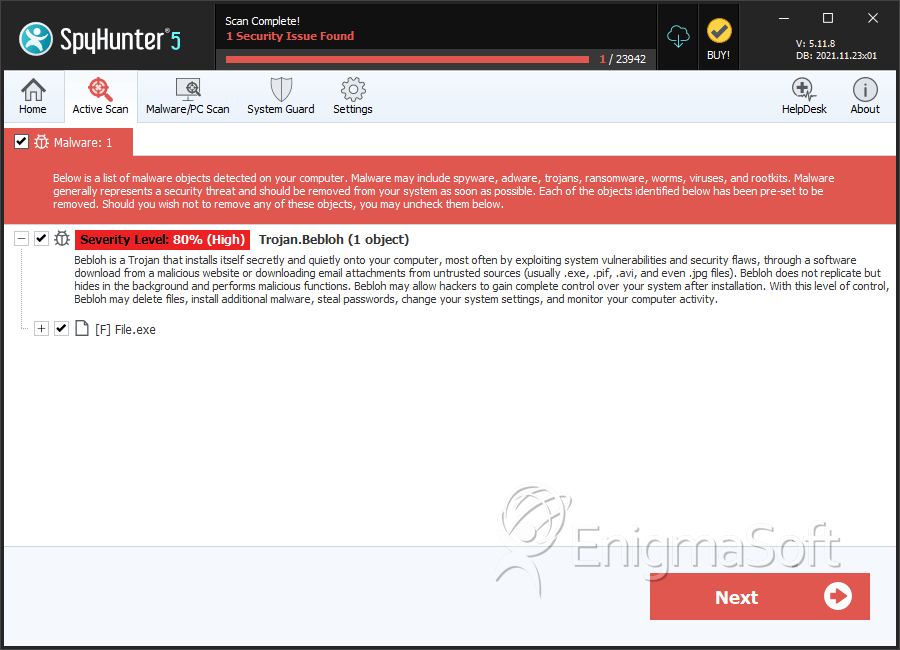
Trojan.Bebloh
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 1 |
| First Seen: | March 23, 2012 |
| OS(es) Affected: | Windows |
Bebloh is a banking Trojan that uses advanced features to collect money from inexperienced computer users. Banking Trojans like Bebloh are specifically designed to collect money from inexperienced computer users' banking accounts. In most cases, these types of Trojans do this by implanting themselves on the infected computer, waiting for the computer user to log into their online banking account. Then, the banking Trojan may intercept traffic, replace the banking website with its own fake website, log keystrokes, or carry out a number of other operations to collect the victim's username and password. Banking Trojans may also search the victim's computer and Web browser settings in order to retrieve any saved passwords or log-in information. Bebloh and other banking Trojans may be especially effective in dodging removal, which makes them particularly threatening.
Table of Contents
Bebloh has Implemented an Evasion Functionality that Makes It Harder to Track
Bebloh's developers implemented features last year that allowed Bebloh to dodge its removal far easier than before. Bebloh is not an unknown banking Trojan. Bebloh has been studied for several years. For many years, this banking Trojan had remained fairly stable. In the first half of 2013, infection rates involving Bebloh had not been particularly high. However, the changes made to Bebloh resulted in a significant increase in Bebloh infections in the second half of 2013. Today, Bebloh remains an active banking Trojan with a relatively larger share of the number of worldwide infections involving these types of Trojans. Bebloh is currently among the top three banking Trojans, a large part due to these changes made to its attack strategy.
How Bebloh Evades Detection
The main way in which Bebloh is distributed is through spam email messages. A typical threatening email message used to distribute Bebloh will show a content that appears to be a flight reservation confirmation, including an embedded link that leads to an attack website. When victims click on this link, Bebloh is downloaded and installed in the background automatically.
When creating threats, one of the issues is designing a way for the threat infection to persist on the infected computer after it is restarted. In the case of Bebloh, this threat uses advanced features to remain on the infected computer in the long term. As soon as Bebloh infects a computer, Bebloh is injected into explorer.exe, the Windows Explorer file process. Then, the original executable file containing Bebloh is deleted from the infected computer. This conceals Bebloh's origin and may be used by other threat infections. However, unlike other threats, Bebloh is not moved to another directory, and there is no autostart entry for Bebloh. This banking Trojan cannot be found on the hard disk after it has been installed. This is why conventional anti-malware programs may not be capable of detecting the presence of Bebloh merely by scanning the infected hard disk. Bebloh runs by hiding in the explorer.exe memory process, so not even a threatening file process may be detected.
When the infected computer restarts, Bebloh generates an invisible window from the explorer.exe process. This window is there to receive a Windows message named 'Windows Messages', issued before a computer shutdown. As soon as Bebloh detects that a shutdown may occur, Bebloh writes its executable file to the hard disk and creates an autostart entry directing to a randomly generated LNK file. This results in a curious fact: Bebloh is never on the infected computer's hard disk while the computer is running. Its file is written onto the hard disk right before Windows shuts down and is deleted and injected into the explorer.exe process during start-up. This makes it very difficult to detect and study Bebloh and practically impossible for signature-based threat scanners to detect this kind of threat. To deal with Bebloh, malware researchers advise the use of an advanced, reputable anti-malware program that is fully up-to-date.
SpyHunter Detects & Remove Trojan.Bebloh
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 9e3ea995e40b62adae78e93e6b30780c | 1 |
| 2. | File.exe | f4adea4a270a7474a9c19b9589102d9f | 0 |
| 3. | file.exe | cac2eaa37b36f498f29843590fca272e | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.